Archive
Troubleshooting with the Windows Sysinternals Tools 2nd Edition Now Available
The Windows Sysinternals utilities are essential tools for troubleshooting Windows platforms and systems. The tools are being updated constantly, and recently a 2nd edition of the book “Troubleshooting with the Windows Sysinternals Tools” was released. This is an important reference for anyone using these tools to perform Windows troubleshooting. Order your copy today!
Using PowerShell to Determine Forefront TMG Build Number
 Identifying the current build number of your Forefront TMG 2010 installation is critically important when making changes or updates to the system. It is generally recommended that all TMG firewalls be on the same release, so having this information is essential. Many TMG administrators use the TMG management console to gather this information, but I can tell you based on experience that this is not always the most accurate method to use.
Identifying the current build number of your Forefront TMG 2010 installation is critically important when making changes or updates to the system. It is generally recommended that all TMG firewalls be on the same release, so having this information is essential. Many TMG administrators use the TMG management console to gather this information, but I can tell you based on experience that this is not always the most accurate method to use.
I much prefer to gather this information programmatically at the command line. In the past I’ve written about using VBScript to do this, but it’s almost 2016 now and we really should be using PowerShell whenever possible. To that end, here are a few lines of PowerShell code you can use to accurately determine which version and build number your TMG firewall is currently running.
$FPC = New-Object -ComObject FPC.Root $Server = $FPC.GetContainingServer() $Server.ProductVersion

If you’ve done any work at all with VBScript and the TMG’s FPC COM object, you’ll no doubt be able to convert some of your existing scripts to PowerShell. Also, PowerShell, with its tab auto completion, is much more discoverable than using VBScript with COM, so I’m sure you’ll be able to do a lot more with TMG using PowerShell.
Enjoy!
Reminder: Microsoft Reputation Services (MRS) End of Support
 As a reminder to anyone out there still using the URL filtering feature of their Forefront TMG 2010 firewall, the Microsoft Reputation Services (MRS) service, which provides URL categorization for TMG, will no longer be supported after December 31, 2015. After this date, Microsoft will cease updating their URL categorization database. In addition, there are no guarantees from Microsoft that the service will be available in any form, so customers still using this service are strongly encouraged to look for alternative solutions.
As a reminder to anyone out there still using the URL filtering feature of their Forefront TMG 2010 firewall, the Microsoft Reputation Services (MRS) service, which provides URL categorization for TMG, will no longer be supported after December 31, 2015. After this date, Microsoft will cease updating their URL categorization database. In addition, there are no guarantees from Microsoft that the service will be available in any form, so customers still using this service are strongly encouraged to look for alternative solutions.
For many organizations, this means migrating to another platform entirely, which is not a bad idea considering that TMG is nearly six years old now. Alternatively, it is possible to replace TMG’s web filtering component. This can be done on premises by using integrations from various third-party vendors, or by using a cloud-based solution such as Zscaler.
Regardless which path you take, you have just over one month to identify and implement another URL filtering solution. Good luck!
ISAinfo Forefront TMG 2010 Configuration Reporting Utility
 With the demise of isatools.org a few years ago, many ISA Server and Forefront TMG 2010 administrators have reached out to me to ask where they can find the ISAinfo tool that was previously found on that site. If you’re not familiar with ISAinfo, it was a great utility used for viewing the ISA or TMG configuration by parsing the configuration export. This tool is tremendously useful for providing support, as it includes all of the information required to provide context for troubleshooting. In addition it is an excellent documentation tool.
With the demise of isatools.org a few years ago, many ISA Server and Forefront TMG 2010 administrators have reached out to me to ask where they can find the ISAinfo tool that was previously found on that site. If you’re not familiar with ISAinfo, it was a great utility used for viewing the ISA or TMG configuration by parsing the configuration export. This tool is tremendously useful for providing support, as it includes all of the information required to provide context for troubleshooting. In addition it is an excellent documentation tool.
So, if you’re looking for a reputable location from which to download this tool, look no further. I’ve placed the isainfo.zip file along with the checksums for file verification on my public OneDrive. Enjoy!
ISAinfo.zip – http://1drv.ms/1Q8GOaA
Checksums – http://1drv.ms/1Q8GWqq
Fastvue TMG Reporter v2.1 Now Available
Today Fastvue announced the general availability of TMG Reporter v2.1, the latest release of their advanced reporting and alerting platform built specifically for Forefront TMG 2010. I’ve been working with some of the early release builds and although this is technically considered a minor release, this latest update includes some important new features that make this a worthwhile and compelling upgrade. Here are some of the great new features included with TMG Reporter v2.1:
Activity Reports – Easily the single most important feature included in Fastvue TMG Reporter v2.1 is the addition of detailed activity reports. Prior to v2.1 only overview reports were available. You can now create extremely granular reports on user, site, category, or application activity that include timestamps, full URLs, browse time, category, and disposition (allowed or denied).
Scheduled Custom Reports – Another excellent new feature in Fastvue TMG Reporter v2.1 allows the administrator to create custom reports using the new filtering interface and schedule them for automated delivery to recipients.
Comprehensive Filtering – Fastvue TMG Reporter v2.1 includes a powerful new filtering facility that allows security administrator to dig deep in to the logging data to find the pertinent information they desire. The new enhanced filtering feature is available for use on all reports.
Drilldown Reporting – Another feature that has been greatly improved in the v2.1 release is drilldown reporting. Previously executing a drilldown report resulted in the creation of a completely new and separate report. With v2.1, the new drilldown report now respects the initial filter settings, allowing the administrator to see detailed information as necessary while maintaining the context that the original report was created within.
SQL Server integration – This is one of my favorite (and most requested!) new features. TMG Reporter v2.1 now includes native support for SQL server logging. There are many compelling reasons to configure the Forefront TMG 2010 firewall to log to an external SQL server, and now TMG Reporter can connect directly to your TMG firewall’s configured SQL server to collect report data.
Full support for Windows 8 and Server 2012 – You can now install TMG Reporter on Windows 8 and Windows Server 2012! This is great news as many organizations are beginning to deploy Windows 2012 server and Windows 8 desktops. The TMG Reporter installer now detects which server platform you are installing on and installs the necessary prerequisites automatically. The TMG Reporter web interface is also fully supported on Windows 8 with Internet Explorer 10 (modern and desktop).
Since its initial release a few years ago, Fastvue TMG Reporter has continued to add features and functionality. If you’re running an older version, or if you haven’t yet made the switch to TMG Reporter, the new capabilities in TMG Reporter v2.1 may finally compel you to take the leap and implement or upgrade to TMG Reporter v2.1 for your Forefront TMG monitoring, alerting, and report needs. Download a free, fully functional evaluation copy of Fastvue TMG Reporter v2.1 today. You’ll be glad you did, trust me!
Fastvue Enhanced Reporting for Forefront TMG 2010
Recently I had the pleasure of reviewing the Fastvue Dashboard product for Forefront TMG 2010 at ISAserver.org. Fastvue is a real-time dashboard that integrates with Forefront TMG to provide a nearly instantaneous view of traffic being controlled by your TMG firewall. Although the real-time dashboard is a nice feature, if you’ve spent any time at all with Forefront TMG 2010’s native reporting tools you know that TMG is severely lacking in this area. A major limitation of Forefront TMG 2010’s in-box reporting is that the reports are generated using summarized data. Data summarization occurs only once daily, so reports can be lacking essential information if you are looking for recent activity. In addition, the native reports are static and one-dimensional. If a report reveals something interesting that you want to know more about, creating and generating a new report is required.
Thankfully the good folks at Fastvue recognized these shortcomings and have addressed many of these issues with their latest release. Fastvue v2.0 now includes full historical reporting capabilities, with detailed company overview and user investigation reports that can be shared via e-mail. Reports can also be scheduled to run automatically. The reports are highly interactive, allowing the administrator to dynamically drill down to generate more granular reports in an instant.
The current version of Fastvue is priced at $395.00 per TMG firewall. The newest version will be priced at $795.00 per server. However, for a limited time, readers of my blog can purchase Fastvue v1.0 for the current price and receive a free upgrade to v2.0 when it is released. Click here to download a trial of the software and to take advantage of this offer!
ESET Gateway Security Beta for Forefront TMG 2010
For security administrators looking to improve upon Forefront TMG 2010’s already strong advanced web protection features, leading anti-virus vendor ESET recently announced the beta availability of its Gateway Security for Forefront TMG 2010 software. ESET Gateway Security for Forefront TMG delivers advanced, gateway-integrated virus and malicious software scanning to provide comprehensive protection for web-based protocols like HTTP and FTP. ESET Gateway Security for Forefront TMG also supports SMTP, IMAP, and POP3 protocols to provide anti-malware and anti-spam capabilities for added protection. In addition, ESET Gateway Security for Forefront TMG 2010 includes host-based security for the TMG firewall’s underlying operating system, as well as automatic file exclusion configuration to ensure compatibility with Forefront TMG. ESET Gateway Security for Forefront TMG 2010 is fully compatible with existing ESET centralized management tools and supports Microsoft ISA Server 2006. Download the beta today!
Configuring Splunk Universal Forwarder on Forefront TMG 2010
Aggregating logged data from security devices such as the Forefront Threat Management Gateway (TMG) 2010 firewall is a top priority for many security engineers. Forefront TMG and its predecessor, ISA Server, have always lacked an integrated facility to forward logged data to an external event management system. Often the administrator will have to devise an elaborate process that consists of batch files or scripts that collect firewall and web proxy logs and copy them to another location where they can be consumed. In the past I’ve demonstrated how third-party utilities can convert firewall log data to the syslog format as well.
Splunk is one of the more popular log management systems in use today, and to make it easier to get Forefront TMG log data in to Splunk we can use the Splunk Universal Forwarder. The Universal Forwarder is a utility that installs on the Forefront TMG firewall and monitors the folder containing W3C formatted text log files. The Universal Forwarder has a small footprint and consumes few resources, making it the ideal method to collect Forefront TMG log data and deliver it to the Splunk indexing server for analysis and archiving. The Splunk Universal Forwarder can be downloaded here.
Configuring Forefront TMG 2010
Before installing the Universal Forwarder, the Forefront TMG firewall must be configured to log to text file format. To change the log file format, open the Forefront TMG management console and highlight the Logs & Reports node in the navigation tree, select the Logging tab in the center console window, and then click Configure Firewall Logging in the Tasks pane on the right.

Select the option to log to File and choose the W3C extended log file format from the drop down box below. Repeat these steps to configure web proxy logging.

When the option to log to text file format is chosen, native Forefront TMG reports cannot be generated and access to historical log data in the Forefront TMG management console is no longer possible. Clicking Ok will generate the following warning message:
Reports cannot be generated with the currently selected logging method. To generate reports, use logging to SQL Server Express databases (on the local server).

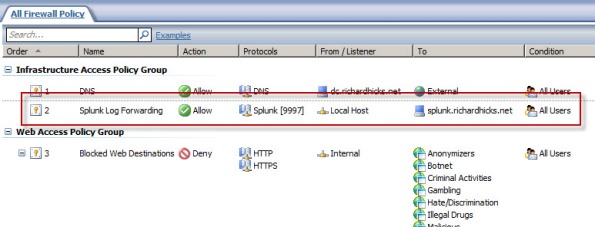
An access rule must be created to allow the Splunk Universal Forwarder to communicate with the Splunk indexing server. The source will be the local host network, the destination will be the Splunk indexing server, and the protocol will be TCP 9997 (outbound), which is the default port used by the Splunk Universal Forwarder.
Configuring Splunk Universal Forwarder
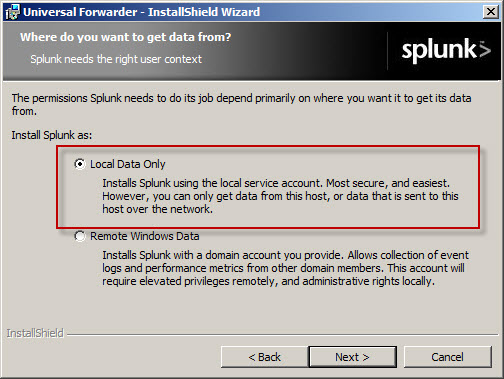
Next, install the Splunk Universal Forwarder on the Forefront TMG firewall. When prompted, enter the hostname, FQDN, or IP address of your indexing server and specify a TCP port to use (the default is TCP port 9997).

Select the option to forward Local Data Only.
The Forefront TMG firewall will create new text log files each day and store them in the specified log files folder. Specify a Path to monitor by clicking Directory… and selecting C:\Program Files\Microsoft Forefront Threat Management Gateway\Logs (or the path where your log files are stored, if different from the default).

Configure Splunk Indexing Server
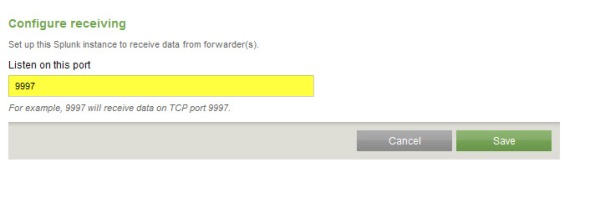
Once the installation is complete, open the Splunk Manager and click Forwarding and receiving.

Click the Add new link next to Configure receiving.
Configure the indexing server to Listen on this port and enter 9997.
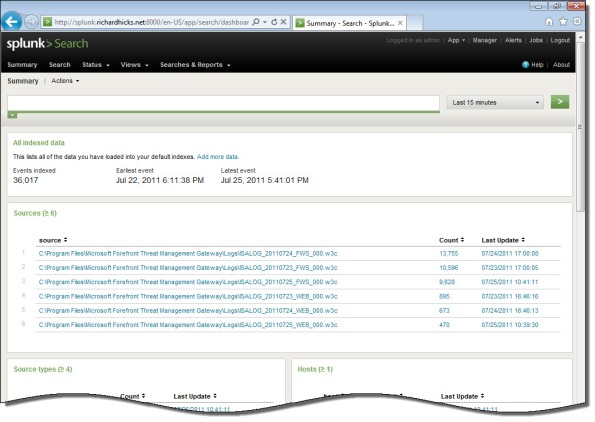
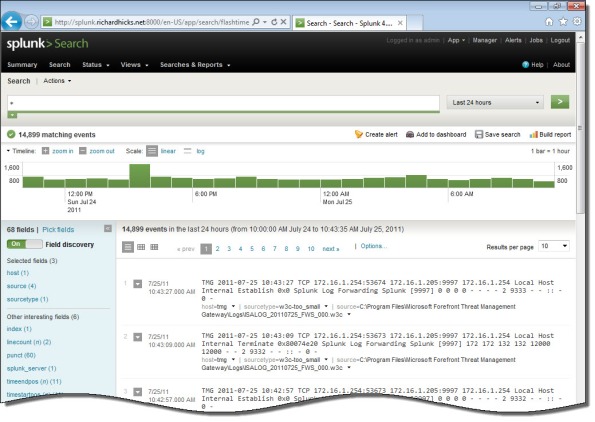
Once you’ve configured Splunk to receive data from the forwarder, Forefront TMG firewall and web proxy log data should appear on the indexing server.
Security Configuration Wizard for Forefront TMG 2010 and Windows Server 2008 R2 SP1
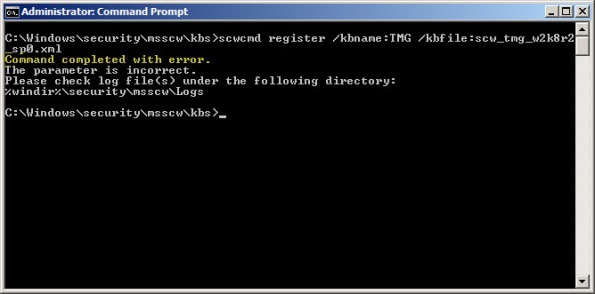
Security hardening and attack surface reduction is an important step in preparing a Forefront TMG 2010 firewall. To accomplish this task, the tool of choice is the Security Configuration Wizard (SCW). In one of my ISAserver.org articles I demonstrated how to use this tool to properly configure the underlying operating system to support the Forefront TMG 2010 firewall role. Since the native Windows SCW does not include support for the Forefront TMG role, the TMGRolesForSCW.exe utility included in the Forefront TMG Tools and SDK is required. This tool was released prior to service pack 1 for Windows Server 2008 R2 and does not include a template that works correctly out of the box. When you attempt to register the Windows Server 2008 R2 template on a system with SP1 installed you will receive the following error:
Command completed with error. The parameter is incorrect. Please check log file(s) under the following directory: %windir%\security\msscw\logs
To resolve this issue, create a copy of the template file SCW_TMG_W2K8R2_SP0.xml and name it SCW_TMG_W2K8R2_SP1.xml. Open this file with any text editor and navigate to the SCWKBRegistrationInfo node (line 2). Change the value of ServicePackMajorVersion from “0” to “1” and save the file. Register the template using the following command:
scwcmd register /kbname:TMG /kbfile:scw_tmg_w2k8r2_sp1.xml
Continue using the SCW to configure and apply a security template to your TMG firewall following the instructions in my ISAserver.org article.
Fwengmon.exe and Forefront Threat Management Gateway (TMG) 2010
For engineers performing advanced troubleshooting on TMG, you have likely noticed that fwengmon.exe, a utility that you used with previous versions of ISA, no longer functions with TMG.

Not to worry! This detailed information is readily accessible using netsh.exe in the tmg context. The following is a list of common commands and their fwengmon.exe equivalents (where applicable):
To view creation objects, active sessions, NLB hook rules, NLB server assigned ranges, and dynamic and persistent allowed ranges:
netsh tmg show all
To view connections only (fwengmon.exe /session or /s):
netsh tmg show connections
To view detailed information about a specific connection (fwengmon.exe /s <ID>):
netsh tmg show connections <connection_number>
To view firewall creation elements (fwengmon.exe /creations or /c):
netsh tmg show creations
Note: You can sort and filter output from show connections or show creations by source IP address, source port, destination IP address, destination port, or protocol using the sort and filter parameters (fwengmon.exe /organize or /o, or fwengnmon.exe /filter or /f). You can also limit the number of connections or creations displayed using the display parameter. Type netsh tmg show connections ? or netsh tmg show creations ? for more information.
To show NLB hook rules (fwengmon.exe /querynlb or /n):
netsh tmg show nlbhookrules
To view packets held in kernel mode:
netsh tmg show holdpackets
To view packets held in user mode:
netsh tmg show usermodepackets
To view global firewall engine driver settings:
netsh tmg show global
To specify a temporary address range to exempt from firewall filtering (fwengmon.exe /allow or /a):
netsh tmg add allowedrange <beginning_ip> <ending_ip>
To specify a permanent address range to exempt from firewall filtering (fwengmon.exe /allow or /a):
netsh tmg add allowedrange <beginning_ip> <ending_ip> persistent
Note: netsh tmg add allowedrange allows all traffic to and from hosts within the IP address range specified to bypass stateful firewall inspection completely. It should be used for troubleshooting purposes only.
To delete a temporary address range (fwengmon.exe /noallow):
netsh tmg delete allowedrange id=<id>
To delete a permanent address range (fwengmon.exe /noallow):
netsh tmg delete allowedrange id=<id> persistent