Archive
Changing the WebSpy Vantage Scheduled Task Recurrence Interval
There are many third-party reporting tools available today that can aggregate log data for analysis, reporting, and event correlation. One of my favorites for Microsoft Forefront Threat Management Gateway (TMG) 2010 is WebSpy Vantage. Vantage uses its own data stores (called storage), so before you can view logged data or generate reports, you must first import data from your current TMG logging repository (SQL or text file) in to Vantage storage. Once this data has been imported you can do pretty much whatever you want with it after that.
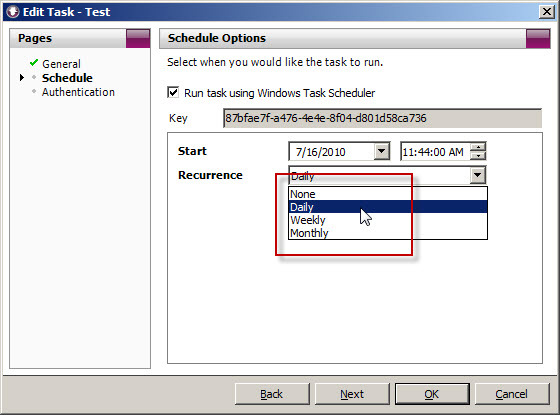
When you create a task to automate the import of log data, you will notice that the Recurrence options are limited to None, Daily, Weekly, and Monthly.
What if you’d like to import the data more frequently than daily? You could create another daily task and schedule that to run daily at a different time, but fortunately there’s an easier way. Since WebSpy Vantage leverages the Windows Task Scheduler, we can use the schtasks.exe command line tool to alter the schedule to run more frequently.
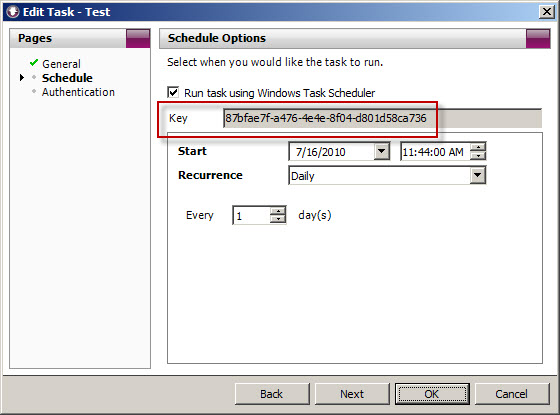
To accomplish this, first copy the Key for the scheduled task you wish to modify.
Next, open a command prompt. The syntax for the command when using Vantage Ultimate is:
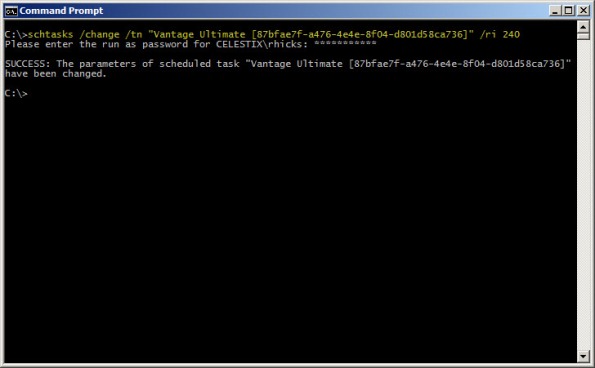
schtasks /change /tn “Vantage Ultimate […key…]” /ri <interval_in_minutes>
For example, if we want to alter the task above to run every 4 hours, the command would look like this:
schtasks /change /tn “Vantage Ultimate [87bfae7f-a476-4e4e-8f04-d801d58ca736]” /ri 240
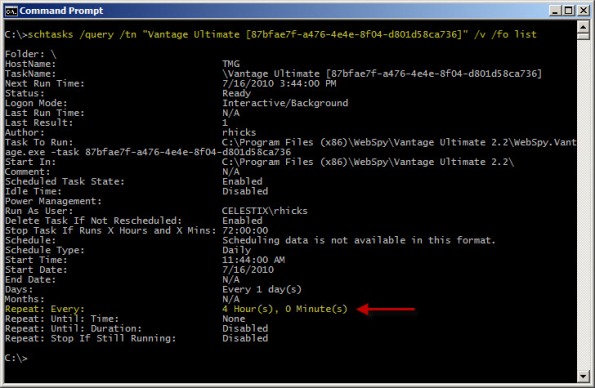
You can verify the new task settings by entering the following command:
schtasks /query /tn “Vantage Ultimate [87bfae7f-a476-4e4e-8f04-d801d58ca736]” /v /fo list
The output will look similar to this:
With schtasks.exe, the interval range in minutes is 1-599940.
Websense Integration Support for Forefront Threat Management Gateway (TMG) 2010
Updated July 11, 2011: Since this post was originally published, Websense now supports full integration with Forefront TMG 2010 with Websense Web Security/Web Filter v7.6.
There seems to be a fair amount of confusion regarding Websense integration support for Microsoft Forefront Threat Management Gateway (TMG) 2010. As you are most likely aware, TMG is 64-bit only and is supported only on Windows Server 2008 64-bit and Windows Server 2008 R2 64-bit. You cannot install TMG on any 32-bit operating system. By contrast, Websense Web Security and Web Filter today (July, 2010) are 32-bit only and are not supported on any 64-bit operating system. These architectural differences clearly limit the integration capabilities for Websense and TMG.
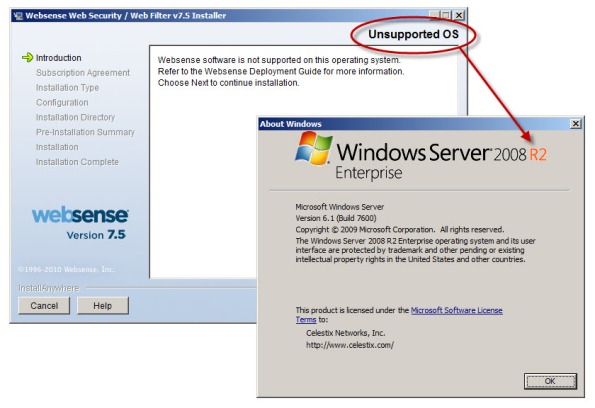
Recently Websense announced the availability of Websense Web Filter and Web Security v7.5, which now includes limited support for integration with TMG. In this release, no Websense components (with the exception of the filtering plug-in) can be installed on the TMG firewall system. In order to support Websense integration with TMG, you must have a separate system or systems on which to install the Websense policy, filtering, user identification, and logging/reporting components. For typical enterprise deployments this won’t be an issue, but this is disappointing news for many small to mid-sized customers who don’t need or want the extra overhead of multiple systems to provide URL filtering services. Another serious limitation is that Websense Web Filter and Web Security v7.5 are currently not supported on Windows Server 2008 R2, at all. If you have installed TMG on Windows Server 2008 R2, you are out of luck.
Thankfully, TMG includes native URL filtering capabilities that, when combined with other TMG advanced protection technologies such as integrated virus and malware scanning, HTTPS inspection, and the vulnerability-based intrusion detection and prevention system, provide a consolidated and comprehensive secure web gateway solution that ultimately affords more overall protection compared to URL filtering solutions alone. TMG includes a 120-day evaluation of these advanced web protection technologies (beginning at the time of product installation, not the activation of the URL filtering feature itself!) so there’s no obligation to try it out. Take it for a test drive…I think you’ll be impressed! It performs well, scales very effectively, and is much easier to manage than many third-party integrations.
Load Balancing and Forefront TMG Firewall Clients
Recently I encountered an issue where TMG firewall clients were experiencing intermittent connectivity issues. Clients were sometimes able to connect to a remote RDP server, and other times they were not. Web proxy clients were working perfectly. After looking carefully at the network and TMG firewall configuration, everything appeared to be in order with no apparent issues. In this particular instance, two TMG firewalls were configured in a multi-homed, standalone array with Network Load Balancing (NLB) enabled on both the Internal and External networks. Clients connect to the array using a hostname that resolves to the virtual IP address (VIP) assigned to the Internal network.
Although this configuration works just fine for web proxy clients, it poses a particular problem for the TMG Firewall Client because the Firewall Client uses a control channel to facilitate authentication and communication with the TMG firewall. For proper operation, Firewall Clients must be configured to communicate directly with the TMG firewall’s dedicated IP address (DIP). For this reason, the use of NLB and third-party hardware load balancers is not supported for load balancing TMG Firewall Clients. The only form of load balancing that is supported for TMG Firewall Clients is DNS round-robin.
To learn more about the TMG Firewall Client and how it functions, please refer to Jim Harrison’s excellent series of articles about this topic on TechNet.
Introduction to the ISA Server Firewall Client and Forefront TMG Client
Introduction to Remote Winsock (RWS) Protocol Analysis
Observing Firewall Client Single-connection HTTP Traffic
Observing Firewall Client Single-connection DNS Traffic