Archive
Installing Forefront TMG 2010 SP2 on Enterprise Arrays
July 4,2012 – Update: A script is now available on ISATools.org that will identify the exact order in which to install TMG SP2 for your environment. You can download the script here.
To successfully install Service Pack 2 (SP2) for Forefront TMG 2010, you must first install Service Pack 1 (SP1), then Software Update 1 for SP1 (SP1U1) as I indicated in a previous blog post. None of the other hotfix rollups available for Forefront TMG are required to upgrade to SP2. For Forefront TMG 2010 enterprise arrays, these updates must be installed in a specific order to eliminate potential conflicts. The proper sequence is as follows:
First, install SP1 for Forefront TMG 2010 on the…
- Enterprise Management Server (EMS)
- Reporting server in each array
- Remaining array members in each array
Next, install Software Update 1 for Forefront TMG 2010 SP1 on the…
- EMS
- Reporting server in each array
- Remaining array members in each array
Lastly, install SP2 for Forefront TMG 2010 on the…
- EMS
- Reporting server in each array
- Remaining array members in each array
For standalone arrays, treat the array manager as the EMS and follow the order outlined above. In addition, if you are adding a new array member to an existing array, install Forefront TMG 2010 and apply the updates in order before joining the array. Make certain that the new array member is at the same update level as the EMS and other array members. Also, consider slipstreaming SP2 with your installation media to save yourself some time.
Special thanks to Jim Harrison for clarification on the installation order.
Forefront TMG 2010 Turns Two Years Old
Today marks the second anniversary of the release to manufacturing (RTM) for Microsoft Forefront Threat Management Gateway (TMG) 2010. In the two years since its release Microsoft has provided two major service packs that have increased stability, improved performance and scalability, and also added some helpful new functionality. During this time the product also achieved Common Criteria (level EAL4+) certification. As we approach the end of mainstream support for Microsoft ISA Server 2006 SP1, now is a good time to begin evaluating Forefront TMG 2010 and to start planning your migration!
Configuring Forefront TMG 2010 HTTPS Inspection Inclusion List
When HTTPS inspection is configured and enabled on a Forefront TMG 2010 firewall, the administrator has the option to define web sites to exclude from HTTPS inspection. This may be required for a variety of reasons. For example, an administrator may need to exclude certain destinations to address privacy concerns, or perhaps HTTPS inspection breaks an application that uses SSL to tunnel non-HTTP protocols. All HTTPS web sites are inspected except for those sites defined as Destination Exceptions.

Beginning with Service Pack 2 (SP2) for Forefront TMG 2010, administrators can now define an explicit inclusion list for HTTPS inspection. Sites included on this list will be subject to HTTPS inspection, while all other destinations will be excluded. To define an HTTPS inspection inclusion list, create a Domain Name Set and populate it with those destinations for which you explicitly want to enforce HTTPS inspection.
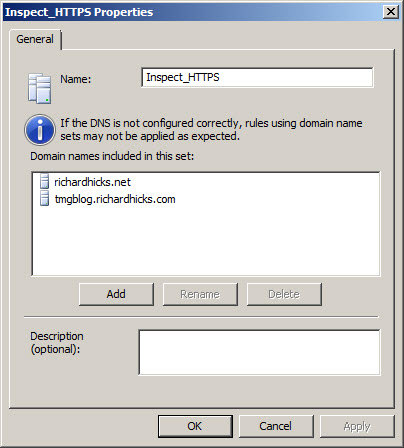
After saving and applying the configuration, copy this VBScript file to the TMG firewall, then open an elevated command prompt and type the following command:
cscript.exe ConfigureHTTPSiInclusionList.vbs <DomainNameSetName>
Substitute <DomainNameSetName> in the command above with the name of the Domain Name Set created earlier. Once configured, the Destination Exceptions tab of the HTTPS Outbound Inspection properties will be greyed out, and only those sites included in the Domain Name Set defined as the HTTPS inspection inclusion list will be subject to HTTPS inspection. All other destinations will be excluded. You can still define Source Exceptions as needed, however.

Only one Domain Name Set can be specified as the HTTPS inspection inclusion list. Running the command without parameters removes any configured inclusion list and returns HTTPS inspection back to its original state.
For more information regarding HTTPS inspection inclusion lists, refer to KB2619986.





