Archive
Forefront TMG 2010 Network Inspection System NIS Signature Updates
When Microsoft announced the formal end-of-life for Forefront TMG 2010, they laid out in clear detail the support boundaries for the product going forward. Microsoft stated specifically that they would continue mainstream support for TMG until April of 2015, and extended support would terminate in April 2020. However, the Web Protection Service (WPS) updates for the URL filtering database, antimalware signatures, and the Network Inspection System (NIS) would only continue until December 31, 2015.
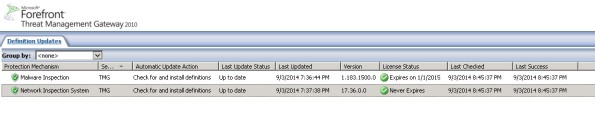
Unfortunately, it appears that Microsoft has abandoned the updating for NIS signatures. You may have noticed that a fully updated Forefront TMG firewall with the latest signature updates shows that the last NIS signature was released for security bulletin MS12-050 on July 20, 2012!
I find it difficult to believe that there hasn’t been a single vulnerability discovered or hotfix released since July of 2012 that wouldn’t benefit from NIS protection, so I have to assume that Microsoft is no longer supporting NIS in spite of their pledge to provide support for WPS through the end of 2015. If you are relying on NIS for essential network protection, it’s time to consider deploying a dedicated IDS/IPS solution or another solution that provides this functionality.
Recommended Forefront TMG 2010 SSL and TLS Configuration
Last year I wrote an article for ISAserver.org that provided detailed guidance for improving security for SSL and TLS protected web sites using Forefront TMG 2010. Many people have reached out to me recently to ask about enabling forward secrecy, which my original article did not include because, at the time, it was not recommended to enable it. However, as times have changed, it is now recommended to enable forward secrecy so I recently wrote a short post with guidance on how to do that. The post was written with a very narrow scope and addressed only the enabling of forward secrecy for TLS. Many of you have since asked for guidance on overall security best practices with regard to SSL and TLS along with adding support for forward secrecy. In addition to the configuration changes detailed in my original ISAserver.org article, I also recommend the following list of SSL and TLS cipher suites be explicitly enforced using the method outlined here.
TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256_P256 TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256_P384 TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256_P521 TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384_P384 TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384_P521 TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256_P256 TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA_P256 TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA_P256 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256_P256 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384_P256 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA_P256 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA_P256 TLS_DHE_DSS_WITH_AES_128_CBC_SHA256 TLS_DHE_DSS_WITH_AES_256_CBC_SHA256 TLS_DHE_DSS_WITH_AES_128_CBC_SHA TLS_DHE_DSS_WITH_AES_256_CBC_SHA TLS_RSA_WITH_AES_128_CBC_SHA256 TLS_RSA_WITH_AES_256_CBC_SHA256 TLS_RSA_WITH_AES_128_CBC_SHA TLS_RSA_WITH_AES_256_CBC_SHA
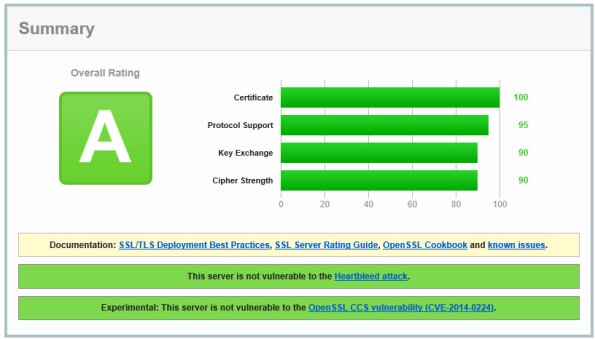
Using this configuration, the Forefront TMG 2010 firewall should receive an A rating from the SSL Labs test site (at the time of this writing).
Enabling and supporting the above list of cipher suites will provide the best overall protection and performance for your SSL protected web sites. Note that the list above does not include support for SSL 3.0. If you need to support SSL 3.0 you should add the following cipher suites to the end of the list.
TLS_RSA_WITH_RC4_128_SHA TLS_RSA_WITH_RC4_128_MD5
Please note that this configuration may not work with older browsers on old, unsupported operating systems, for example Internet Explorer 6 on Windows XP. Before deploying this configuration in production I would encourage you to conduct some testing with your supported clients to ensure operability.