Archive
Disable SSL 3.0 and TLS 1.0 on Forefront TMG and UAG 2010
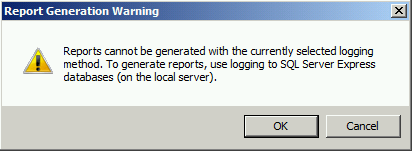
When performing SSL and TLS hardening on Microsoft Forefront Threat Management Gateway (TMG) 2010 or Forefront Unified Access Gateway (UAG) 2010 servers, disabling SSL 3.0 and TLS 1.0 is often required to meet regulatory and compliance guidelines for security. However, disabling SSL 3.0 and TLS 1.0 causes the SQL Server (ISARS) and SQL Server Express services to fail on start up.

Switching from SQL logging to text file logging can be employed as a workaround. However, when using text file logging, generating historical reports in the TMG management console is no longer supported.
To restore full functionality for SQL logging and reporting when SSL 3.0 and TLS 1.0 are both disabled, an update to the local security policy of the server is required. Open the Local Security Policy editor by clicking on the Start button and navigating to Administrative Tools and Local Security Policy. Expand Local Policies and click on Security Options. Double-click on System cryptography: Use FIPS compliant algorithms for encryption, hashing, and signing. Click Enabled and then click OK.

Restart the computer for the changes to take effect. Once complete, all SQL services should start and run without issue.
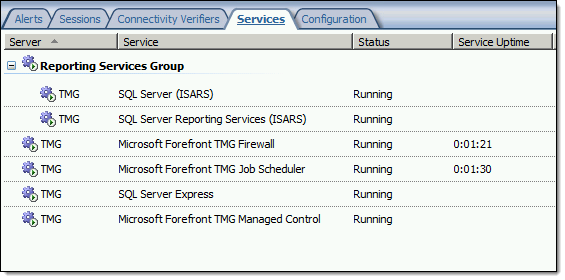
Note: If Remote Desktop Services (RDS) is used to manage the Forefront TMG firewall it will be necessary to install update KB3080079.
Improving SSL Security for Forefront TMG 2010 Published Web Sites
Recently I wrote an article for ISAserver.org entitled Improving SSL Security for Forefront TMG 2010 Published Web Sites. In the article I demonstrate how to evaluate the current security configuration of your Forefront TMG firewall for published SSL web sites and how to make changes to the default settings in order to improve the overall security posture of TMG in reverse proxy scenarios. Implementing these changes will provide dramatically improved protection for Forefront TMG published SSL web sites. The steps outlined in the article include details for changes to be made to specific registry entries on the Forefront TMG 2010 firewall. I’ve had a number of requests to make the registry file available for download in order to simplify the process and ensure that these changes are made correctly. You can download the registry file used in the ISAserver.org post here. Enjoy!




