Archive
Forefront TMG 2010 Network Inspection System NIS Signature Updates
When Microsoft announced the formal end-of-life for Forefront TMG 2010, they laid out in clear detail the support boundaries for the product going forward. Microsoft stated specifically that they would continue mainstream support for TMG until April of 2015, and extended support would terminate in April 2020. However, the Web Protection Service (WPS) updates for the URL filtering database, antimalware signatures, and the Network Inspection System (NIS) would only continue until December 31, 2015.
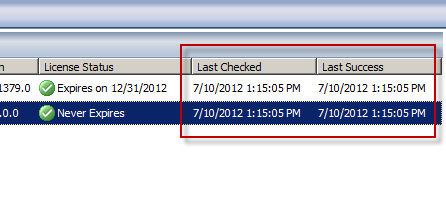
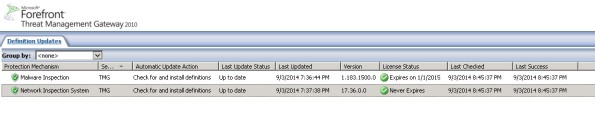
Unfortunately, it appears that Microsoft has abandoned the updating for NIS signatures. You may have noticed that a fully updated Forefront TMG firewall with the latest signature updates shows that the last NIS signature was released for security bulletin MS12-050 on July 20, 2012!
I find it difficult to believe that there hasn’t been a single vulnerability discovered or hotfix released since July of 2012 that wouldn’t benefit from NIS protection, so I have to assume that Microsoft is no longer supporting NIS in spite of their pledge to provide support for WPS through the end of 2015. If you are relying on NIS for essential network protection, it’s time to consider deploying a dedicated IDS/IPS solution or another solution that provides this functionality.
Citrix NetScaler Forefront TMG 2010 Replacement White Paper
With the formal end of life announcement for Forefront TMG 2010 last year, many firewall and secure web gateway vendors have been touting themselves as replacements for TMG. The folks at Citrix recently made available a white paper [PDF] making their case as a comprehensive replacement for Forefront TMG. While I don’t have any personal experience with the NetScaler solution, it does appear to have many of the features that TMG administrators have come to rely upon, such as URL filtering, virus and malicious software inspection, SSL termination (HTTPS inspection), content caching, low-level intrusion detection and prevention, and VPN capabilities. In addition, the NetScaler supports flexible network placement with edge, back firewall, and unihomed (single-legged or one-arm) deployment options. The solution is available in both hardware appliance form factor and virtual appliance.
Citrix makes an attempt to position their solution as the ideal and comprehensive replacement for Forefront TMG, and while it does have many features that TMG provides there is one glaring omission – an alternative to the Forefront TMG Firewall Client. ISA and TMG administrators have long used the Firewall Client to provide seamless and transparent proxy services for Winsock applications. The firewall client enables fully authenticated proxy support for non-web based protocols, and it appears that the NetScaler does not include such capabilities.
As with most white papers comparing solutions like this, it is helpful to understand they are essentially marketing material designed to downplay the features of the competing solution while often embellishing their own features. There are also some inaccuracies with regard to Forefront TMG capabilities, which is also not uncommon in documents such as these. For example, the document states that Forefront TMG 2010 failover requires three nodes, which is incorrect. You can easily create a standalone array using Forefront TMG 2010 Enterprise Edition using two nodes.
Overall the Citrix NetScaler looks like a pretty good solution. If you are in the market today for an alternative to Forefront TMG 2010 (…and should you be? That’s a topic for a future post, so stay tuned!) then download their white paper and take a closer look.
Forefront TMG 2010 Update Center Quick Tip
The Update Center in the Forefront TMG 2010 management console provides an instant view of the status of signature updates for the Malware Inspection and Network Inspection System (NIS) protection mechanisms. However, the column layout leaves out important information that can be essential when troubleshooting signature update issues. By default, the Last Checked and Last Success columns are hidden from view. To display these details, right-click anywhere in the column headings and then select Add/Remove Columns.
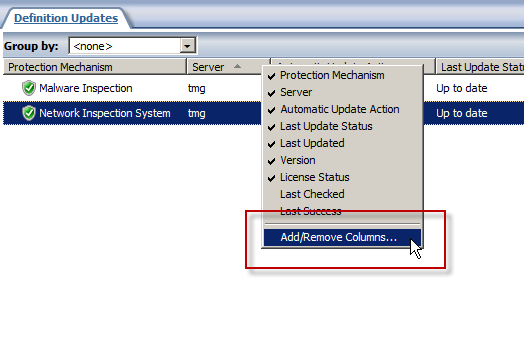
Next, select the Last Checked and Last Success columns and click Add.

Now you’ll see when the Forefront TMG 2010 firewall last checked for updates and when it was last successful.