Archive
Forefront TMG 2010 Computer Certificate Request or Renewal Fails
When attempting to request or renew a computer certificate on the Forefront TMG 2010 firewall, you may receive the following error message:
Status: Failed The RPC server is unavailable.

This occurs because the Forefront TMG 2010 firewall does not, by default, allow the protocols and ports required to request or renew a certificate from a Certificate Authority (CA). Common workarounds suggest stopping the firewall completely or creating a rule allowing all protocols and ports from the TMG firewall to the CA. However, both of these workarounds are problematic. Stopping the firewall is a manual process that will cause a service disruption. It also leaves the firewall in an unprotected state. For edge deployment scenarios, the underlying operating system will be exposed directly to untrusted networks, which is a serious security risk. Creating an open access rule is not desirable because it violates the basic security principle of least privilege by allowing more access than is required.
To properly address this issue and allow for the secure request and renewal of certificates without disruption and with the least exposure, it will be necessary to create an access rule on the Forefront TMG 2010 firewall to allow all dynamic ports (TCP 49152-65535) from the local host network to the IP address of the CA for all users.
Note: Allowing all dynamic ports (TCP 49152-65535) might also be considered too much access from the Forefront TMG 2010 firewall to the CA. It is possible to restrict the dynamic ports used by TMG and further tighten the access rule, if required. For information about restricting dynamic ports, click here.
In addition to the access rule allowing all dynamic ports, it will also be necessary to make a change to a system policy rule. To do this, right-click the Firewall Policy node in the navigation tree and choose All Tasks, System Policy, and then Edit System Policy. In the Authentication Services group highlight Active Directory and clear the checkbox next to Enforce strict RPC compliance.

Once these changes have been made you can now request or renew a computer certificate on the Forefront TMG 2010 firewall successfully.

Addressing Security Issues with PPTP VPN in Forefront TMG 2010
At the recent DEFCON hacking conference, security researchers demonstrated a method to crack the MS-CHAPv2 authentication protocol with a 100% success rate. MS-CHAPv2 is used as the default authentication method for remote access VPN in Forefront TMG 2010.
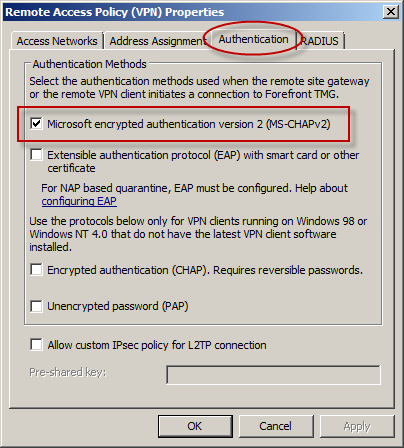
With the public availability of tools to automate the cracking process, PPTP communication using MS-CHAPv2 should be considered unencrypted. There are two options available to mitigate this concern: disable MS-CHAPv2 and enable EAP with PPTP, or disable PPTP and switch to a more secure remote access VPN protocol such as L2TP/IPsec or SSTP. Enabling EAP requires the use of smart cards or certificates for authentication which makes implementation more challenging. SSTP is an excellent option as it leverages SSL/TLS to protect the MS-CHAPv2 authentication process. However, SSTP is only supported on Windows Vista SP1 and later clients. L2TP/IPsec is another good choice, and although it does support certificates it can also be configured using a pre-shared key. If long, complex passwords are used and care is taken to ensure that the password is well protected, it can provide a secure remote access solution.
Hotfix Rollup 1 for Forefront TM 2010 SP2 Now Available
A hotfix rollup for Forefront TMG 2010 SP2 is now available. The hotfix rollup resolves several reported issues with TMG, including:
KB2654016 – A client may be unsuccessful in accessing a Java SSO application published to the web by Forefront TMG 2010
KB2653703 – “Error: Subreport could not be shown” error message in the User Activity or Site Activity report in Forefront TMG 2010
KB2654585 – UDP packets may become backlogged when you increase the “maximum concurrent UDP sessions per IP address” setting in Forefront TMG 2010
KB2624178 – Forefront TMG 2010 administrators may be unable to generate reports
KB2636183 – Both sides of a TCP connection are closed when the client or remote application half-closes the TCP connection in Forefront TMG 2010
KB2653669 – Summary information for the Top Overridden URLs table and for the Top Rule Override Users table display incorrect information in Forefront TMG 2010
KB2617060 – Forefront TMG 2010 enables L2TP site-to-site connections in RRAS
KB2655951 – Japanese characters in the subject line of an Alert email message are not readable in the Japanese version of Forefront TMG 2010
KB2654068 – “The Web Listener is not configured to use SSL” warning message may occur when you configure a Web Listener to use a valid SSL certificate in Forefront TMG 2010
KB2654193 – You receive a “Bad Request” error message when you try to access Outlook Web App published by Forefront TMG 2010
KB2654074 – String comparison may become case-sensitive when you published a website using Forefront TMG 2010
KB2658903 – Forefront TMG 2010 firewall service (wspsrv.exe) may crash frequently for a published website secured by SSL after you install Service Pack 2.
Hotfix rollup 1 for Forefront TMG 2010 SP2 can be downloaded here. After applying this update, the new Forefront TMG 2010 build number will be 7.0.9193.515.





