Archive
Microsoft Reputation Services (MRS) Offline after December 31, 2015
 As I recently mentioned, Microsoft has discontinued and will be terminating their Microsoft Reputation Services (MRS) cloud URL categorization service on or shortly after December 31, 2015. Today, Microsoft released additional information vital to TMG administrators everywhere who are still relying on this service for URL filtering. Specifically, what happens with TMG once Microsoft officially turns off MRS and it is no longer available?
As I recently mentioned, Microsoft has discontinued and will be terminating their Microsoft Reputation Services (MRS) cloud URL categorization service on or shortly after December 31, 2015. Today, Microsoft released additional information vital to TMG administrators everywhere who are still relying on this service for URL filtering. Specifically, what happens with TMG once Microsoft officially turns off MRS and it is no longer available?
Bad things.
First, any firewall rules that rely on URL categorization to allow traffic will fail closed. That is, they will block all traffic. Second, any rules using URL categorization to deny traffic will fail open and allow that traffic instead. Finally, there is potential performance degradation that may occur with TMG after the service is disabled by Microsoft.
What to do?
First, update any TMG firewall rules that use URL Categories or URL Category Sets. You can replace them with Domain Name Sets or URL Sets, if desired. Next, disable the use of URL filtering in TMG by opening the TMG management console, right-clicking Web Access Policy and choosing Configure and then URL Filtering. Uncheck the box next to Enable URL Filtering and then click Ok.

Finally, consider a replacement solution for TMG’s URL filtering. There are a number of solutions available, both on-premises and cloud-based, that are capable replacements. The Zscaler solution is highly effective, and if you’re looking for a low-buck alternative, consider something like OpenDNS. There are many more, I’m sure.
Good luck!
Forefront TMG 2010 SQL Services Fail to Start After Disabling SSL 3.0
When performing POODLE attack mitigation on the Forefront TMG 2010 firewall by disabling SSL 3.0, you may encounter a scenario in which TMG’s SQL services fail to start after a reboot.

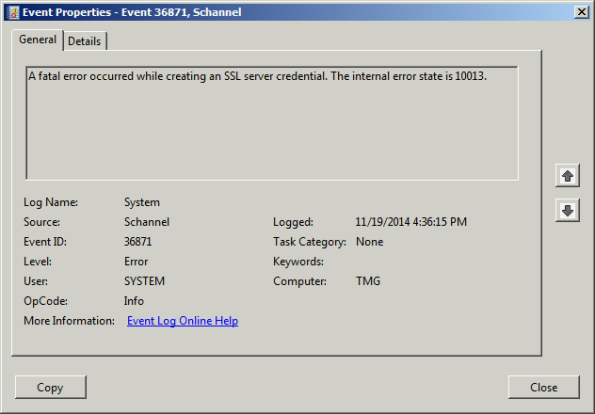
Looking through the Windows system event log you may see an error message logged by the Service Control Manager with event ID 36871 which states:
A fatal error occurred while creating an SSL server credential. The internal error state is 10013.
In addition you may also see an error message logged by the Service Control Manager with event ID 7024 which states:
The SQL Server (ISARS) service terminated with service-specific error %%-2146893007.

This can occur when SSL 3.0 is disabled at the same time that TLS 1.0 is also disabled. Even though TLS 1.1 and 1.2 might be enabled, TMG requires that TLS 1.0 specifically be enabled for SQL server services to function properly when SSL 3.0 is disabled.
To resolve this issue, enable TLS 1.0 Server in the registry by changing the value of Enabled to 1, as shown here. If these registry keys do not exist, create them.

Restart the server for the change to take effect.
Forefront TMG 2010 Network Inspection System NIS Signature Updates
When Microsoft announced the formal end-of-life for Forefront TMG 2010, they laid out in clear detail the support boundaries for the product going forward. Microsoft stated specifically that they would continue mainstream support for TMG until April of 2015, and extended support would terminate in April 2020. However, the Web Protection Service (WPS) updates for the URL filtering database, antimalware signatures, and the Network Inspection System (NIS) would only continue until December 31, 2015.
Unfortunately, it appears that Microsoft has abandoned the updating for NIS signatures. You may have noticed that a fully updated Forefront TMG firewall with the latest signature updates shows that the last NIS signature was released for security bulletin MS12-050 on July 20, 2012!
I find it difficult to believe that there hasn’t been a single vulnerability discovered or hotfix released since July of 2012 that wouldn’t benefit from NIS protection, so I have to assume that Microsoft is no longer supporting NIS in spite of their pledge to provide support for WPS through the end of 2015. If you are relying on NIS for essential network protection, it’s time to consider deploying a dedicated IDS/IPS solution or another solution that provides this functionality.
Recommended Forefront TMG 2010 SSL and TLS Configuration
Last year I wrote an article for ISAserver.org that provided detailed guidance for improving security for SSL and TLS protected web sites using Forefront TMG 2010. Many people have reached out to me recently to ask about enabling forward secrecy, which my original article did not include because, at the time, it was not recommended to enable it. However, as times have changed, it is now recommended to enable forward secrecy so I recently wrote a short post with guidance on how to do that. The post was written with a very narrow scope and addressed only the enabling of forward secrecy for TLS. Many of you have since asked for guidance on overall security best practices with regard to SSL and TLS along with adding support for forward secrecy. In addition to the configuration changes detailed in my original ISAserver.org article, I also recommend the following list of SSL and TLS cipher suites be explicitly enforced using the method outlined here.
TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256_P256 TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256_P384 TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256_P521 TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384_P384 TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384_P521 TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256_P256 TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA_P256 TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA_P256 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256_P256 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384_P256 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA_P256 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA_P256 TLS_DHE_DSS_WITH_AES_128_CBC_SHA256 TLS_DHE_DSS_WITH_AES_256_CBC_SHA256 TLS_DHE_DSS_WITH_AES_128_CBC_SHA TLS_DHE_DSS_WITH_AES_256_CBC_SHA TLS_RSA_WITH_AES_128_CBC_SHA256 TLS_RSA_WITH_AES_256_CBC_SHA256 TLS_RSA_WITH_AES_128_CBC_SHA TLS_RSA_WITH_AES_256_CBC_SHA
Using this configuration, the Forefront TMG 2010 firewall should receive an A rating from the SSL Labs test site (at the time of this writing).
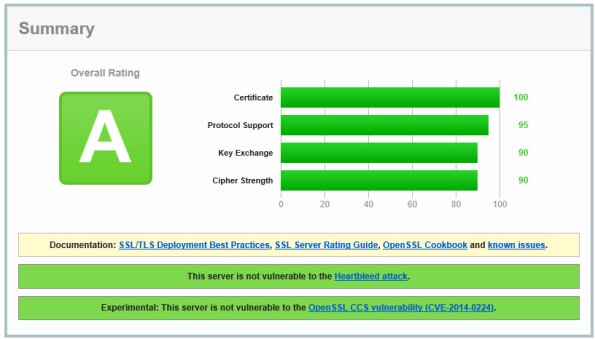
Enabling and supporting the above list of cipher suites will provide the best overall protection and performance for your SSL protected web sites. Note that the list above does not include support for SSL 3.0. If you need to support SSL 3.0 you should add the following cipher suites to the end of the list.
TLS_RSA_WITH_RC4_128_SHA TLS_RSA_WITH_RC4_128_MD5
Please note that this configuration may not work with older browsers on old, unsupported operating systems, for example Internet Explorer 6 on Windows XP. Before deploying this configuration in production I would encourage you to conduct some testing with your supported clients to ensure operability.
Enable TLS Forward Secrecy for Forefront TMG 2010 Published Web Sites
Last year I wrote an article for ISAserver.org that outlined in detail how to improve SSL and TLS security for web sites published using Forefront TMG 2010. In its default configuration, Windows Server 2008 R2 and Forefront TMG leave quite a bit to be desired in terms of SSL and TLS security. In the article I demonstrated how to dramatically improve the security posture of TMG when publishing web sites that use SSL and TLS. At the time I wrote the article it was not recommended to enable forward secrecy, so the changes I originally proposed resulted in an “A” score from the Qualys SSL Labs test site. However, times have changed since then, and with the recent revelations of wide spread government spying, it is now recommended to enable forward secrecy by default. Sites that don’t support forward secrecy will now receive a reduced grade.

To accomplish this on the Forefront TMG 2010 firewall, open the Local Group Policy Editor (gpedit.msc) and navigate to Computer Configuration, Administrative Templates, Network, SSL Configuration Settings. Double-click SSL Cipher Suite Order and choose Enabled. Copy the list of SSL cipher suites to a blank notepad document and then move all of the cipher suites that begin with TLS_ECDHE_RSA_WITH_AES_ to the front of the list. Use caution here because the list cannot have any extra commas, line breaks, or spaces at all. Paste the updated list back in to the SSL Cipher Suites box and click Ok.

The server will have to be restarted for the changes to take effect. Once complete, forward secrecy will now be used by modern browsers and you should once again receive an “A” grade from SSL Labs.

Hotfix Rollup 5 for Forefront TMG 2010 SP2 Now Available
Hotfix rollup 5 for Microsoft Forefront TMG 2010 with Service pack 2 (SP2) is now available for download. This latest hotfix rollup includes fixes for the following issues:
KB2963805 – Account lockout alerts are not logged after you install Rollup 4 for Forefront TMG 2010 SP2
KB2963811 – The Forefront TMG 2010 Firewall service (wspsrv.exe) may crash when the DiffServ filter is enabled
KB2963823 – “1413 Invalid Index” after you enable cookie sharing across array members in Forefront TMG 2010
KB2963834 – HTTPS traffic may not be inspected when a user accesses a site through Forefront TMG 2010
KB2967726 – New connections are not accepted on a specific web proxy or web listener in Forefront TMG 2010
KB2965004 – EnableSharedCookie option doesn’t work if the Forefront TMG 2010 service runs under a specific account
KB2932469 – An incorrect value is used for IPsec Main Mode key lifetime in Threat Management Gateway 2010
KB2966284 – A zero value is always returned when an average counter of the “Forefront TMG Web Proxy” object is queried from the .NET Framework
KB2967763 – The “Const SE_VPS_VALUE = 2” setting does not work for users if the UPN is not associated with a real domain
KB2973749 – HTTP Connectivity Verifiers return unexpected failures in TMG 2010
You can download hotfix rollup 5 for Forefront TMG 2010 SP2 here. After applying this update, the new Forefront TMG 2010 build number will be 7.0.9193.644.
Improving SSL Security for Forefront TMG 2010 Published Web Sites
Recently I wrote an article for ISAserver.org entitled Improving SSL Security for Forefront TMG 2010 Published Web Sites. In the article I demonstrate how to evaluate the current security configuration of your Forefront TMG firewall for published SSL web sites and how to make changes to the default settings in order to improve the overall security posture of TMG in reverse proxy scenarios. Implementing these changes will provide dramatically improved protection for Forefront TMG published SSL web sites. The steps outlined in the article include details for changes to be made to specific registry entries on the Forefront TMG 2010 firewall. I’ve had a number of requests to make the registry file available for download in order to simplify the process and ensure that these changes are made correctly. You can download the registry file used in the ISAserver.org post here. Enjoy!
Extending the Life of Forefront TMG 2010 with Zscaler Cloud Based Security
Forefront TMG End of Life
With the end of life announcement for Microsoft Forefront TMG 2010, one of the most common questions I am asked is “What should I replace my Forefront TMG firewall with?” Many are surprised when I reply “Why do you want to replace it?” Simply because Forefront TMG will not be developed in the future does not mean there’s an immediate need to replace it. Considering the fact that Forefront TMG mainstream support extends until April 2015, and extended support lasts until April 2020, often the decision to replace TMG is nothing more than a knee-jerk reaction to marketing pressure by vendors of competing solutions.
Do You Need to Replace Forefront TMG 2010 Now?
If you have deployed Forefront TMG 2010 as a firewall, basic forward or reverse web proxy, or remote access or site-to-site VPN, there is no need to replace Forefront TMG 2010 right now. All of the features used in these deployment scenarios will continue to function in to perpetuity. You have until April 2020 to find a replacement for Forefront TMG, which should give you plenty of time to consider alternative solutions. However, if you have deployed Forefront TMG as a secure web gateway, the situation is a little different. Although support for the product extends until April 2020, the Web Protection Service (WPS) subscription will only function until the end of 2015. This means that URL filtering reputation database updates, antimalware signatures, and Network Inspection System (NIS) signatures will no longer be updated past this time. Not to worry, there are some excellent cloud-based security solutions that can be integrated with Forefront TMG 2010 to effectively extend the life of TMG for the foreseeable future.
Extending the Life of Forefront TMG 2010 with Zscaler
Recently I had the opportunity to evaluate the Zscaler Cloud-based security solution. Zscaler provides security-as-a-service and integrates seamlessly with Forefront TMG to provide essential web security protection with URL filtering, dynamic web content control, virus and malicious software scanning, HTTPS inspection capabilities, and more. The Zscaler security solution provides significantly more protection than the native Forefront TMG technologies offer. There are also tremendous economies of scale to be gained by using this cloud-based security solution, as Zscaler has more than 4000 enterprise customers in 180 countries, servicing more than 10 million users globally. The threat intelligence gained from having such a broad view of Internet activity worldwide enables Zscaler to quickly identify emerging threats on a global basis and extend protection to all of its customers quickly and effectively.
Zscaler Integration with Forefront TMG 2010
Integrating an on-premises Forefront TMG firewall with the Zscaler cloud is accomplished without having to install a plug-in on the TMG firewall. On-premises web traffic is delivered to the Zscaler cloud service by Forefront TMG through the use of web proxy chaining rules. After you’ve signed up for the service, simply configure a web proxy chaining rule to forward web proxy requests from Forefront TMG to the Zscaler cloud proxy gateways.

Zscaler Protection for Mobile Users
The Zscaler solution has some additional advantages over Forefront TMG’s native web protection mechanisms. With a cloud-based solution, Zscaler’s protection can also be extended transparently to mobile users, keeping them safe regardless of where they are. Zscaler has more than 100 datacenters worldwide, ensuring quick response times and low latency wherever the mobile user happens to be. Integrating individual clients can be done using proxy PAC files to route traffic to Zscaler’s datacenters. Additionally there is an option to install an agent on the client to forward traffic, which has the benefit of preventing the end user from disabling proxy settings to bypass content filtering restrictions.
Forefront TMG 2010 and Zscaler – Better Together
You may be asking yourself “Why not just use Zscaler exclusively? Why do I need TMG at all?” Valid question! Integrating Zscaler with Forefront TMG provides the best of both worlds in terms of security and performance. With Forefront TMG 2010 on premises, you have a Common Criteria-certified enterprise-class firewall to provide the highest level of security for your network. You can leverage strong user and group-based authentication, and you gain the added benefit of local caching for web content. In addition, you can make use of Forefront TMG 2010’s other features like multi-networking to create perimeter or DMZ networks for isolating public-facing services, reverse proxy for on-premises web-based and non-web based applications and services, remote access VPN for managed and non-managed mobile users, and site-to-site VPN to connect remote offices, business partners, or cloud service providers.
Forefront TMG End of Sale? Not Quite!
Although Microsoft is committed to supporting Forefront TMG 2010 for many years to come, they are no longer selling Forefront TMG 2010 licenses or the Web Protection Service (WPS) subscription licenses. If you’ve already deployed Forefront TMG 2010, or have already purchased Forefront TMG processor licenses and the WPS subscription, you have nothing to worry about. If you’re looking to deploy Forefront TMG 2010 today, you can’t purchase licenses for the software from Microsoft. However, you can still obtain Forefront TMG 2010 through a Microsoft OEM partner like Celestix Networks. (Full disclosure: Celestix Networks is my current employer.)
Keep Calm and Carry On
In my estimation, you can safely deploy or keep Forefront TMG 2010 in your environment and still gain a healthy return on your investment for many years to come. If you’re using Forefront TMG for publishing services such as Outlook Web App (OWA) or SharePoint, or you’re leveraging client-based remote access or site-to-site VPN, you have nothing to worry about. If you’re using Forefront TMG as a secure web gateway, you can enhance and extend the solution by using Zscaler’s cloud-based security solution for less than you would have paid for the Microsoft WPS subscription. No need to go out and replace your Forefront TMG 2010 solution for quite a few more years! If you are considering a new deployment, you can still purchase Forefront TMG 2010 from Microsoft OEM partners like Iron Networks. So Keep Calm and Deploy Forefront TMG 2010 today!

Citrix NetScaler Forefront TMG 2010 Replacement White Paper
With the formal end of life announcement for Forefront TMG 2010 last year, many firewall and secure web gateway vendors have been touting themselves as replacements for TMG. The folks at Citrix recently made available a white paper [PDF] making their case as a comprehensive replacement for Forefront TMG. While I don’t have any personal experience with the NetScaler solution, it does appear to have many of the features that TMG administrators have come to rely upon, such as URL filtering, virus and malicious software inspection, SSL termination (HTTPS inspection), content caching, low-level intrusion detection and prevention, and VPN capabilities. In addition, the NetScaler supports flexible network placement with edge, back firewall, and unihomed (single-legged or one-arm) deployment options. The solution is available in both hardware appliance form factor and virtual appliance.
Citrix makes an attempt to position their solution as the ideal and comprehensive replacement for Forefront TMG, and while it does have many features that TMG provides there is one glaring omission – an alternative to the Forefront TMG Firewall Client. ISA and TMG administrators have long used the Firewall Client to provide seamless and transparent proxy services for Winsock applications. The firewall client enables fully authenticated proxy support for non-web based protocols, and it appears that the NetScaler does not include such capabilities.
As with most white papers comparing solutions like this, it is helpful to understand they are essentially marketing material designed to downplay the features of the competing solution while often embellishing their own features. There are also some inaccuracies with regard to Forefront TMG capabilities, which is also not uncommon in documents such as these. For example, the document states that Forefront TMG 2010 failover requires three nodes, which is incorrect. You can easily create a standalone array using Forefront TMG 2010 Enterprise Edition using two nodes.
Overall the Citrix NetScaler looks like a pretty good solution. If you are in the market today for an alternative to Forefront TMG 2010 (…and should you be? That’s a topic for a future post, so stay tuned!) then download their white paper and take a closer look.
Identifying and Reducing Anonymous Traffic Allowed by Forefront TMG 2010
My recent blog post about altering the SafeSearch enforcement rule in Forefront TMG 2010 to require authentication has sparked some discussion on Twitter and Facebook regarding unauthenticated, anonymous access, particularly to resources located on the public Internet. In a perfect world (ok, my perfect world!), all access to and through the TMG firewall would be fully authenticated. Unfortunately, for a variety of reasons, this isn’t achievable. To start, authenticating all traffic to and through the TMG firewall would necessitate that all clients be configured as explicit web proxy clients. In addition, if non web-based protocols are allowed by firewall policy the Firewall Client would need to be distributed to all clients. While this is ideal if we’re designing a solution on paper, in the real world many administrators don’t have the luxury of forcing proxy configuration or installing the Firewall Client on all their systems. For example, some systems may not be under the administrator’s control or they may be required to support non web-based protocols on platforms other than Windows, for which the Firewall Client is not supported. Also, as veteran ISA and TMG firewall administrators know all too well, there are some applications that simply don’t play nice with an authenticating proxy, even with the Firewall Client installed. Applications that don’t leverage Winsock for network communication or that use IP-based protocols such as ICMP or GRE also prevent us from realizing our goal of authenticating all network traffic through TMG. Windows Update traffic also poses challenges for authenticating all TMG traffic, as the Windows Update service often makes requests to the Internet for updates in the background and perhaps even if there is no interactive user logged on.
Just because out of necessity some traffic has to be allowed through the TMG firewall anonymously doesn’t mean that undertaking an effort to reduce unauthenticated traffic isn’t a worthwhile project. If you’re interested in doing something like this, have a look at the Fastvue blog and read Scott Glew’s excellent article detailing how to use TMG Reporter to identify and reduce unauthenticated traffic on the Forefront TMG 2010 firewall. Not using TMG Reporter? You’re missing out! Download a free evaluation here!