Forefront TMG 2010 Protocol Direction Explained
When reviewing the configuration of a pre-defined protocol or creating a custom protocol on the Forefront TMG 2010 firewall, many new (and sometimes even veteran) firewall administrators can be confused by the protocol direction. The correct configuration of the protocol direction is essential for proper firewall operation, but there are times when it can be somewhat unintuitive. In this post I’ll provide some clarification.
TCP
For TCP protocols the direction can be specified as either inbound or outbound.
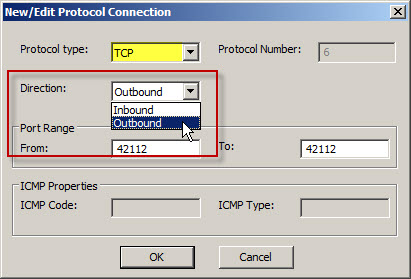
For access rules, protocol direction is configured as outbound. Traffic flows outbound from the source to the destination. This is true even when creating an access rule to allow traffic inbound to the Forefront TMG 2010 firewall itself. It sounds counterintuitive, but the TCP protocol direction for access rules allowing access to the Local Host network should still be outbound. Why? Again, because traffic flows outbound form the source to the destination, in this case the TMG firewall’s Local Host network. If, in this case, you were to configure the protocol direction as Inbound (intuitively, inbound to the TMG firewall) it will not work.
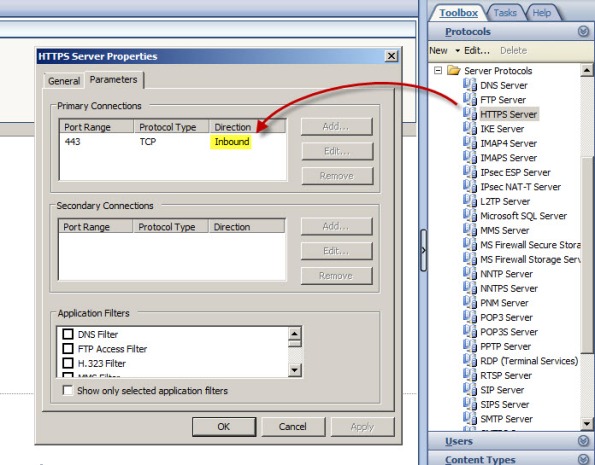
For publishing rules, protocol direction is configured as inbound. Traffic flows inbound from the source to the published service on the Forefront TMG 2010 firewall. Pre-defined server publishing protocols include the “server” suffix, as shown here:
UDP
For UDP protocols the direction can be specified as either Receive, Receive Send, Send, or Send Receive.
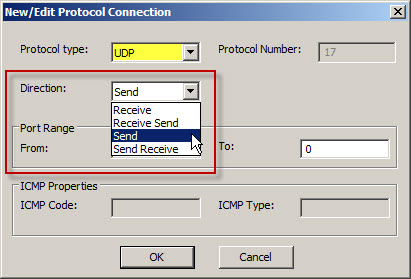
For access rules, protocol direction is configured as Send. Traffic is sent from the source to the destination. If a response is expected then the protocol direction is configured as Send Receive. This is required because UDP is connectionless and the return traffic would otherwise be denied by the TMG firewall.
For publishing rules, protocol direction is configured as Receive. Traffic is received by the TMG firewall from the source to the published service on the Forefront TMG 2010 firewall. If a response is expected then the protocol direction would be configured as Receive Send.
IP and ICMP
For IP and ICMP protocols the direction can be specified as either Send or Send Receive.

IP and ICMP protocol definitions are only supported for access rules, so protocol direction is configured as Send. As with UDP, IP and ICMP are connectionless and if a response is expected then the protocol direction is configured as Send Receive.





Great post Rich. The explanation on the options for UDP based protocols was especially helpful..
I also wanted to add how well one of your recommendations related to this topic has worked out. For defining custom protocol names, you had suggested including the port number, and optionally the direction of traffic in the name itself. This has saved me several times in quickly provisioning rules based on custom protocols.
– Pete
I’m trying to enable UDP through my TMG 2010 box to support RemoteFX from Server 2012. Microsoft says to set the UDP direction to send recieve which required me to create an access rule. I don’t seem to be have any luck with this are there any guides on how to do this?
I’m not aware of any guides that provide detailed information for publishing RemoteFX in Windows Server 2012 through the Forefront TMG 2010 firewall. However, it is possible that there are additional protocols that are required. Have you checked the access logs when you’re trying to connect to see if anything else is dropping? Another suggestion is to observe the traffic when there is no firewall in between to see what protocols/ports are in use, and then create access rules to allow the traffic as required.