Archive
Microsoft Operations Framework (MOF) Reliability Workbooks
The Microsoft Operations Framework (MOF) provides important guidance for IT professionals responsible for maintaining and operating various Microsoft technologies. The MOF Technology Library includes a series of workbooks that provide detailed knowledge, tasks, and schedules required to keep these technologies operating efficiently and without issue. There are workbooks available today for many Microsoft infrastructure and application services, including Active Directory, DNS, Exchange, SQL, IIS, and many more. Reliability workbooks for Forefront Unified Access Gateway (UAG) and DirectAccess were recently added to the library. The Network Load Balancing (NLB) workbook will also be helpful for many TMG and UAG administrators. If you are responsible for deploying or managing these technologies in your organization, these workbooks are sure to be beneficial.
Forefront TMG Malware Protection and the Unified Access Gateway (UAG)
Forefront Threat Management Gateway (TMG) 2010 includes integrated virus and malware inspection capabilities that provide enhanced protection for clients accessing the Internet through TMG. The scanning engine used by TMG is the same engine included in many Forefront protection technologies such as Forefront Protection for Exchange (FPE), Forefront Protection for SharePoint (FPS), and the forthcoming Forefront Endpoint Protection (FEP), just to name a few. This same scanning engine is also the heart of the Microsoft Security Essentials desktop antivirus offering, which is very highly rated by independent third parties. It has a proven track record of being efficient and performing well, with a high degree of accuracy and extremely low false positives.
Since the Forefront Unified Access Gateway (UAG) 2010 includes TMG, many UAG administrators believe that they can enable TMG malware protection to protect their UAG-published applications. Unfortunately, this does not work. With UAG, all SSL VPN traffic is processed by the UAG ISAPI filter, not the underlying TMG firewall. TMG is used only to protect the UAG host itself, so enabling TMG malware inspection on the UAG system has no effect whatsoever.
If you are thinking you can leverage the malware inspection capabilities when publishing applications using TMG, it still doesn’t work. With TMG, the malware inspection engine works only in forward proxy scenarios (HTTP requests made by TMG protected clients). Malware inspection does not apply to reverse proxy traffic at all in TMG.
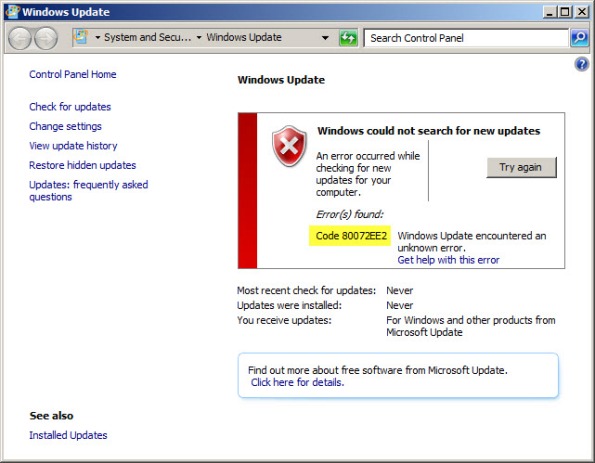
Running Windows Update on a TMG Firewall Fails with Result Code 80072EE2
Recently I have encountered a few instances in which the Windows Update client on a system with Forefront Threat Management Gateway (TMG) 2010 installed is unable to retrieve updates and fails with an error code of 80072EE2.
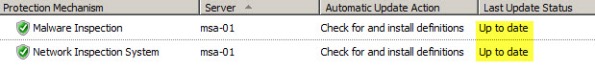
When this occurs, Malware Inspection and Network Inspection Systems signature updates are received without issue.
To resolve this issue, open an elevated command prompt and enter the following command:
netsh winhttp set proxy localhost:8080
If it is necessary to access HTTP and/or HTTPS web sites or services on your Internal network from the TMG firewall, you will need to configure the proxy bypass list. To learn how, enter the following command:
netsh winhttp set proxy ?
If you need to configure Windows Update on the TMG firewall to work with WSUS, read this blog post on the Forefront TMG product team blog.