Archive
Preparing Forefront TMG 2010 for Enterprise Workgroup Deployment
Deploying Forefront Threat Management Gateway (TMG) 2010 in a workgroup (non-domain joined) enterprise array configuration can present a significant challenge to many administrators. This post isn’t meant to be a comprehensive TMG Enterprise Management Server (EMS) deployment guide, but I would like to share with you a few important tips that will hopefully make the process of creating an EMS-managed array a little easier.
Before Installing EMS
IP Addressing – Make certain that all basic IP connectivity is verified before installing any Forefront TMG 2010 services.
Name Resolution – Confirm that name resolution is working properly and that hostnames are being resolved to the correct IP addresses. Be sure that these IP addresses are assigned to the Internal network interface of the EMS and each array member.
Certificates – The EMS will require a machine certificate, and each array member should trust the Certificate Authority (CA) that issued this certificate. It is recommended that this certificate be issued by your internal private CA and not a public third-party CA. The certificate should be for server authentication and the common name on the certificate should be the FQDN of the host it is to be installed on. Be sure to install the root certificate and any intermediate certificates for the CA on the EMS and each array member. Make certain the certificate is issued with the option for the private key to be exportable.
Local Accounts – Identical (mirrored) local accounts should be configured on the EMS and each array member and be granted administrative rights for the Forefront TMG 2010 Enterprise.
After Installing EMS
Before joining a TMG firewall to an array, you can perform some preliminary tests to determine if certificate authentication between hosts is working correctly. To do this, open a PowerShell command window and enter the following commands:
import-module servermanager add-windowsfeature rsat-adlds
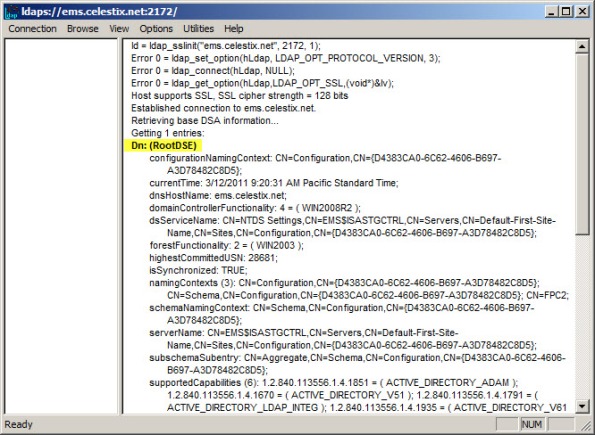
Once complete, click Start | Run and enter ldp.exe. From the drop-down menu choose Connection, and then Connect…. For the server, enter the fully-qualified domain name (FQDN) of the EMS, specify port 2172, and then select the option to use SSL.

If certificate authentication is working correctly you will connect to the RootDSE. If it is not configured correctly you will receive a connection error.
To determine if user authentication is working correctly, select Connection from the drop-down menu and then Bind…. If you are currently logged on with the local mirrored account, select the option to Bind as currently logged on user, otherwise select Bind with credentials and enter the user and password of the mirrored account (leave the domain blank).

If configured correctly you will receive notification that you have been authenticated. If not, you will be notified that the logon attempt failed.
Once you’ve completed these steps you can proceed with configuring the TMG firewall to join the array. Be sure to specify the name of the EMS in exactly the same format as the certificate common name (preferably using the FQDN ).
Phoenix Unified Communications User Group
Are you interested in learning how Forefront Threat Management Gateway (TMG) 2010 can protect your Microsoft Exchange implementation? If so, join me at the Phoenix Unified Communications User Group meeting at 4:00PM on Wednesday, March 30 2011 in Tempe, AZ where I’ll be presenting on the topic. We’ll discuss how to leverage TMG to protect Outlook Web App, Exchange ActiveSync, OutlookAnywhere, and SMTP communication. This month’s meeting is being held at the new Microsoft building. The address is:
Microsoft Corporation
60 E. Rio Salado Parkway
12th Floor
Tempe, AZ 85282
[map]
You can register for the event here. Hope to see you there!