Forefront TMG 2010 Configuration Error Alert
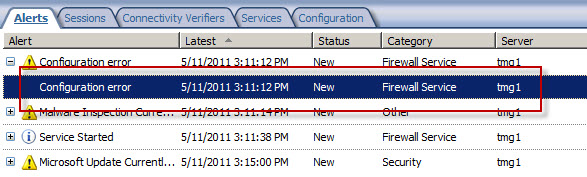
On a Forefront Threat Management Gateway (TMG) 2010 firewall you may encounter a Configuration Error alert like this:
The alert description states:
“The routing table for the network adapter Internal includes IP address ranges that are not defined in the array-level network Internal, to which it is bound. As a result, packets arriving at this network adapter from the IP address ranges listed below or sent to these IP address ranges via this network adapter will be dropped as spoofed. To resolve this issue, add the missing IP address ranges to the array network.
The following IP address ranges will be dropped as spoofed:
External:172.16.2.0-172.16.3.255;
This alert is the result of the Forefront TMG firewall’s routing table and network definition being out of sync with each other. In this example, the routing table looks like this:
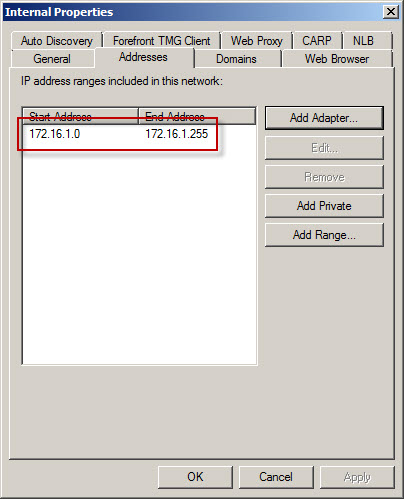
However, the Forefront TMG Internal network definition looks like this:
As you can see, the Forefront TMG firewall is configured with an Internal network IP address range of 172.16.1.0/24. However, the routing table contains additional static routes that also make the 172.16.2.0/24 and 172.16.3.0/24 networks reachable.
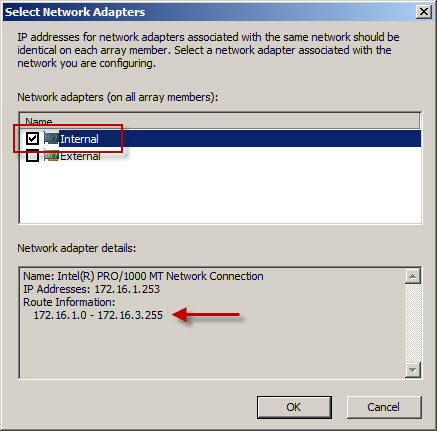
To resolve this issue, highlight the Networking node in the navigation tree, select the Networks tab in the center window, then highlight the network that corresponds to the IP address range contained in the alert. In our example the address range 172.16.2.0-172.16.3.255 also belongs to the Internal network. Right-click the Internal network and choose properties, choose the Addresses tab, then remove all address ranges previously configured. Next, choose Add Adapter and choose the network adapter for this network.
Using this method the IP address range for this network is built using the routing table for the network interface. This is the preferred method for defining IP address ranges for Forefront TMG networks. Save the changes and apply the configuration.
For more information on configuring network interfaces for Forefront TMG 2010 firewalls, please refer to Jason Jones’ excellent documentation on the subject here:
Recommended Network Adapter Configuration for Forefront TMG Standard Edition Servers
Recommended Network Adapter Configuration for Forefront TMG Enterprise Edition Servers







Thanks Rich, I now have updated TMG versions on the TechNet wiki here:
http://social.technet.microsoft.com/wiki/contents/articles/recommended-network-adapter-configuration-for-forefront-tmg-standard-edition-servers.aspx
http://social.technet.microsoft.com/wiki/contents/articles/recommended-network-adapter-configuration-for-forefront-tmg-enterprise-edition-servers.aspx
Cheers
JJ
Thanks, Jason! I’ll update the post to reflect this information. 🙂
Hi Andreas,
I disagree. Once you have configured your network interfaces with any required static routes, selecting “add adapter” is foolproof. Also, the DHCP VPN subnet should not be a part of the Internal network, so that shouldn’t cause any issues. I have never encountered a scenario in which this technique resulted in unexpected behavior.
Thanks!
I faced the same problem. I reinstalled the forefront because of this and then when I was selecting network adaptor it was picking the incorrect route information of that adaptor from no where..therefore I went to command prompt and typed the command ” route -f ” and it is gone…anyway above method is also nice way to solve the issue..
Not surprising. Confuring static routes at the command line then selecting “add adapter” is the best and most reliable way to define network definitions on the Forefront TMG 2010 firewall. 🙂
The method proposed above is quite elegant, but does not seem to work in an Enterprise Edition installation. You have to configure all network ranges both at the enterprise and array level (unless you include the enterprise network in the array network), and for enterprise networks the “Add Adapter …” operation is not supported. Correct?
That’s correct. Enterprise networks don’t have any concept of a network adapter because, for obvious reasons, addressing and routing tables for physical network adapters is going to be different for each array in the enterprise.
For an array of servers joined to an EMS – how would you remove an errant route on a single server? New member joined with a bad route – on joining the array that route is now reflected under address range for the network. I would think route delete on the server then edit the range from the UI.
Or would it be ok to delete the route, ensure all 3 nodes match route table wise then perform the add adapter? Adding adapter at this point should reflect the aggregate of the 3?
That’s probably best. The routes for all array members must be identical. Ensure that they are all in order (and matching) and then update the network definition by removing all addresses and clicking “add adapter” again.
I’m getting a bizarre result when using “Add adapter”. It wants to add the DMZ IP’s and most of the external IP’s. My route print looks more or less correct.
Basically, TMG seems to think that “internal” consists of all IP’s that are not actually explicitly assigned to “external” IP’s. However, my ‘route print’ looks normal.
I’ve been getting this error for a while, and at it’s worst, it disables my VPN!
At one time, we had a DMZ with a Cisco router setup by a 3rd party to do S2S VPN off the DMZ, which was particularly confusing to TMG (I believe) because the route had to be setup to go to the DMZ IP for a separate internal IP range as well. I disabled this, and rebooted, and VPN’s now work, but the fix posted here still results in most WAN IP’s being added to the internal NIC, which is clearly wrong.
Any ideas?
== John ==
So your TMG server has multiple network interfaces then, correct?