Archive
Using PowerShell to Determine Forefront TMG Build Number
 Identifying the current build number of your Forefront TMG 2010 installation is critically important when making changes or updates to the system. It is generally recommended that all TMG firewalls be on the same release, so having this information is essential. Many TMG administrators use the TMG management console to gather this information, but I can tell you based on experience that this is not always the most accurate method to use.
Identifying the current build number of your Forefront TMG 2010 installation is critically important when making changes or updates to the system. It is generally recommended that all TMG firewalls be on the same release, so having this information is essential. Many TMG administrators use the TMG management console to gather this information, but I can tell you based on experience that this is not always the most accurate method to use.
I much prefer to gather this information programmatically at the command line. In the past I’ve written about using VBScript to do this, but it’s almost 2016 now and we really should be using PowerShell whenever possible. To that end, here are a few lines of PowerShell code you can use to accurately determine which version and build number your TMG firewall is currently running.
$FPC = New-Object -ComObject FPC.Root $Server = $FPC.GetContainingServer() $Server.ProductVersion

If you’ve done any work at all with VBScript and the TMG’s FPC COM object, you’ll no doubt be able to convert some of your existing scripts to PowerShell. Also, PowerShell, with its tab auto completion, is much more discoverable than using VBScript with COM, so I’m sure you’ll be able to do a lot more with TMG using PowerShell.
Enjoy!
Reminder: Microsoft Reputation Services (MRS) End of Support
 As a reminder to anyone out there still using the URL filtering feature of their Forefront TMG 2010 firewall, the Microsoft Reputation Services (MRS) service, which provides URL categorization for TMG, will no longer be supported after December 31, 2015. After this date, Microsoft will cease updating their URL categorization database. In addition, there are no guarantees from Microsoft that the service will be available in any form, so customers still using this service are strongly encouraged to look for alternative solutions.
As a reminder to anyone out there still using the URL filtering feature of their Forefront TMG 2010 firewall, the Microsoft Reputation Services (MRS) service, which provides URL categorization for TMG, will no longer be supported after December 31, 2015. After this date, Microsoft will cease updating their URL categorization database. In addition, there are no guarantees from Microsoft that the service will be available in any form, so customers still using this service are strongly encouraged to look for alternative solutions.
For many organizations, this means migrating to another platform entirely, which is not a bad idea considering that TMG is nearly six years old now. Alternatively, it is possible to replace TMG’s web filtering component. This can be done on premises by using integrations from various third-party vendors, or by using a cloud-based solution such as Zscaler.
Regardless which path you take, you have just over one month to identify and implement another URL filtering solution. Good luck!
Hotfix Rollup 2 for Forefront UAG 2010 Service Pack 4 Now Available
Hotfix Rollup 2 for Microsoft Forefront UAG 2010 Service Pack 4 is now available for download. This hotfix rollup includes fixes for the following issues:
KB3066351 – Client HTTP connections to a UAG redirect trunk receives errors after you install hotfix rollup 1 for Forefront UAG 2010 SP4
KB3070067 – You may receive an HTTP 503 “Service is Unavailable” error when a connection to a UAG trunk fails in Forefront UAG 2010 SP4
KB3068283 – You may receive HTTP 503 errors on a server that is running Forefront UAG 2010 SP4
KB3068289 – Moving mailboxes as part of a hybrid Office 365 migration fails in Forefront UAG 2010 SP4
You can download Hotfix Rollup 2 for Forefront UAG 2010 SP4 here.
Mitigating the POODLE SSL 3 Vulnerability on Forefront TMG 2010
Recently a new and very serious vulnerability in the SSL 3.0 protocol has been discovered that allows an attacker to recover sensitive information for an encrypted session. The Qualys SSL Labs server test has been updated to identify and warn about this issue.
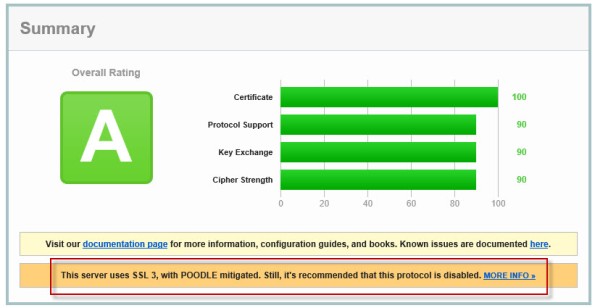
Figure 1 – Qualys SSL Labs Server Test Score for TMG Published Secure Web Site
On a Forefront TMG server with SSL hardening implemented as I’ve outlined here and here, the POODLE attack is mitigated, but it is still recommended that you disable SSL 3.0 altogether. SSL 3.0 is an old, outdated protocol that is no longer widely used, and disabling it should have minimal impact on clients connecting to secure web sites published by the Forefront TMG 2010 firewall.
To disable SSL 3.0 on the TMG firewall, open an elevated PowerShell window and execute the following commands:
New-Item -Path “HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server” -Force
New-ItemProperty -Path “HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server” -PropertyType dword -Value 0 -Name Enabled
Note: Use caution when copying/pasting the above commands as wrapping of the text has occurred.
A restart of the server is required for the change to take effect.
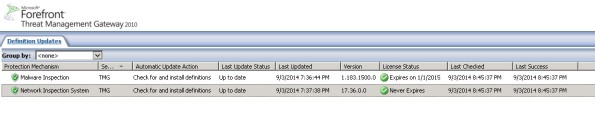
Forefront TMG 2010 Network Inspection System NIS Signature Updates
When Microsoft announced the formal end-of-life for Forefront TMG 2010, they laid out in clear detail the support boundaries for the product going forward. Microsoft stated specifically that they would continue mainstream support for TMG until April of 2015, and extended support would terminate in April 2020. However, the Web Protection Service (WPS) updates for the URL filtering database, antimalware signatures, and the Network Inspection System (NIS) would only continue until December 31, 2015.
Unfortunately, it appears that Microsoft has abandoned the updating for NIS signatures. You may have noticed that a fully updated Forefront TMG firewall with the latest signature updates shows that the last NIS signature was released for security bulletin MS12-050 on July 20, 2012!
I find it difficult to believe that there hasn’t been a single vulnerability discovered or hotfix released since July of 2012 that wouldn’t benefit from NIS protection, so I have to assume that Microsoft is no longer supporting NIS in spite of their pledge to provide support for WPS through the end of 2015. If you are relying on NIS for essential network protection, it’s time to consider deploying a dedicated IDS/IPS solution or another solution that provides this functionality.
Recommended Forefront TMG 2010 SSL and TLS Configuration
Last year I wrote an article for ISAserver.org that provided detailed guidance for improving security for SSL and TLS protected web sites using Forefront TMG 2010. Many people have reached out to me recently to ask about enabling forward secrecy, which my original article did not include because, at the time, it was not recommended to enable it. However, as times have changed, it is now recommended to enable forward secrecy so I recently wrote a short post with guidance on how to do that. The post was written with a very narrow scope and addressed only the enabling of forward secrecy for TLS. Many of you have since asked for guidance on overall security best practices with regard to SSL and TLS along with adding support for forward secrecy. In addition to the configuration changes detailed in my original ISAserver.org article, I also recommend the following list of SSL and TLS cipher suites be explicitly enforced using the method outlined here.
TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256_P256 TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256_P384 TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256_P521 TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384_P384 TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384_P521 TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256_P256 TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA_P256 TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA_P256 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256_P256 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384_P256 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA_P256 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA_P256 TLS_DHE_DSS_WITH_AES_128_CBC_SHA256 TLS_DHE_DSS_WITH_AES_256_CBC_SHA256 TLS_DHE_DSS_WITH_AES_128_CBC_SHA TLS_DHE_DSS_WITH_AES_256_CBC_SHA TLS_RSA_WITH_AES_128_CBC_SHA256 TLS_RSA_WITH_AES_256_CBC_SHA256 TLS_RSA_WITH_AES_128_CBC_SHA TLS_RSA_WITH_AES_256_CBC_SHA
Using this configuration, the Forefront TMG 2010 firewall should receive an A rating from the SSL Labs test site (at the time of this writing).
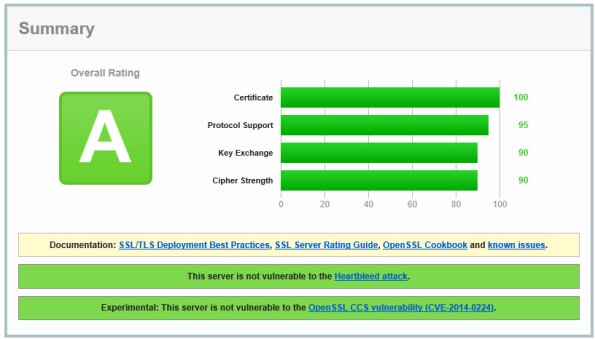
Enabling and supporting the above list of cipher suites will provide the best overall protection and performance for your SSL protected web sites. Note that the list above does not include support for SSL 3.0. If you need to support SSL 3.0 you should add the following cipher suites to the end of the list.
TLS_RSA_WITH_RC4_128_SHA TLS_RSA_WITH_RC4_128_MD5
Please note that this configuration may not work with older browsers on old, unsupported operating systems, for example Internet Explorer 6 on Windows XP. Before deploying this configuration in production I would encourage you to conduct some testing with your supported clients to ensure operability.
Enable TLS Forward Secrecy for Forefront TMG 2010 Published Web Sites
Last year I wrote an article for ISAserver.org that outlined in detail how to improve SSL and TLS security for web sites published using Forefront TMG 2010. In its default configuration, Windows Server 2008 R2 and Forefront TMG leave quite a bit to be desired in terms of SSL and TLS security. In the article I demonstrated how to dramatically improve the security posture of TMG when publishing web sites that use SSL and TLS. At the time I wrote the article it was not recommended to enable forward secrecy, so the changes I originally proposed resulted in an “A” score from the Qualys SSL Labs test site. However, times have changed since then, and with the recent revelations of wide spread government spying, it is now recommended to enable forward secrecy by default. Sites that don’t support forward secrecy will now receive a reduced grade.

To accomplish this on the Forefront TMG 2010 firewall, open the Local Group Policy Editor (gpedit.msc) and navigate to Computer Configuration, Administrative Templates, Network, SSL Configuration Settings. Double-click SSL Cipher Suite Order and choose Enabled. Copy the list of SSL cipher suites to a blank notepad document and then move all of the cipher suites that begin with TLS_ECDHE_RSA_WITH_AES_ to the front of the list. Use caution here because the list cannot have any extra commas, line breaks, or spaces at all. Paste the updated list back in to the SSL Cipher Suites box and click Ok.

The server will have to be restarted for the changes to take effect. Once complete, forward secrecy will now be used by modern browsers and you should once again receive an “A” grade from SSL Labs.

Forefront TMG 2010 Computer Certificate Request or Renewal Fails
When attempting to request or renew a computer certificate on the Forefront TMG 2010 firewall, you may receive the following error message:
Status: Failed The RPC server is unavailable.

This occurs because the Forefront TMG 2010 firewall does not, by default, allow the protocols and ports required to request or renew a certificate from a Certificate Authority (CA). Common workarounds suggest stopping the firewall completely or creating a rule allowing all protocols and ports from the TMG firewall to the CA. However, both of these workarounds are problematic. Stopping the firewall is a manual process that will cause a service disruption. It also leaves the firewall in an unprotected state. For edge deployment scenarios, the underlying operating system will be exposed directly to untrusted networks, which is a serious security risk. Creating an open access rule is not desirable because it violates the basic security principle of least privilege by allowing more access than is required.
To properly address this issue and allow for the secure request and renewal of certificates without disruption and with the least exposure, it will be necessary to create an access rule on the Forefront TMG 2010 firewall to allow all dynamic ports (TCP 49152-65535) from the local host network to the IP address of the CA for all users.
Note: Allowing all dynamic ports (TCP 49152-65535) might also be considered too much access from the Forefront TMG 2010 firewall to the CA. It is possible to restrict the dynamic ports used by TMG and further tighten the access rule, if required. For information about restricting dynamic ports, click here.
In addition to the access rule allowing all dynamic ports, it will also be necessary to make a change to a system policy rule. To do this, right-click the Firewall Policy node in the navigation tree and choose All Tasks, System Policy, and then Edit System Policy. In the Authentication Services group highlight Active Directory and clear the checkbox next to Enforce strict RPC compliance.

Once these changes have been made you can now request or renew a computer certificate on the Forefront TMG 2010 firewall successfully.

Forefront UAG 2010 End of Life Statement
Today, Microsoft announced the end of life for the Forefront UAG 2010 product. Microsoft will continue to provide mainstream support for UAG until April 14, 2015, and extended support until April 14, 2020. Existing customers with active Software Assurance on their existing UAG licenses as of December 1, 2013, may add new UAG server instances, users, and devices without having to purchase additional UAG licenses. In addition, existing customers who have purchased Forefront UAG server licenses will be given upgrade rights to Windows Server 2012 R2, which provides some of the remote access features found in Forefront UAG. For example, Windows Server 2012 R2 supports DirectAccess, client-based VPN, and reverse web proxy with new Web Application Proxy role.
With regard to license upgrade rights, users are entitled to a Windows Server 2012 R2 license for each Forefront UAG server license (or External Connector license) they currently own. Software Assurance for UAG can still be purchased until January 1, 2014. Forefront UAG 2010 will be removed from the pricelist on July 1, 2014. Forefront UAG 2010 will continue to be available from Microsoft OEM hardware partners like Celestix Networks for the foreseeable future, however.
Forefront UAG Service Pack 4 Now Available for Download
Good news! Service Pack 4 (SP4) for Forefront Unified Access Gateway (UAG) 2010 is now available for download. This latest service pack for UAG includes updates to support Windows 8.1 client devices using Internet Explorer 11, the native mail app, and Remote Desktop Connection (RDC) 8.1 client. In addition, SP4 for Forefront UAG 2010 also includes support for publishing RemoteApps from a Remote Desktop Session Host running on Windows Server 2012 or 2012 R2. The service pack also includes fixes for various reported issues.
KB2907776 – The UserMgrCom service crashes intermittently in Forefront UAG 2010
KB2909151 – Trunk authentication fails when the global catalog server is unavailable in Forefront UAG 2010
KB2909168 – The W3wp.exe process randomly stops and causes all sessions to disconnect in Forefront UAG 2010
KB2909182 – “The URL contains an invalid path” error occurs when you try to access an Exchange 2013 OWA website
KB2909191 – You cannot connect to corporate IPv4 resources by using DirectAccess after Forefront UAG 2010 Service Pack 3 is installed
KB2909350 – An SSL VPN application that has the Socket Forwarding mode set to Disabled uses 100 percent of the CPU’s time in Forefront UAG 2010
KB2909353 – You have to authenticate again to the ADFS server when the published server is configured for single sign-on in Forefront UAG 2010
KB2909356 – A detailed HTTP 403.14 error message occurs when you go to a specific InternalSite URL in a Forefront UAG 2010 environment
KB2909365 – A memory leak in W3wp.exe occurs when Outlook Anywhere is published through a Forefront UAG 2010 trunk
KB2909367 – Intermittent HTTP 500 error codes when you access a Forefront UAG 2010 portal
KB2909376 – File uploads do not occur to SharePoint Server 2013 or SkyDrive Pro through Forefront UAG 2010
KB2910407 – An internal 500 error occurs if a custom URL logoff page is configured in Forefront UAG 2010
KB2910413 – Multiple 4625 event IDs are logged when a user logs on in Forefront UAG 2010
KB2910467 – Configuration activation fails on some servers in a large array in Forefront UAG 2010
KB2910498 – A handle leak occurs in Lsass.exe in Forefront UAG 2010
KB2910506 – An authentication prompt is received even though a user is successfully authenticated in Forefront UAG 2010
KB2910517 – An incorrect domain password policy may be used if Active Directory integrated authentication is configured in Forefront UAG 2010
You must have Forefront UAG 2010 SP3 hotfix rollup 1 installed prior to installing SP4. You can download SP3 rollup 1 here. You can download Forefront UAG 2010 SP4 here. Once the update is installed the new Forefront UAG 2010 build number will be 4.0.4083.10000.