Archive
Disable SSL 3.0 and TLS 1.0 on Forefront TMG and UAG 2010
When performing SSL and TLS hardening on Microsoft Forefront Threat Management Gateway (TMG) 2010 or Forefront Unified Access Gateway (UAG) 2010 servers, disabling SSL 3.0 and TLS 1.0 is often required to meet regulatory and compliance guidelines for security. However, disabling SSL 3.0 and TLS 1.0 causes the SQL Server (ISARS) and SQL Server Express services to fail on start up.

Switching from SQL logging to text file logging can be employed as a workaround. However, when using text file logging, generating historical reports in the TMG management console is no longer supported.
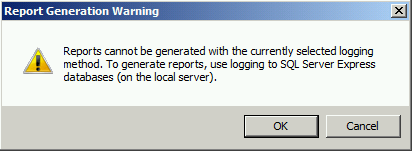
To restore full functionality for SQL logging and reporting when SSL 3.0 and TLS 1.0 are both disabled, an update to the local security policy of the server is required. Open the Local Security Policy editor by clicking on the Start button and navigating to Administrative Tools and Local Security Policy. Expand Local Policies and click on Security Options. Double-click on System cryptography: Use FIPS compliant algorithms for encryption, hashing, and signing. Click Enabled and then click OK.

Restart the computer for the changes to take effect. Once complete, all SQL services should start and run without issue.
Note: If Remote Desktop Services (RDS) is used to manage the Forefront TMG firewall it will be necessary to install update KB3080079.
Using PowerShell to Determine Forefront TMG Build Number
 Identifying the current build number of your Forefront TMG 2010 installation is critically important when making changes or updates to the system. It is generally recommended that all TMG firewalls be on the same release, so having this information is essential. Many TMG administrators use the TMG management console to gather this information, but I can tell you based on experience that this is not always the most accurate method to use.
Identifying the current build number of your Forefront TMG 2010 installation is critically important when making changes or updates to the system. It is generally recommended that all TMG firewalls be on the same release, so having this information is essential. Many TMG administrators use the TMG management console to gather this information, but I can tell you based on experience that this is not always the most accurate method to use.
I much prefer to gather this information programmatically at the command line. In the past I’ve written about using VBScript to do this, but it’s almost 2016 now and we really should be using PowerShell whenever possible. To that end, here are a few lines of PowerShell code you can use to accurately determine which version and build number your TMG firewall is currently running.
$FPC = New-Object -ComObject FPC.Root $Server = $FPC.GetContainingServer() $Server.ProductVersion

If you’ve done any work at all with VBScript and the TMG’s FPC COM object, you’ll no doubt be able to convert some of your existing scripts to PowerShell. Also, PowerShell, with its tab auto completion, is much more discoverable than using VBScript with COM, so I’m sure you’ll be able to do a lot more with TMG using PowerShell.
Enjoy!
Hotfix Rollup 3 for Forefront TMG 2010 SP2 Now Available
Hotfix rollup 3 for Microsoft Forefront TMG 2010 with Service Pack 2 is now available for download. This latest hotfix rollup includes fixes for the following issues:
KB2700248 – A server that is running Forefront TMG 2010 may stop accepting all new connections and may become unresponsive
KB2761736 – All servers in a load balanced web farm may become unavailable in Forefront TMG 2010
KB2761895 – The Firewall service (wspsrv.exe) may crash when the firewall policy rules are reevaluated in Forefront TMG 2010
KB2780562 – PPTP connections through Forefront TMG 2010 may be unsuccessful when internal clients try to access a VPN server on the external network
KB2780594 – A non-web-proxy client in a Forefront TMG 2010 environment cannot open certain load-balanced websites when TMG HTTPS inspection is enabled
KB2783332 – You cannot log on when FQDN is used and authentication delegation is set to “Kerberos constrained delegation” in a Forefront TMG 2010 environment
KB2783339 – A closed connection to a domain controller is never reestablished when authentication delegation is set to “Kerberos constrained delegation” in a Forefront TMG 2010 environment
KB2783345 – Unexpected authentication prompts while you use an OWA website that is published by using Forefront TMG 2010 when RSA authentication and FBA are used
KB2785800 – A “DRIVER_IRQL_NOT_LESS_OR_EQUAL stop error may occur on a server that is running Forefront TMG 2010
KB2790765 – A “Host Not Found (11001)” error message occurs when an SSL site is accessed by using a downstream Forefront TMG 2010 server that has HTTPS Inspection enabled
You can download hotfix rollup 3 for Forefront TMG 2010 SP2 here. After applying this update, the new Forefront TMG 2010 build number will be 7.0.9193.575.
Forefront TMG 2010 End of Life Statement
Note: This post updated on 4/22/2015 to reflect current information about the status of the Microsoft Reputation Service (MRS) after December 1, 2015.
Today, Microsoft announced the Forefront TMG 2010 product will be discontinued. Microsoft will continue to provide mainstream support for TMG until April 14, 2015, and extended support until April 14, 2020. The Forefront TMG 2010 Web Protection Services (WPS) will be discontinued on December 31, 2015. Beginning on January 1, 2016, Web Protection Service (URL filtering) will cease to function and the Microsoft Reputation Service (MRS) will be shutdown permanently. Virus and malicious software scanning and the Network Inspection System (NIS) will continue to operate but will no longer receive updates.
The end of life for Forefront TMG 2010 comes as part of sweeping changes made to the entire Forefront protection suite of products. In addition to ending development of Forefront TMG 2010, Microsoft also announced that Forefront Protection for Exchange (FPE), Forefront Protection for SharePoint (FPSP), Forefront Security for OCS (FSOCS), and Forefront Protection Server Management Console (FPSMC) are all being discontinued. Forefront Online Protection for Exchange (FOPE), which has been a part of Office 365, is being renamed Exchange Online Protection.
Looking ahead, Forefront Unified Access Gateway (UAG) 2010 and Forefront Identify Manager (FIM) 2010 R2 both have current roadmaps and will continue to be developed, although it is likely that they will not continue under the Forefront brand name.
Forefront TMG 2010 Update Center Quick Tip
The Update Center in the Forefront TMG 2010 management console provides an instant view of the status of signature updates for the Malware Inspection and Network Inspection System (NIS) protection mechanisms. However, the column layout leaves out important information that can be essential when troubleshooting signature update issues. By default, the Last Checked and Last Success columns are hidden from view. To display these details, right-click anywhere in the column headings and then select Add/Remove Columns.
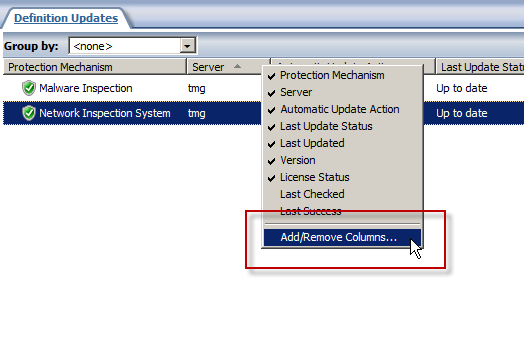
Next, select the Last Checked and Last Success columns and click Add.

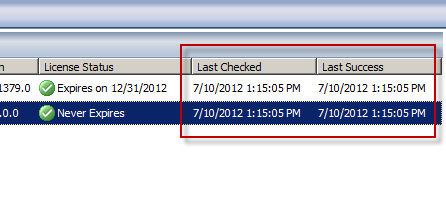
Now you’ll see when the Forefront TMG 2010 firewall last checked for updates and when it was last successful.
TechDays San Francisco 2012
TechDays San Francisco 2012, sponsored by the Pacific IT Professionals user group, is a two day IT professional conference being held on March 23 and 24, 2012. The event features a lineup of speakers that includes Chris Avis, CA Callahan, Jennelle Crothers, Jessica DeVita, Steve Evans, Jason C. Helmick, Chris Henley, Ed Horley, Darren Mar-Elia, Mark Minasi, Stephen Rose, Joey Snow, Doug Spindler, Mark Vinkour, Harold Wong, and Chris Zwergel. Sessions will cover topics such as Azure and cloud, Clustering, DNS/DHCP/IPAM, Exchange, Hyper-V, IIS, Lync, MDOP, networking and VPN, Powershell, SharePoint, System Center, VDI, Windows 8 Client and Server, and Windows Phone 7. I will be presenting sessions on Forefront Edge Security (Forefront TMG 2010 and UAG 2010) as well as DirectAccess. Visit the TechDaysSF web site for the full speaker lineup and session abstracts, then click here to register for the event. Hope to see you there!
ESET Gateway Security Beta for Forefront TMG 2010
For security administrators looking to improve upon Forefront TMG 2010’s already strong advanced web protection features, leading anti-virus vendor ESET recently announced the beta availability of its Gateway Security for Forefront TMG 2010 software. ESET Gateway Security for Forefront TMG delivers advanced, gateway-integrated virus and malicious software scanning to provide comprehensive protection for web-based protocols like HTTP and FTP. ESET Gateway Security for Forefront TMG also supports SMTP, IMAP, and POP3 protocols to provide anti-malware and anti-spam capabilities for added protection. In addition, ESET Gateway Security for Forefront TMG 2010 includes host-based security for the TMG firewall’s underlying operating system, as well as automatic file exclusion configuration to ensure compatibility with Forefront TMG. ESET Gateway Security for Forefront TMG 2010 is fully compatible with existing ESET centralized management tools and supports Microsoft ISA Server 2006. Download the beta today!
Error 0xc0040431 When Creating a Forefront TMG 2010 Enterprise Array
When attempting to join a Forefront TMG 2010 enterprise edition firewall to an Enterprise Management Server (EMS) managed array, you may encounter one of the following error messages:
The operation failed. Error: 0xc0040431 Forefront TMG Services failed to start after array join or an array disjoin. Check alerts, fix the configuration, and attempt to restart the services.

The operation failed. Error: 0xc0040410 The file cannot be imported because the enterprise management mode is 2010SP1 in the exported file and 2008-only in the stored configuration.

You may also encounter one of the following error messages when attempting to create a standalone array with two or more Forefront TMG 2010 enterprise edition firewalls:
The operation failed. Error: 0x80004002 No such interface supported

The operation failed. Error: 0xc0040410 The file cannot be imported because the enterprise management mode is in the exported file and in the stored configuration.

Any of these errors can occur when you attempt to join a pre-SP2 Forefront TMG 2010 firewall to an EMS-managed array running Forefront TMG SP2, or when you attempt to create a standalone array with one node running Forefront TMG SP2 and another node running SP1.
To resolve this issue, make certain that Forefront TMG 2010 firewalls are all at the same service pack and update level before joining an EMS-managed array or creating a standalone array. For information about determining which version of ISA or TMG is installed, refer to one of the following blog posts:
https://tmgblog.richardhicks.com/2010/10/11/how-to-determine-tmg-version/
https://tmgblog.richardhicks.com/2010/12/03/more-about-determining-tmg-version-numbers/
For a documented reference of ISA and TMG build numbers, click here.
Configuring Forefront TMG 2010 HTTPS Inspection Inclusion List
When HTTPS inspection is configured and enabled on a Forefront TMG 2010 firewall, the administrator has the option to define web sites to exclude from HTTPS inspection. This may be required for a variety of reasons. For example, an administrator may need to exclude certain destinations to address privacy concerns, or perhaps HTTPS inspection breaks an application that uses SSL to tunnel non-HTTP protocols. All HTTPS web sites are inspected except for those sites defined as Destination Exceptions.

Beginning with Service Pack 2 (SP2) for Forefront TMG 2010, administrators can now define an explicit inclusion list for HTTPS inspection. Sites included on this list will be subject to HTTPS inspection, while all other destinations will be excluded. To define an HTTPS inspection inclusion list, create a Domain Name Set and populate it with those destinations for which you explicitly want to enforce HTTPS inspection.
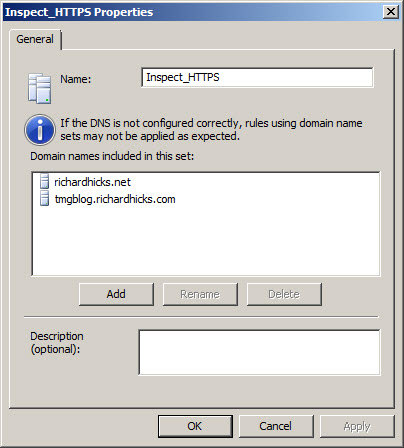
After saving and applying the configuration, copy this VBScript file to the TMG firewall, then open an elevated command prompt and type the following command:
cscript.exe ConfigureHTTPSiInclusionList.vbs <DomainNameSetName>
Substitute <DomainNameSetName> in the command above with the name of the Domain Name Set created earlier. Once configured, the Destination Exceptions tab of the HTTPS Outbound Inspection properties will be greyed out, and only those sites included in the Domain Name Set defined as the HTTPS inspection inclusion list will be subject to HTTPS inspection. All other destinations will be excluded. You can still define Source Exceptions as needed, however.

Only one Domain Name Set can be specified as the HTTPS inspection inclusion list. Running the command without parameters removes any configured inclusion list and returns HTTPS inspection back to its original state.
For more information regarding HTTPS inspection inclusion lists, refer to KB2619986.







