Archive
Implementing DirectAccess with Windows Server 2016 Now Available
I am very excited to announce that my new DirectAccess book, “Implementing DirectAccess with Windows Server 2016“ from Apress media, is now shipping! The book is available on popular online sites like Amazon.com, Barnes & Noble, Springer.com, Apress.com, and others. The book is also available in electronic formats such as Amazon Kindle and Barnes & Noble Nook, as well as a variety of subscription formats including Safari, Books24x7, and SpringerLink.
This book contains detailed and prescriptive guidance for the planning, design, implementation, and support of a DirectAccess remote access solution on Windows Server 2016. It also includes valuable insight, tips, tricks, and best practice recommendations gained from my many years of deploying DirectAccess for some of the largest organizations in the world.
Current DirectAccess administrators will also find this book helpful, as the majority of content is still applicable to DirectAccess in Windows Server 2012 and Windows Server 2012 R2. In addition, the book also includes essential information on the design and deployment of highly available and geographically redundant DirectAccess deployments.
Troubleshooting DirectAccess can be a daunting task, so I’ve dedicated an entire chapter in the book to this topic. For those responsible for the maintenance and support of DirectAccess in their organization, this chapter alone will be worth the investment.
Be sure to order your copy today!
Publish DirectAccess with Forefront TMG 2010
DirectAccess is a compelling remote access solution that provides seamless and transparent, always-on, bi-directional remote corporate network connectivity for managed Windows clients. In Windows Server 2008 R2 and Forefront Unified Access Gateway (UAG) 2010, the DirectAccess server had to be configured with two network adapters, with the external network interface configured with two consecutive public IPv4 addresses. Many security engineers were understandably concerned about exposing a domain-joined Windows server directly to the public Internet, which limited the adoption of the technology. Beginning with Windows Server 2012, DirectAccess is integrated in to the operating system and provides more flexible network configuration. DirectAccess can now be deployed behind an existing edge security solution performing NAT, and even supports single-NIC configuration.
The Forefront TMG 2010 firewall is an excellent choice to provide essential protection for the DirectAccess workload. When DirectAccess is deployed behind a NAT device, the only firewall port that needs to be opened is TCP port 443 (HTTPS).
When publishing DirectAccess with TMG, it is important to use a server publishing rule and not a web publishing rule. To publish DirectAccess, open the Forefront TMG 2010 management console, right-click Firewall Policy in the navigation tree, and then choose New Non-Web Server Publishing Rule.
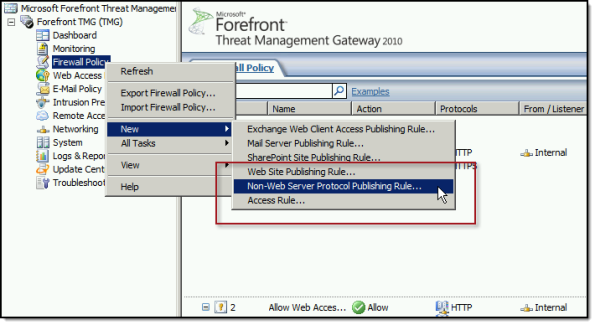
Provide a descriptive name for the rule, enter the IP address of the DirectAccess server, choose HTTPS Server for the protocol, and then select the network interface on which to listen for these requests.
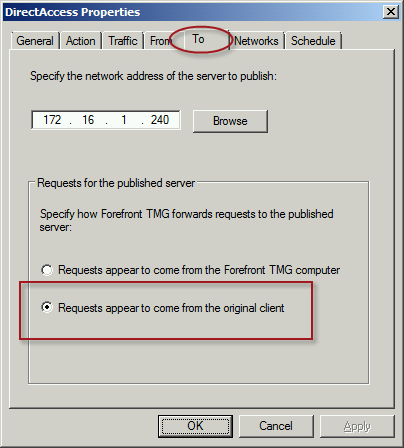
To ensure the proper operation of Receive Side Scaling (RSS) on the DirectAccess server, it is recommended that the server be configured to use TMG as its default gateway and to configure the publishing rule on TMG using the option Requests appear to come from the original client.
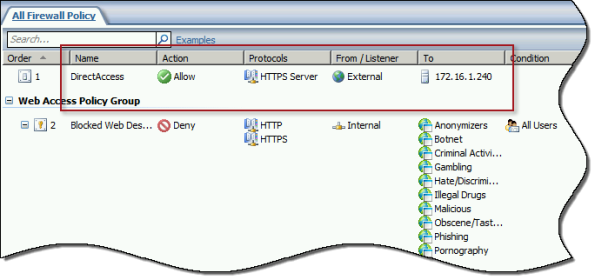
Also, TMG does not support load balancing for server publishing rules, so it is not possible to deliver traffic to multiple back end servers using TMG. For high availability and to provide for scalability, it is recommended to configure load balancing for DirectAccess using NLB or an external load balancer (recommended) and publish the virtual IP address (VIP) using the steps described above.
To learn more about DirectAccess, visit http://directaccess.richardhicks.com/
Hotfix Rollup 5 for Forefront TMG 2010 SP2 Now Available
Hotfix rollup 5 for Microsoft Forefront TMG 2010 with Service pack 2 (SP2) is now available for download. This latest hotfix rollup includes fixes for the following issues:
KB2963805 – Account lockout alerts are not logged after you install Rollup 4 for Forefront TMG 2010 SP2
KB2963811 – The Forefront TMG 2010 Firewall service (wspsrv.exe) may crash when the DiffServ filter is enabled
KB2963823 – “1413 Invalid Index” after you enable cookie sharing across array members in Forefront TMG 2010
KB2963834 – HTTPS traffic may not be inspected when a user accesses a site through Forefront TMG 2010
KB2967726 – New connections are not accepted on a specific web proxy or web listener in Forefront TMG 2010
KB2965004 – EnableSharedCookie option doesn’t work if the Forefront TMG 2010 service runs under a specific account
KB2932469 – An incorrect value is used for IPsec Main Mode key lifetime in Threat Management Gateway 2010
KB2966284 – A zero value is always returned when an average counter of the “Forefront TMG Web Proxy” object is queried from the .NET Framework
KB2967763 – The “Const SE_VPS_VALUE = 2” setting does not work for users if the UPN is not associated with a real domain
KB2973749 – HTTP Connectivity Verifiers return unexpected failures in TMG 2010
You can download hotfix rollup 5 for Forefront TMG 2010 SP2 here. After applying this update, the new Forefront TMG 2010 build number will be 7.0.9193.644.
Forefront UAG 2010 End of Life Statement
Today, Microsoft announced the end of life for the Forefront UAG 2010 product. Microsoft will continue to provide mainstream support for UAG until April 14, 2015, and extended support until April 14, 2020. Existing customers with active Software Assurance on their existing UAG licenses as of December 1, 2013, may add new UAG server instances, users, and devices without having to purchase additional UAG licenses. In addition, existing customers who have purchased Forefront UAG server licenses will be given upgrade rights to Windows Server 2012 R2, which provides some of the remote access features found in Forefront UAG. For example, Windows Server 2012 R2 supports DirectAccess, client-based VPN, and reverse web proxy with new Web Application Proxy role.
With regard to license upgrade rights, users are entitled to a Windows Server 2012 R2 license for each Forefront UAG server license (or External Connector license) they currently own. Software Assurance for UAG can still be purchased until January 1, 2014. Forefront UAG 2010 will be removed from the pricelist on July 1, 2014. Forefront UAG 2010 will continue to be available from Microsoft OEM hardware partners like Celestix Networks for the foreseeable future, however.
Windows Azure Multifactor Authentication and Forefront TMG 2010
When Microsoft first announced Windows Azure Multi-Factor Authentication, a cloud-based strong authentication solution, my first thought was “I wonder if it works with Forefront TMG 2010?” Being cloud-based, my first thought was perhaps not. However, once I started digging in to it I quickly learned that it includes a software component that can be installed on-premises and will even integrate with on-premises security solutions via a number of interfaces, including RADIUS. Forefront TMG 2010 has supported RADIUS authentication for many years, so I put together a test lab and in no time at all I had Windows Azure multi-factor authentication working with Forefront TMG 2010 remote access VPN. Forefront TMG 2010 integrated with Windows Azure multi-factor authentication provides the highest level of protection for remote access users. Leveraging Windows Azure cloud-based strong authentication is extremely cost effective, with very low per user or per authentication costs and no on-premises hardware to purchase. The Windows Azure public cloud, which is ISO/IEC27001:2005 certified, provides the most secure and reliable strong authentication service available today. To learn how to configure Forefront TMG 2010 to work with Windows Azure multi-factor authentication, click here.
Publishing Exchange 2013 Outlook Web App with Forefront TMG 2010
Recently I wrote an article for ISAserver.org about publishing Exchange 2013 Outlook Web App (OWA) using Forefront TMG 2010. In spite of the fact that many organizations are migrating their e-mail services to the cloud, there are many organizations who cannot, for a variety of reasons, take advantage of cloud services for e-mail. This makes Exchange 2013 a compelling upgrade for many companies. Historically Forefront TMG 2010 and its predecessors were the go-to service for securing access to on-premises Exchange implementations. Forefront TMG 2010 supports OWA publishing with native publishing wizards, allowing you to select which version of Exchange you are publishing, with the added bonus of providing in-box forms-based authentication (FBA) templates that matched the look and feel of the Exchange version you were publishing. Since Forefront TMG 2010 has been deprecated, Microsoft has not updated Forefront TMG 2010 to include support for Exchange 2013 OWA. However, you can still publish Exchange 2013 OWA using Forefront TMG by following the instructions outlined in my ISAserver.org post. When using this method, the Exchange 2010 FBA templates are used. This makes the user experience somewhat disjointed, with the FBA pages not matching the new, updated look and feel of OWA 2013. To remedy this, I reached out to my good friend Scott Glew at Fastvue. Scott is a terrific web developer, as evidenced by the amazing UI included with the TMG Reporter solution. In short order, Scott whipped up some customized Forefront TMG 2010 FBA templates to match the look and feel of OWA 2013 and has made them available for free. Now if you’re publishing Exchange 2013 OWA using Forefront TMG 2010, you can download these custom templates and use them to provide a consistent experience for your Exchange OWA users. Enjoy!
Extending the Life of Forefront TMG 2010 with Zscaler Cloud Based Security
Forefront TMG End of Life
With the end of life announcement for Microsoft Forefront TMG 2010, one of the most common questions I am asked is “What should I replace my Forefront TMG firewall with?” Many are surprised when I reply “Why do you want to replace it?” Simply because Forefront TMG will not be developed in the future does not mean there’s an immediate need to replace it. Considering the fact that Forefront TMG mainstream support extends until April 2015, and extended support lasts until April 2020, often the decision to replace TMG is nothing more than a knee-jerk reaction to marketing pressure by vendors of competing solutions.
Do You Need to Replace Forefront TMG 2010 Now?
If you have deployed Forefront TMG 2010 as a firewall, basic forward or reverse web proxy, or remote access or site-to-site VPN, there is no need to replace Forefront TMG 2010 right now. All of the features used in these deployment scenarios will continue to function in to perpetuity. You have until April 2020 to find a replacement for Forefront TMG, which should give you plenty of time to consider alternative solutions. However, if you have deployed Forefront TMG as a secure web gateway, the situation is a little different. Although support for the product extends until April 2020, the Web Protection Service (WPS) subscription will only function until the end of 2015. This means that URL filtering reputation database updates, antimalware signatures, and Network Inspection System (NIS) signatures will no longer be updated past this time. Not to worry, there are some excellent cloud-based security solutions that can be integrated with Forefront TMG 2010 to effectively extend the life of TMG for the foreseeable future.
Extending the Life of Forefront TMG 2010 with Zscaler
Recently I had the opportunity to evaluate the Zscaler Cloud-based security solution. Zscaler provides security-as-a-service and integrates seamlessly with Forefront TMG to provide essential web security protection with URL filtering, dynamic web content control, virus and malicious software scanning, HTTPS inspection capabilities, and more. The Zscaler security solution provides significantly more protection than the native Forefront TMG technologies offer. There are also tremendous economies of scale to be gained by using this cloud-based security solution, as Zscaler has more than 4000 enterprise customers in 180 countries, servicing more than 10 million users globally. The threat intelligence gained from having such a broad view of Internet activity worldwide enables Zscaler to quickly identify emerging threats on a global basis and extend protection to all of its customers quickly and effectively.
Zscaler Integration with Forefront TMG 2010
Integrating an on-premises Forefront TMG firewall with the Zscaler cloud is accomplished without having to install a plug-in on the TMG firewall. On-premises web traffic is delivered to the Zscaler cloud service by Forefront TMG through the use of web proxy chaining rules. After you’ve signed up for the service, simply configure a web proxy chaining rule to forward web proxy requests from Forefront TMG to the Zscaler cloud proxy gateways.
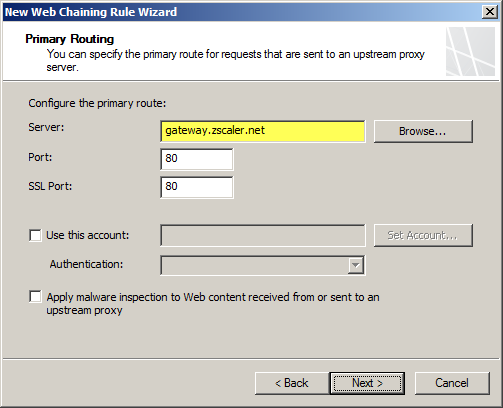

Zscaler Protection for Mobile Users
The Zscaler solution has some additional advantages over Forefront TMG’s native web protection mechanisms. With a cloud-based solution, Zscaler’s protection can also be extended transparently to mobile users, keeping them safe regardless of where they are. Zscaler has more than 100 datacenters worldwide, ensuring quick response times and low latency wherever the mobile user happens to be. Integrating individual clients can be done using proxy PAC files to route traffic to Zscaler’s datacenters. Additionally there is an option to install an agent on the client to forward traffic, which has the benefit of preventing the end user from disabling proxy settings to bypass content filtering restrictions.
Forefront TMG 2010 and Zscaler – Better Together
You may be asking yourself “Why not just use Zscaler exclusively? Why do I need TMG at all?” Valid question! Integrating Zscaler with Forefront TMG provides the best of both worlds in terms of security and performance. With Forefront TMG 2010 on premises, you have a Common Criteria-certified enterprise-class firewall to provide the highest level of security for your network. You can leverage strong user and group-based authentication, and you gain the added benefit of local caching for web content. In addition, you can make use of Forefront TMG 2010’s other features like multi-networking to create perimeter or DMZ networks for isolating public-facing services, reverse proxy for on-premises web-based and non-web based applications and services, remote access VPN for managed and non-managed mobile users, and site-to-site VPN to connect remote offices, business partners, or cloud service providers.
Forefront TMG End of Sale? Not Quite!
Although Microsoft is committed to supporting Forefront TMG 2010 for many years to come, they are no longer selling Forefront TMG 2010 licenses or the Web Protection Service (WPS) subscription licenses. If you’ve already deployed Forefront TMG 2010, or have already purchased Forefront TMG processor licenses and the WPS subscription, you have nothing to worry about. If you’re looking to deploy Forefront TMG 2010 today, you can’t purchase licenses for the software from Microsoft. However, you can still obtain Forefront TMG 2010 through a Microsoft OEM partner like Celestix Networks. (Full disclosure: Celestix Networks is my current employer.)
Keep Calm and Carry On
In my estimation, you can safely deploy or keep Forefront TMG 2010 in your environment and still gain a healthy return on your investment for many years to come. If you’re using Forefront TMG for publishing services such as Outlook Web App (OWA) or SharePoint, or you’re leveraging client-based remote access or site-to-site VPN, you have nothing to worry about. If you’re using Forefront TMG as a secure web gateway, you can enhance and extend the solution by using Zscaler’s cloud-based security solution for less than you would have paid for the Microsoft WPS subscription. No need to go out and replace your Forefront TMG 2010 solution for quite a few more years! If you are considering a new deployment, you can still purchase Forefront TMG 2010 from Microsoft OEM partners like Iron Networks. So Keep Calm and Deploy Forefront TMG 2010 today!

DirectAccess Session at Microsoft TechEd 2013
This month I had the honor and privilege to present a Windows Server 2012 DirectAccess session at Microsoft TechEd North America and Europe 2013. For those of you who attended in person, thank you very much! I certainly hope that you found the session informative and worthwhile. For those of you who were not able to attend in person, you can watch a recording of the session for free at Microsoft’s MSDN Channel 9 web site here. Enjoy!
Forefront UAG 2010 Video Training Course Now Available
I’m happy to announce that my latest Trainsignal video training course is now available! This new video training course is on Forefront Unified Access Gateway (UAG) 2010. It is an introductory course on Forefront UAG designed to teach network engineers and security administrators the basic essentials of planning, preparing, installing, configuring, monitoring, and maintain a Forefront UAG 2010 remote access solution. In the course I demonstrate how to publish popular Microsoft on-premises applications like SharePoint and Exchange Outlook Web App (OWA). In addition I cover publishing Remote Desktop Services and VPN remote access. I also provide a high level explanation of endpoint detection and endpoint policy enforcement and demonstrate how to provide high availability for the solution. Here is the entire course outline:
Lesson 1 – Introduction and Course Outline
Lesson 2 – Forefront UAG 2010 Overview
Lesson 3 – Planning to Deploy Forefront UAG 2010
Lesson 4 – Installing and Configuring Forefront UAG 2010
Lesson 5 – Configuring a Portal
Lesson 6 – Publishing Exchange Outlook Web App
Lesson 7 – Publishing SharePoint
Lesson 8 – Publishing Remote Desktop Services
Lesson 9 – Configuring VPN Remote Access
Lesson 10 – Enabling Endpoint Detection
Lesson 11 – Configuring High Availability
Lesson 12 – Web Monitor Overview
Lesson 13 – Forefront UAG Backups
Once again I had the opportunity to work with my good friend and fellow Microsoft MVP Jordan Krause on this course. As he did in my previous Trainsignal video training course on Windows Server 2012 DirectAccess, Jordan served as the technical reviewer and provided valuable insight that ultimately made the course better. If you’re planning to implement Forefront UAG 2010 to provide secure remote access to both managed and non-managed systems and devices, be sure to sign up for a subscription at Trainsignal.com today! Not only will you have access to this video training course on Forefront UAG 2010, you will gain access to the entire Trainsignal library of content, including my course on Windows Server 2012 DirectAccess, all for just $49.00 per month!
Forefront TMG 2010 Replacement Options
Since Microsoft formally announced the end of life for the venerable Forefront TMG 2010 firewall, the most common question I hear is “What should I replace my Forefront TMG firewall with?” It’s an excellent question, and one that I can’t really answer for you definitively. Since Microsoft has elected to leave this space entirely, you’ll obviously be replacing it with a solution from another vendor. But which one? Well, the answer is “it depends”. There are many excellent firewalls, web proxies, and secure web gateways on the market today. So-called “Next Generation Firewalls” are gaining in popularity as well, and provide some interesting capabilities a security administrator can leverage to provide increased protection for their corporate networks. Which one to choose depends on many factors, and will vary greatly depending on your deployment scenario. My suggestion when evaluating potential replacements for your Forefront TMG 2010 firewall is to take a look at your current configuration, review your corporate security policy to determine network security requirements, then begin researching products that include the features you need. If you take a look at the latest Gartner Magic Quadrant for Secure Web Gateways or Next Generation Firewalls and choose a product in the leaders or challengers quadrants you will probably be satisfied. Regardless which solution you choose, demand a proof-of-concept or insist on an evaluation period with which you can return the product for a full refund if it doesn’t meet your needs or expectations. Be open-minded during the process, as you’re not likely to have the comfort level with the new solution as you do with your existing Forefront TMG 2010 firewall. If you are using your Forefront TMG 2010 firewall as a dedicated remote access solution, I would encourage you to look closely at Windows Server 2012 remote access VPN and especially DirectAccess.
Keep in mind that although Microsoft has announced the end of life for Forefront TMG 2010, it will still be supported for many years to come. You will have full feature functionality until the end of 2015, and the product will be supported in some fashion until early 2020 so there’s no need to rush. Perhaps the best replacement for Forefront TMG 2010 hasn’t even been created yet! If you have questions about Forefront TMG 2010 replacements, or you are in the process of evaluating another solution to replace your existing Forefront TMG firewall today, feel free to ask questions or share your experiences by commenting below. Thanks!









