Addressing Security Issues with PPTP VPN in Forefront TMG 2010
At the recent DEFCON hacking conference, security researchers demonstrated a method to crack the MS-CHAPv2 authentication protocol with a 100% success rate. MS-CHAPv2 is used as the default authentication method for remote access VPN in Forefront TMG 2010.
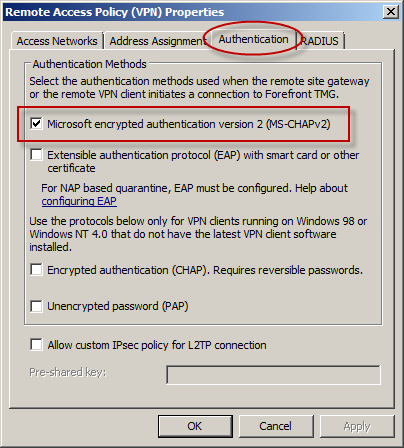
With the public availability of tools to automate the cracking process, PPTP communication using MS-CHAPv2 should be considered unencrypted. There are two options available to mitigate this concern: disable MS-CHAPv2 and enable EAP with PPTP, or disable PPTP and switch to a more secure remote access VPN protocol such as L2TP/IPsec or SSTP. Enabling EAP requires the use of smart cards or certificates for authentication which makes implementation more challenging. SSTP is an excellent option as it leverages SSL/TLS to protect the MS-CHAPv2 authentication process. However, SSTP is only supported on Windows Vista SP1 and later clients. L2TP/IPsec is another good choice, and although it does support certificates it can also be configured using a pre-shared key. If long, complex passwords are used and care is taken to ensure that the password is well protected, it can provide a secure remote access solution.





Richard,
Good post pointing out the potential risk in PPTP VPNs, but the fact that MS-CHAPv2 has been cracked is a scary one.
There are so many things dependent on this technology like wireless authentication, dailin connectivity, 802.1x implementations etc. etc.
I guess we are going to see lots of interesting hacks over the next couple of months as a result of this.
Hi Richard,
i think SSTP is allready available with Windows Vista SP1?!
Greets from Germany,
Jens Mander…
Agreed. Remote access is especially troublesome here because the traffic is passed over untrusted networks. I’d say that any wireless authentication relying on MS-CHAPv2 would be next in order of importance. Certainly we’ll have to deal with other technologies that leverage MS-CHAPv2 soon enough.
You are correct. I’ve updated the article accordingly. 🙂 Thanks!
Great post! I´m sharing at my company!
What would be required to carry out this attack? From what I understand you would need to do a packet capture over the physical wire, or an unencrypted wireless connection, correct? You can’t just attack a server outright, you have to be able to capture a login process as it is happening?
Yes, this attack would involve the attacker capturing network traffic between the client and the VPN server during the connection setup. The most obvious scenario for this would be when a user was connected to an open wireless network, which is quite common these days unfortunately.
Hi Richard,
Its there a way to configure a custom L2TP port for TMG 2010?? instead of using the default VPN L2TP port.
Not to my knowledge…