Forefront TMG 2010 SQL Services Fail to Start After Disabling SSL 3.0
When performing POODLE attack mitigation on the Forefront TMG 2010 firewall by disabling SSL 3.0, you may encounter a scenario in which TMG’s SQL services fail to start after a reboot.

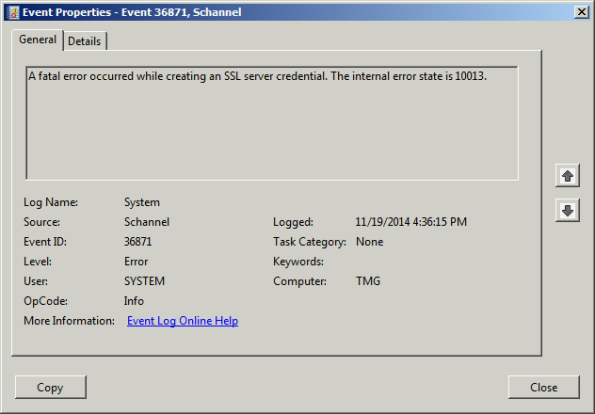
Looking through the Windows system event log you may see an error message logged by the Service Control Manager with event ID 36871 which states:
A fatal error occurred while creating an SSL server credential. The internal error state is 10013.
In addition you may also see an error message logged by the Service Control Manager with event ID 7024 which states:
The SQL Server (ISARS) service terminated with service-specific error %%-2146893007.

This can occur when SSL 3.0 is disabled at the same time that TLS 1.0 is also disabled. Even though TLS 1.1 and 1.2 might be enabled, TMG requires that TLS 1.0 specifically be enabled for SQL server services to function properly when SSL 3.0 is disabled.
To resolve this issue, enable TLS 1.0 Server in the registry by changing the value of Enabled to 1, as shown here. If these registry keys do not exist, create them.

Restart the server for the change to take effect.





Probably a stupid question but is this also the case if TMG is configured to log in W3C format?
I didn’t test it, but it probably does. Switching to text file logging doesn’t remove SQL. However, you’ll be less impacted by SQL services being stopped than you would be otherwise. 🙂
Thanks Richard. I’m just trying to anticipate future calls from our Security Team to disabling TLS 1.0 🙂
Hi Richard
great article, thank you 🙂
I have been informed that TLS 1.0 is no longer acceptable for compliance under PCI DSS 3.1, and we are now being asked to disable this 😦 how would this be possible without impacting TMG (and UAG for that matter)? is there a way to move the TMG logging and reporting to another SQL server?
Unfortunately TMG will not work without TLS 1.0 enabled, even if you choose another logging option. This is where TMG is really beginning to show its age.