Archive
Disable SSL 3.0 and TLS 1.0 on Forefront TMG and UAG 2010
When performing SSL and TLS hardening on Microsoft Forefront Threat Management Gateway (TMG) 2010 or Forefront Unified Access Gateway (UAG) 2010 servers, disabling SSL 3.0 and TLS 1.0 is often required to meet regulatory and compliance guidelines for security. However, disabling SSL 3.0 and TLS 1.0 causes the SQL Server (ISARS) and SQL Server Express services to fail on start up.

Switching from SQL logging to text file logging can be employed as a workaround. However, when using text file logging, generating historical reports in the TMG management console is no longer supported.
To restore full functionality for SQL logging and reporting when SSL 3.0 and TLS 1.0 are both disabled, an update to the local security policy of the server is required. Open the Local Security Policy editor by clicking on the Start button and navigating to Administrative Tools and Local Security Policy. Expand Local Policies and click on Security Options. Double-click on System cryptography: Use FIPS compliant algorithms for encryption, hashing, and signing. Click Enabled and then click OK.

Restart the computer for the changes to take effect. Once complete, all SQL services should start and run without issue.
Note: If Remote Desktop Services (RDS) is used to manage the Forefront TMG firewall it will be necessary to install update KB3080079.
Implementing DirectAccess with Windows Server 2016 Now Available
I am very excited to announce that my new DirectAccess book, “Implementing DirectAccess with Windows Server 2016“ from Apress media, is now shipping! The book is available on popular online sites like Amazon.com, Barnes & Noble, Springer.com, Apress.com, and others. The book is also available in electronic formats such as Amazon Kindle and Barnes & Noble Nook, as well as a variety of subscription formats including Safari, Books24x7, and SpringerLink.
This book contains detailed and prescriptive guidance for the planning, design, implementation, and support of a DirectAccess remote access solution on Windows Server 2016. It also includes valuable insight, tips, tricks, and best practice recommendations gained from my many years of deploying DirectAccess for some of the largest organizations in the world.
Current DirectAccess administrators will also find this book helpful, as the majority of content is still applicable to DirectAccess in Windows Server 2012 and Windows Server 2012 R2. In addition, the book also includes essential information on the design and deployment of highly available and geographically redundant DirectAccess deployments.
Troubleshooting DirectAccess can be a daunting task, so I’ve dedicated an entire chapter in the book to this topic. For those responsible for the maintenance and support of DirectAccess in their organization, this chapter alone will be worth the investment.
Be sure to order your copy today!
Forefront TMG 2010 SQL Services Fail to Start After Disabling SSL 3.0
When performing POODLE attack mitigation on the Forefront TMG 2010 firewall by disabling SSL 3.0, you may encounter a scenario in which TMG’s SQL services fail to start after a reboot.

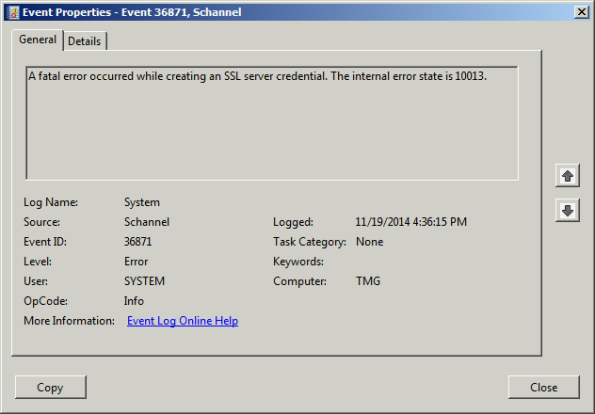
Looking through the Windows system event log you may see an error message logged by the Service Control Manager with event ID 36871 which states:
A fatal error occurred while creating an SSL server credential. The internal error state is 10013.
In addition you may also see an error message logged by the Service Control Manager with event ID 7024 which states:
The SQL Server (ISARS) service terminated with service-specific error %%-2146893007.

This can occur when SSL 3.0 is disabled at the same time that TLS 1.0 is also disabled. Even though TLS 1.1 and 1.2 might be enabled, TMG requires that TLS 1.0 specifically be enabled for SQL server services to function properly when SSL 3.0 is disabled.
To resolve this issue, enable TLS 1.0 Server in the registry by changing the value of Enabled to 1, as shown here. If these registry keys do not exist, create them.

Restart the server for the change to take effect.
Mitigating the POODLE SSL 3 Vulnerability on Forefront TMG 2010
Recently a new and very serious vulnerability in the SSL 3.0 protocol has been discovered that allows an attacker to recover sensitive information for an encrypted session. The Qualys SSL Labs server test has been updated to identify and warn about this issue.
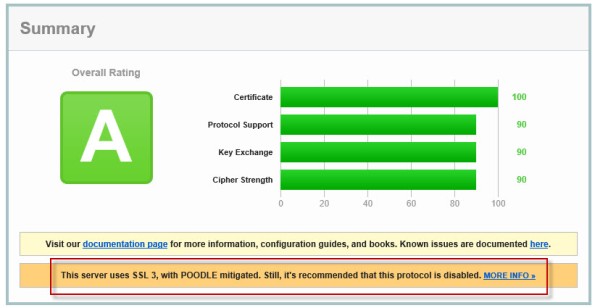
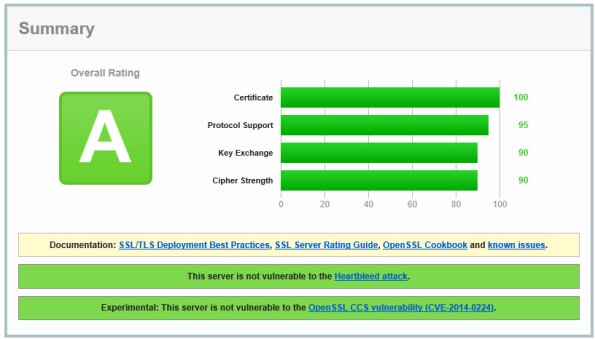
Figure 1 – Qualys SSL Labs Server Test Score for TMG Published Secure Web Site
On a Forefront TMG server with SSL hardening implemented as I’ve outlined here and here, the POODLE attack is mitigated, but it is still recommended that you disable SSL 3.0 altogether. SSL 3.0 is an old, outdated protocol that is no longer widely used, and disabling it should have minimal impact on clients connecting to secure web sites published by the Forefront TMG 2010 firewall.
To disable SSL 3.0 on the TMG firewall, open an elevated PowerShell window and execute the following commands:
New-Item -Path “HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server” -Force
New-ItemProperty -Path “HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server” -PropertyType dword -Value 0 -Name Enabled
Note: Use caution when copying/pasting the above commands as wrapping of the text has occurred.
A restart of the server is required for the change to take effect.
Recommended Forefront TMG 2010 SSL and TLS Configuration
Last year I wrote an article for ISAserver.org that provided detailed guidance for improving security for SSL and TLS protected web sites using Forefront TMG 2010. Many people have reached out to me recently to ask about enabling forward secrecy, which my original article did not include because, at the time, it was not recommended to enable it. However, as times have changed, it is now recommended to enable forward secrecy so I recently wrote a short post with guidance on how to do that. The post was written with a very narrow scope and addressed only the enabling of forward secrecy for TLS. Many of you have since asked for guidance on overall security best practices with regard to SSL and TLS along with adding support for forward secrecy. In addition to the configuration changes detailed in my original ISAserver.org article, I also recommend the following list of SSL and TLS cipher suites be explicitly enforced using the method outlined here.
TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256_P256 TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256_P384 TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256_P521 TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384_P384 TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384_P521 TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256_P256 TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA_P256 TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA_P256 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256_P256 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384_P256 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA_P256 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA_P256 TLS_DHE_DSS_WITH_AES_128_CBC_SHA256 TLS_DHE_DSS_WITH_AES_256_CBC_SHA256 TLS_DHE_DSS_WITH_AES_128_CBC_SHA TLS_DHE_DSS_WITH_AES_256_CBC_SHA TLS_RSA_WITH_AES_128_CBC_SHA256 TLS_RSA_WITH_AES_256_CBC_SHA256 TLS_RSA_WITH_AES_128_CBC_SHA TLS_RSA_WITH_AES_256_CBC_SHA
Using this configuration, the Forefront TMG 2010 firewall should receive an A rating from the SSL Labs test site (at the time of this writing).
Enabling and supporting the above list of cipher suites will provide the best overall protection and performance for your SSL protected web sites. Note that the list above does not include support for SSL 3.0. If you need to support SSL 3.0 you should add the following cipher suites to the end of the list.
TLS_RSA_WITH_RC4_128_SHA TLS_RSA_WITH_RC4_128_MD5
Please note that this configuration may not work with older browsers on old, unsupported operating systems, for example Internet Explorer 6 on Windows XP. Before deploying this configuration in production I would encourage you to conduct some testing with your supported clients to ensure operability.
Enable TLS Forward Secrecy for Forefront TMG 2010 Published Web Sites
Last year I wrote an article for ISAserver.org that outlined in detail how to improve SSL and TLS security for web sites published using Forefront TMG 2010. In its default configuration, Windows Server 2008 R2 and Forefront TMG leave quite a bit to be desired in terms of SSL and TLS security. In the article I demonstrated how to dramatically improve the security posture of TMG when publishing web sites that use SSL and TLS. At the time I wrote the article it was not recommended to enable forward secrecy, so the changes I originally proposed resulted in an “A” score from the Qualys SSL Labs test site. However, times have changed since then, and with the recent revelations of wide spread government spying, it is now recommended to enable forward secrecy by default. Sites that don’t support forward secrecy will now receive a reduced grade.

To accomplish this on the Forefront TMG 2010 firewall, open the Local Group Policy Editor (gpedit.msc) and navigate to Computer Configuration, Administrative Templates, Network, SSL Configuration Settings. Double-click SSL Cipher Suite Order and choose Enabled. Copy the list of SSL cipher suites to a blank notepad document and then move all of the cipher suites that begin with TLS_ECDHE_RSA_WITH_AES_ to the front of the list. Use caution here because the list cannot have any extra commas, line breaks, or spaces at all. Paste the updated list back in to the SSL Cipher Suites box and click Ok.

The server will have to be restarted for the changes to take effect. Once complete, forward secrecy will now be used by modern browsers and you should once again receive an “A” grade from SSL Labs.

Hotfix Rollup 5 for Forefront TMG 2010 SP2 Now Available
Hotfix rollup 5 for Microsoft Forefront TMG 2010 with Service pack 2 (SP2) is now available for download. This latest hotfix rollup includes fixes for the following issues:
KB2963805 – Account lockout alerts are not logged after you install Rollup 4 for Forefront TMG 2010 SP2
KB2963811 – The Forefront TMG 2010 Firewall service (wspsrv.exe) may crash when the DiffServ filter is enabled
KB2963823 – “1413 Invalid Index” after you enable cookie sharing across array members in Forefront TMG 2010
KB2963834 – HTTPS traffic may not be inspected when a user accesses a site through Forefront TMG 2010
KB2967726 – New connections are not accepted on a specific web proxy or web listener in Forefront TMG 2010
KB2965004 – EnableSharedCookie option doesn’t work if the Forefront TMG 2010 service runs under a specific account
KB2932469 – An incorrect value is used for IPsec Main Mode key lifetime in Threat Management Gateway 2010
KB2966284 – A zero value is always returned when an average counter of the “Forefront TMG Web Proxy” object is queried from the .NET Framework
KB2967763 – The “Const SE_VPS_VALUE = 2” setting does not work for users if the UPN is not associated with a real domain
KB2973749 – HTTP Connectivity Verifiers return unexpected failures in TMG 2010
You can download hotfix rollup 5 for Forefront TMG 2010 SP2 here. After applying this update, the new Forefront TMG 2010 build number will be 7.0.9193.644.
Forefront TMG 2010 Computer Certificate Request or Renewal Fails
When attempting to request or renew a computer certificate on the Forefront TMG 2010 firewall, you may receive the following error message:
Status: Failed The RPC server is unavailable.

This occurs because the Forefront TMG 2010 firewall does not, by default, allow the protocols and ports required to request or renew a certificate from a Certificate Authority (CA). Common workarounds suggest stopping the firewall completely or creating a rule allowing all protocols and ports from the TMG firewall to the CA. However, both of these workarounds are problematic. Stopping the firewall is a manual process that will cause a service disruption. It also leaves the firewall in an unprotected state. For edge deployment scenarios, the underlying operating system will be exposed directly to untrusted networks, which is a serious security risk. Creating an open access rule is not desirable because it violates the basic security principle of least privilege by allowing more access than is required.
To properly address this issue and allow for the secure request and renewal of certificates without disruption and with the least exposure, it will be necessary to create an access rule on the Forefront TMG 2010 firewall to allow all dynamic ports (TCP 49152-65535) from the local host network to the IP address of the CA for all users.
Note: Allowing all dynamic ports (TCP 49152-65535) might also be considered too much access from the Forefront TMG 2010 firewall to the CA. It is possible to restrict the dynamic ports used by TMG and further tighten the access rule, if required. For information about restricting dynamic ports, click here.
In addition to the access rule allowing all dynamic ports, it will also be necessary to make a change to a system policy rule. To do this, right-click the Firewall Policy node in the navigation tree and choose All Tasks, System Policy, and then Edit System Policy. In the Authentication Services group highlight Active Directory and clear the checkbox next to Enforce strict RPC compliance.

Once these changes have been made you can now request or renew a computer certificate on the Forefront TMG 2010 firewall successfully.

Windows Azure Multifactor Authentication and Forefront TMG 2010
When Microsoft first announced Windows Azure Multi-Factor Authentication, a cloud-based strong authentication solution, my first thought was “I wonder if it works with Forefront TMG 2010?” Being cloud-based, my first thought was perhaps not. However, once I started digging in to it I quickly learned that it includes a software component that can be installed on-premises and will even integrate with on-premises security solutions via a number of interfaces, including RADIUS. Forefront TMG 2010 has supported RADIUS authentication for many years, so I put together a test lab and in no time at all I had Windows Azure multi-factor authentication working with Forefront TMG 2010 remote access VPN. Forefront TMG 2010 integrated with Windows Azure multi-factor authentication provides the highest level of protection for remote access users. Leveraging Windows Azure cloud-based strong authentication is extremely cost effective, with very low per user or per authentication costs and no on-premises hardware to purchase. The Windows Azure public cloud, which is ISO/IEC27001:2005 certified, provides the most secure and reliable strong authentication service available today. To learn how to configure Forefront TMG 2010 to work with Windows Azure multi-factor authentication, click here.
Improving SSL Security for Forefront TMG 2010 Published Web Sites
Recently I wrote an article for ISAserver.org entitled Improving SSL Security for Forefront TMG 2010 Published Web Sites. In the article I demonstrate how to evaluate the current security configuration of your Forefront TMG firewall for published SSL web sites and how to make changes to the default settings in order to improve the overall security posture of TMG in reverse proxy scenarios. Implementing these changes will provide dramatically improved protection for Forefront TMG published SSL web sites. The steps outlined in the article include details for changes to be made to specific registry entries on the Forefront TMG 2010 firewall. I’ve had a number of requests to make the registry file available for download in order to simplify the process and ensure that these changes are made correctly. You can download the registry file used in the ISAserver.org post here. Enjoy!