Archive
Mitigating the POODLE SSL 3 Vulnerability on Forefront TMG 2010
Recently a new and very serious vulnerability in the SSL 3.0 protocol has been discovered that allows an attacker to recover sensitive information for an encrypted session. The Qualys SSL Labs server test has been updated to identify and warn about this issue.
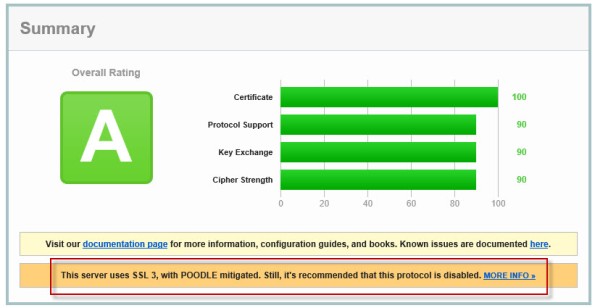
Figure 1 – Qualys SSL Labs Server Test Score for TMG Published Secure Web Site
On a Forefront TMG server with SSL hardening implemented as I’ve outlined here and here, the POODLE attack is mitigated, but it is still recommended that you disable SSL 3.0 altogether. SSL 3.0 is an old, outdated protocol that is no longer widely used, and disabling it should have minimal impact on clients connecting to secure web sites published by the Forefront TMG 2010 firewall.
To disable SSL 3.0 on the TMG firewall, open an elevated PowerShell window and execute the following commands:
New-Item -Path “HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server” -Force
New-ItemProperty -Path “HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server” -PropertyType dword -Value 0 -Name Enabled
Note: Use caution when copying/pasting the above commands as wrapping of the text has occurred.
A restart of the server is required for the change to take effect.




