Mitigating the POODLE SSL 3 Vulnerability on Forefront TMG 2010
Recently a new and very serious vulnerability in the SSL 3.0 protocol has been discovered that allows an attacker to recover sensitive information for an encrypted session. The Qualys SSL Labs server test has been updated to identify and warn about this issue.
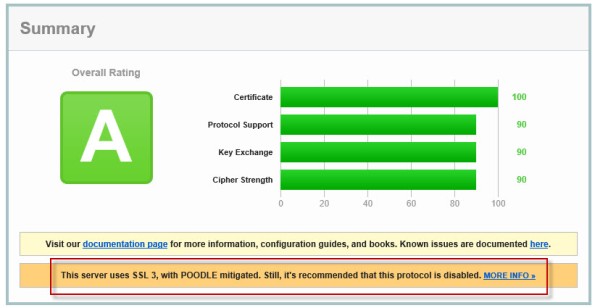
Figure 1 – Qualys SSL Labs Server Test Score for TMG Published Secure Web Site
On a Forefront TMG server with SSL hardening implemented as I’ve outlined here and here, the POODLE attack is mitigated, but it is still recommended that you disable SSL 3.0 altogether. SSL 3.0 is an old, outdated protocol that is no longer widely used, and disabling it should have minimal impact on clients connecting to secure web sites published by the Forefront TMG 2010 firewall.
To disable SSL 3.0 on the TMG firewall, open an elevated PowerShell window and execute the following commands:
New-Item -Path “HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server” -Force
New-ItemProperty -Path “HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server” -PropertyType dword -Value 0 -Name Enabled
Note: Use caution when copying/pasting the above commands as wrapping of the text has occurred.
A restart of the server is required for the change to take effect.





Excellent article Richard 🙂
However I believe whole server has to be restarted than JUST TMG Services.
Good Article Richard 🙂
Also as its a Windows level change I believe whole machine has to be restarted than JUST TMG Services.
Absolutely. That’s what I meant, but I can see how my original wording made it seem like I was suggesting that only the TMG firewall “service” needed to be restarted. Yes, the server itself needs to be completely restarted for this change to take effect. I’ve updated the wording in the post for clarification. Thanks for bringing that to my attention!
Any thoughts on getting to 100 on all fields? Currently I’m at 100,100,90,90. TMG has all but TLS1.2 enabled, I seem to be losing out to cipher strength (128’s rather than 256, ECDH is pushing at <4096 effective), and downgrade attack prevention.
I don’t have any. I’m satisfied with an “A”. 🙂 If you do get a perfect score, please let us know how you did it!
this is an interesting article 🙂
https://scotthelme.co.uk/getting-an-a-on-the-qualys-ssl-test-windows-edition/
Most interesting! 🙂
Error with second command: A parameter cannot be found that matches parameter name ‘PropertyType’. I was able to set it in regedit once the SSL 3.0 Protocol was named, however.
My PowerShell code may not be perfect. 😉 It certainly doesn’t contain any error checking, and also doesn’t behave well if those keys already exist. Glad you got it figured out though. 🙂
I’m certainly not complaining: you got me on the right track and I appreciate it. Setting the Enable to false inside regedit worked fine after the first step. Thanks for your post!
Hi Richard, I’ve used the IIS Crypto tool to implement the necessary registry changes to secure my instance of TMG. My latest Qualsys scan states the following;
This server is vulnerable to the POODLE attack against TLS servers. Patching required. Grade set to F. MORE INFO »
But according to the following article that states that schannel isn’t affected by CVE-2014-8730, I’m confused :S
https://social.technet.microsoft.com/Forums/windowsserver/en-US/0f854cf2-9028-4788-bf0f-655f0115cc7d/schannel-and-tls-1x-padding-vulnerability-cve20148730?forum=winserversecurity
It might be a false positive. Did you also disable support for RC4 cipher suites?
Have you noticed any difference between the registry setting of Enabled=0 or the registry setting DisabledByDefault=1? Do both work equally the same?
I have not. I would expect they would exhibit the same behavior, but I could be wrong. Testing should confirm that.
I post my question here, because I dont where else to post it.
Even after disabling SSL v2 + v3, enabling TLS 1.1 + 1.2 AND using your recommended list of SSL and TLS cipher suites I get a rating F on the site. The reason is a Poodle attack against TLS:
“This server is vulnerable to the POODLE attack against TLS servers. Patching required. Grade set to F.”
Im not sure what I can do to change that… Do you have any advises?
In addition to the steps in this post, you will still need to follow the guidance I’ve outlined here: http://www.isaserver.org/articles-tutorials/configuration-security/improving-ssl-security-forefront-threat-management-gateway-tmg-2010-published-web-sites.html.
And here: https://tmgblog.richardhicks.com/2014/09/08/recommended-forefront-tmg-2010-ssl-and-tls-configuration/
That should fix it!