Archive
Ad-hoc Use of Sysinternals Utilities
If you perform any troubleshooting at all in the Windows environment you are no doubt familiar with Mark Russinovich‘s Sysinternals utilities. There is hardly a day that goes by that I don’t use one myself, and I’m not even directly involved in supporting our products!
The tools themselves are fantastic and provide a wealth of information, which is helpful not only for troubleshooting, but for learning as well. Typically you just download the tools and run them from your local system (they don’t require installation – just run them directly!). There are, however, certain times when I’m working on a customer’s machine and I find myself in need of one of these tools, and thanks to Alex Eckelberry’s post on the Sunbelt Blog I’ve learned that you can run them directly from live.sysinternals.com/tools right from the command line! For example…
As long as the system you are working on has Internet access you can use any of the tools in the suite remotely and on an ad-hoc basis.
Be sure to read Alex’s full post on the subject for more information.
Microsoft Forefront Threat Management Gateway Administrator’s Companion – Coming Soon!
Just wanted to remind everyone now that Microsoft Forefront Threat Management Gateway Beta 3 is out that the Administrator’s Companion book will be available soon!
This book is being co-authored by some of the most knowledgeable TMG experts in the world – Jim Harrison, Yuri Diogenes, Mohit Saxena, and Tom Shinder. I’ll post another reminder as soon as the book is available for pre-order.
Microsoft Leads in Security
Great article by Steve Grimes at InfoWorld on the security advances made by Microsoft.
http://www.infoworld.com/d/security-central/pigs-fly-microsoft-leads-in-security-200
: )
DNS Security Enhancements and Web Proxy Auto Discovery
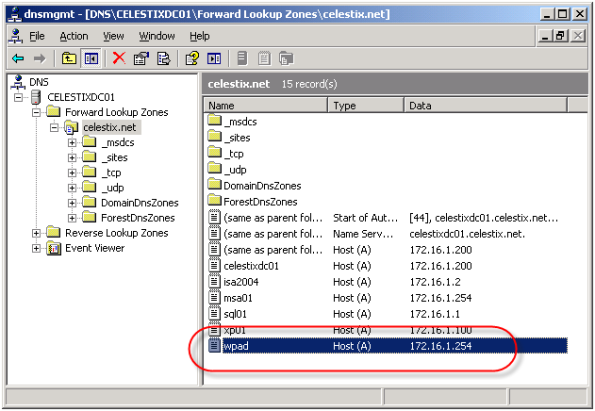
Using Web Proxy Auto Discovery (WPAD) is a simple and effective way to configure web browsers to use the ISA firewall as a proxy server. WPAD can be implemented using DNS or DHCP, with DNS being the more common of the two. For WPAD using DNS, configuration is simple and straightforward; all that is required is that you configure a host record in DNS called WPAD that resolves to the IP address of your ISA firewall’s internal network interface.
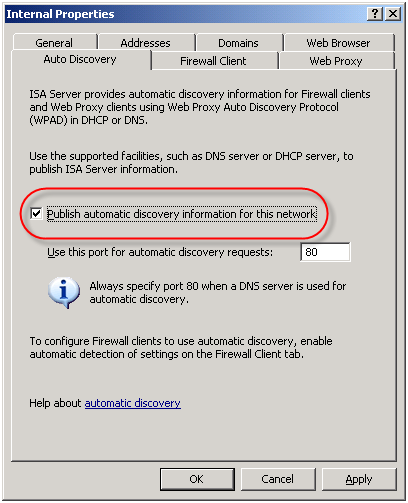
On the ISA firewall, enable the ‘Publish automatic discovery information for this network’ option on the ‘Auto Discovery’ tab for the Internal network.
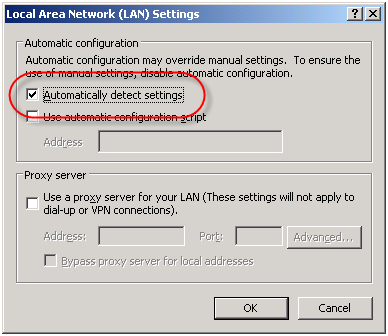
For Internet Explorer, navigate to ‘Tools/Internet Options/Connections/Lan Settings’ and select the option to ‘Automatically detect settings’ and your work is done!
Unfortunately this functionality can be easily leveraged for nefarious purposes. An attacker could create their own WPAD record (which can be accomplished simply if dynamic DNS is not configured correctly) and redirect traffic through a host that they control. From there they could have full view in to all web-based communication between a client and an Internet-based remote host.
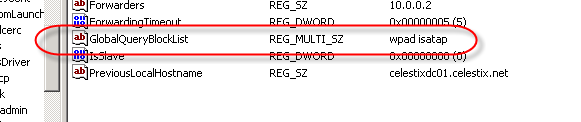
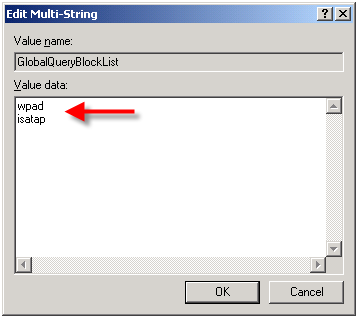
In order to address this security concern, Microsoft has made changes to the way DNS works beginning in Windows Server 2008. DNS in Windows Server 2008 now includes a feature called the global query block list. Essentially this is a list of names that the DNS server will not respond to if queried. By default this list includes two entries; WPAD and ISATAP. You can view this list by executing the following command from an elevated command prompt:
dnscmd /info /globalqueryblocklist
If you are using Windows Server 2008 DNS and you wish to leverage DNS WPAD functionality you must instruct the DNS server to respond to these requests. Simply creating the DNS record by itself is not enough. On Windows Server 2008 you can configure WPAD by creating your DNS record as usual, then remove WPAD from the global query block list by executing the following command from an elevated command prompt:
dnscmd /config /globalqueryblocklist isatap
This command replaces the existing global query block list with only isatap. Remember to execute this command on each DNS server that is authoritative for your zone.
Although not recommended, you can also disable the global query block list functionality altogether by executing the following command from an elevated command prompt:
dnscmd /config /enableglobalqueryblocklist 0
Of course this functionality can be restored by executing the following command from an elevated command prompt:
dnscmd /config /enableglobalqueryblocklist 1
The global query block list functionality is also now included in security update MS09-008 for Windows Server 2003 DNS and WINS servers. This means that everything we’ve discussed here applies to Windows Server 2003 DNS servers with the MS09-008 update installed, with the exception of how the block list is configured. With Windows Server 2003 DNS and the MS09-008 update, management of the global query block list is done through the following registry key:
HKLM\SYSTEM\CurrentControlSet\Services
\DNS\Parameters\GlobalQueryBlockList
If you have already configured WPAD record in DNS, the good news is that if you perform an in-place upgrade to Windows Server 2008, WPAD functionality will not be disabled. The same holds true if you install the security update for MS09-008. Any existing functionality will remain if it was in place prior to the upgrade or update. For additional information on the MS09-008 security update, read this blog post by the Microsoft Security Research and Defense team.
Microsoft ISA Server 2006 Role Based Administration
Microsoft ISA Server 2006 features role based administration to provide granular access to the ISA firewall configuration and security policies. When configured properly, users who have local administrative rights on the underlying operating system do not implicitly have administrative privileges on the ISA firewall. The security model of the ISA firewall is such that administrative access is defined by the firewall administrator explicitly. However, during the process of installing ISA Server 2006, the BUILTIN\Administrators group, along with the account of the user installing the software is automatically added to the ‘ISA Server Full Administrator’ role. This is done for the obvious reason that someone has to be able to administer the firewall once it is installed!
While this default configuration is good for functionality, it is not particularly ideal for security. The domain administrators group is typically a member of the local administrators group on all domain-joined Windows systems (your ISA firewall should be a member of the domain!). However, do you want all of your domain administrators to have full control over your firewall? In small to mid-sized deployments, perhaps. In larger enterprise deployments, not likely. Now I realize that if you can’t trust your domain administrators you have a serious problem, but I also believe strongly in the principle of least privilege. I would much prefer to keep the number of firewall administrators to a bare minimum.
In my opinion, one of the first things an ISA firewall administrator should do is immediately remove the local administrators group and explicitly define the firewall administrators. In fact, I recommend defining your administrators by their individual user accounts as opposed to using local or domain groups. I prefer this method because it provides more control over who has ISA firewall administrative rights. If you decide to define your ISA firewall administrators by group, be sure to use restricted groups to prevent someone from intentionally or unintentionally adding unnecessary users to the ISA firewall administrators group.
Forefront Threat Management Gateway Beta 3 – Now Available!
The third beta for the forthcoming release of Microsoft Forefront Threat Management Gateway is now available! This latest release includes many new and wonderful features and functionality. In this latest release you will find an improved installation and setup utility that now automatically installs TMG prerequisites, including the .Net Framework 3.5 SP1 as well as required roles and role services. URL filtering is now included, along with support for SSTP VPN clients, improvements to the Network Inspection System (NIS), and enhancements to NAT. There’s even version of the management console for 32-bit machines! This is excellent news for TMG firewall administrators who wish to manage their firewalls remotely from 32-bit workstations.
In addition, there have been numerous improvements made to the UI. We now have the ability to search the rule base for specific objects (think “where used”!) and create groups for our access rules as well. Perhaps my favorite UI enhancement is the inclusion of NLB advanced settings for unicast or multicast operations. No more running scripts to change the NLB operational mode!
Beta 3 of Microsoft Forefront Threat Management Gateway can be downloaded here.
A Few Notes Regarding Remote SQL Logging with Microsoft ISA Server 2006 and Forefront Threat Management Gateway
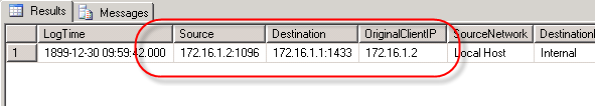
In response to my last blog post disucssing remote SQL logging for Microsoft ISA Server, several people asked about the data stored in the IP address fields of the ISA 2006 log database.
Clearly these are not IP addresses. In ISA versions up to and including ISA Server 2004, the data type for these fields were varchar(32) and contained IP addresses in the familiar dotted decimal notation.
Beginning with ISA Server 2006, the data type for these fields were changed to bigint. In order to convert the data from these fields to the more familiar dotted decimal notation, use the following SQL function (adapted from this KB article):
CREATE FUNCTION [dbo].[fnConvertIPToText] (
@ISALogIPAddress [bigint]
)
RETURNS varchar(15) AS
BEGIN
DECLARE @ConvertedAddress varchar(15)
SET @ConvertedAddress =
CAST(@ISALogIPAddress / 256 / 256 / 256 % 256 AS VARCHAR) + ‘.’ + CAST(@ISALogIPAddress / 256 / 256 % 256 AS VARCHAR) + ‘.’ + CAST(@ISALogIPAddress / 256 % 256 AS VARCHAR) + ‘.’ + CAST(@ISALogIPAddress % 256 AS VARCHAR)
RETURN @ConvertedAddress
END
[Download script here.]
(Special thanks to my good friend Christopher Schau, DBA extraordinaire, for creating this function for me!)
When selecting data from the table, use the function created above to convert the data follows:
SELECT
LogTime,
dbo.fnConvertIPToText(SourceIP) AS [SourceIP],
dbo.fnConvertIPToText(DestinationIP) AS [DestinationIP],
dbo.fnConvertIPToText(OriginalClientIP) AS [OriginalClientIP]
FROM
firewalllog
Data from the IP address fields returned from this query will now appear in the familiar dotted decimal notation.
Looking ahead to Microsoft Forefront Threat Management Gateway (TMG), the developers have once again changed the data type for IP address fields. In TMG, the data type for these fields were changed to uniqueidentifier. This was done in order to support IPv6 entries in these fields. In order to convert the data from these fields in to the more familiar dotted decimal notation, use the following SQL function:
CREATE FUNCTION [dbo].[fnIpAddressToText]
(
@Ipv6Address [uniqueidentifier]
)
RETURNS varchar(40) AS
BEGIN
DECLARE @strInAddress varchar(40)
DECLARE @strOutAddress varchar(40)
SET @strInAddress = LOWER(CONVERT(varchar(40), @Ipv6Address))
SET @strOutAddress = ”
IF (SUBSTRING(@strInAddress, 10, 4) = ‘ffff’)
BEGIN
— ipv4 (hex to int conversion)
DECLARE @IsNum int, @ZERO int, @IsAlpa int
set @ZERO = ASCII(‘0’)
set @IsNum = ASCII(‘9’)
set @IsAlpa = ASCII(‘a’) – 10
DECLARE @intH int, @intL int
SET @intH = ASCII(SUBSTRING(@strInAddress, 1, 1))
IF (@intH <= @IsNum) SET @intH = @intH – @ZERO ELSE SET @intH = @intH – @IsAlpa
SET @intL = ASCII(SUBSTRING(@strInAddress, 2, 1))
IF (@intL <= @IsNum) SET @intL = @intL – @ZERO ELSE SET @intL = @intL – @IsAlpa
SET @strOutAddress = CONVERT(varchar(3), @intH * 16 + @intL) + '.'
SET @intH = ASCII(SUBSTRING(@strInAddress, 3, 1))
IF (@intH <= @IsNum) SET @intH = @intH – @ZERO ELSE SET @intH = @intH – @IsAlpa
SET @intL = ASCII(SUBSTRING(@strInAddress, 4, 1))
IF (@intL <= @IsNum) SET @intL = @intL – @ZERO ELSE SET @intL = @intL – @IsAlpa
SET @strOutAddress = @strOutAddress + CONVERT(varchar(3), @intH * 16 + @intL) + '.'
SET @intH = ASCII(SUBSTRING(@strInAddress, 5, 1))
IF (@intH <= @IsNum) SET @intH = @intH – @ZERO ELSE SET @intH = @intH – @IsAlpa
SET @intL = ASCII(SUBSTRING(@strInAddress, 6, 1))
IF (@intL <= @IsNum) SET @intL = @intL – @ZERO ELSE SET @intL = @intL – @IsAlpa
SET @strOutAddress = @strOutAddress + CONVERT(varchar(3), @intH * 16 + @intL) + '.'
SET @intH = ASCII(SUBSTRING(@strInAddress, 7, 1))
IF (@intH <= @IsNum) SET @intH = @intH – @ZERO ELSE SET @intH = @intH – @IsAlpa
SET @intL = ASCII(SUBSTRING(@strInAddress, 8, 1))
IF (@intL <= @IsNum) SET @intL = @intL – @ZERO ELSE SET @intL = @intL – @IsAlpa
SET @strOutAddress = @strOutAddress + CONVERT(varchar(3), @intH * 16 + @intL)
END
ELSE
BEGIN
— ipv6
SET @strOutAddress = @strOutAddress + SUBSTRING(@strInAddress, 1, 4) + ':'
+ SUBSTRING(@strInAddress, 5, 4) + ':'
+ SUBSTRING(@strInAddress, 10, 4) + ':'
+ SUBSTRING(@strInAddress, 15, 4) + ':'
+ SUBSTRING(@strInAddress, 20, 4) + ':'
+ SUBSTRING(@strInAddress, 25, 4) + ':'
+ SUBSTRING(@strInAddress, 29, 4) + ':'
+ SUBSTRING(@strInAddress, 33, 4)
END
—- guid sample '6F9619FF-8B86-D011-B42D-FFF34FC964FF'
RETURN @strOutAddress
END
[Download script here.]
(Special thanks to Avi Sander with Microsoft Israel for sharing this SQL code with me. Shortly after I received this code it was also posted on the TMG Product Team Blog as well.)
I apologize in advance if any of the SQL code listed in this post is not readable. When posting code like this, formatting with WordPress can cause problems. If you have any issue with code on this page, send me an e-mail and I’ll be glad to send you the actual script files.