Archive
Reminder: Microsoft Reputation Services (MRS) End of Support
 As a reminder to anyone out there still using the URL filtering feature of their Forefront TMG 2010 firewall, the Microsoft Reputation Services (MRS) service, which provides URL categorization for TMG, will no longer be supported after December 31, 2015. After this date, Microsoft will cease updating their URL categorization database. In addition, there are no guarantees from Microsoft that the service will be available in any form, so customers still using this service are strongly encouraged to look for alternative solutions.
As a reminder to anyone out there still using the URL filtering feature of their Forefront TMG 2010 firewall, the Microsoft Reputation Services (MRS) service, which provides URL categorization for TMG, will no longer be supported after December 31, 2015. After this date, Microsoft will cease updating their URL categorization database. In addition, there are no guarantees from Microsoft that the service will be available in any form, so customers still using this service are strongly encouraged to look for alternative solutions.
For many organizations, this means migrating to another platform entirely, which is not a bad idea considering that TMG is nearly six years old now. Alternatively, it is possible to replace TMG’s web filtering component. This can be done on premises by using integrations from various third-party vendors, or by using a cloud-based solution such as Zscaler.
Regardless which path you take, you have just over one month to identify and implement another URL filtering solution. Good luck!
Forefront TMG 2010 SQL Services Fail to Start After Disabling SSL 3.0
When performing POODLE attack mitigation on the Forefront TMG 2010 firewall by disabling SSL 3.0, you may encounter a scenario in which TMG’s SQL services fail to start after a reboot.

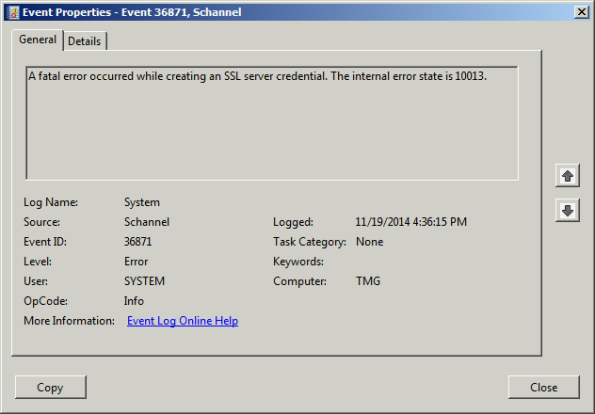
Looking through the Windows system event log you may see an error message logged by the Service Control Manager with event ID 36871 which states:
A fatal error occurred while creating an SSL server credential. The internal error state is 10013.
In addition you may also see an error message logged by the Service Control Manager with event ID 7024 which states:
The SQL Server (ISARS) service terminated with service-specific error %%-2146893007.

This can occur when SSL 3.0 is disabled at the same time that TLS 1.0 is also disabled. Even though TLS 1.1 and 1.2 might be enabled, TMG requires that TLS 1.0 specifically be enabled for SQL server services to function properly when SSL 3.0 is disabled.
To resolve this issue, enable TLS 1.0 Server in the registry by changing the value of Enabled to 1, as shown here. If these registry keys do not exist, create them.

Restart the server for the change to take effect.
Mitigating the POODLE SSL 3 Vulnerability on Forefront TMG 2010
Recently a new and very serious vulnerability in the SSL 3.0 protocol has been discovered that allows an attacker to recover sensitive information for an encrypted session. The Qualys SSL Labs server test has been updated to identify and warn about this issue.
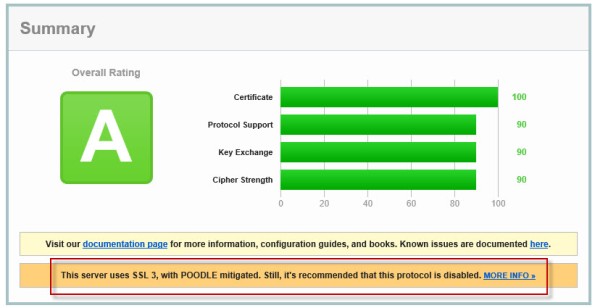
Figure 1 – Qualys SSL Labs Server Test Score for TMG Published Secure Web Site
On a Forefront TMG server with SSL hardening implemented as I’ve outlined here and here, the POODLE attack is mitigated, but it is still recommended that you disable SSL 3.0 altogether. SSL 3.0 is an old, outdated protocol that is no longer widely used, and disabling it should have minimal impact on clients connecting to secure web sites published by the Forefront TMG 2010 firewall.
To disable SSL 3.0 on the TMG firewall, open an elevated PowerShell window and execute the following commands:
New-Item -Path “HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server” -Force
New-ItemProperty -Path “HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server” -PropertyType dword -Value 0 -Name Enabled
Note: Use caution when copying/pasting the above commands as wrapping of the text has occurred.
A restart of the server is required for the change to take effect.
Hotfix Rollup 3 for Forefront TMG 2010 SP2 Now Available
Hotfix rollup 3 for Microsoft Forefront TMG 2010 with Service Pack 2 is now available for download. This latest hotfix rollup includes fixes for the following issues:
KB2700248 – A server that is running Forefront TMG 2010 may stop accepting all new connections and may become unresponsive
KB2761736 – All servers in a load balanced web farm may become unavailable in Forefront TMG 2010
KB2761895 – The Firewall service (wspsrv.exe) may crash when the firewall policy rules are reevaluated in Forefront TMG 2010
KB2780562 – PPTP connections through Forefront TMG 2010 may be unsuccessful when internal clients try to access a VPN server on the external network
KB2780594 – A non-web-proxy client in a Forefront TMG 2010 environment cannot open certain load-balanced websites when TMG HTTPS inspection is enabled
KB2783332 – You cannot log on when FQDN is used and authentication delegation is set to “Kerberos constrained delegation” in a Forefront TMG 2010 environment
KB2783339 – A closed connection to a domain controller is never reestablished when authentication delegation is set to “Kerberos constrained delegation” in a Forefront TMG 2010 environment
KB2783345 – Unexpected authentication prompts while you use an OWA website that is published by using Forefront TMG 2010 when RSA authentication and FBA are used
KB2785800 – A “DRIVER_IRQL_NOT_LESS_OR_EQUAL stop error may occur on a server that is running Forefront TMG 2010
KB2790765 – A “Host Not Found (11001)” error message occurs when an SSL site is accessed by using a downstream Forefront TMG 2010 server that has HTTPS Inspection enabled
You can download hotfix rollup 3 for Forefront TMG 2010 SP2 here. After applying this update, the new Forefront TMG 2010 build number will be 7.0.9193.575.
Discussing Forefront TMG 2010 SP2 on Security Talk
Recently I had the privilege to appear with my good friends Tom Shinder and Yuri Diogenes on their video series Security Talk. We spent most of the time discussing new features and capabilities provided by Service Pack 2 (SP2) for Forefront TMG 2010. Click here to watch. Enjoy!
Microsoft Security Bulletin MS11-083 and Forefront TMG 2010
Included in the November Microsoft security bulletin release was security update MS11-083 (KB2588516) that addresses a critical vulnerability in TCP/IP that could allow remote code execution. Forefront TMG 2010 firewalls are protected from this vulnerability, as the firewall engine’s kernel mode driver processes packets even before the operating system sees them. More information about how the Forefront TMG 2010 firewall engine and service work can be found here [this document is for ISA, but TMG is similar]. Although the underlying operating system’s TCP/IP networking stack is protected by the Forefront TMG firewall engine driver, TMG administrators are still strongly encouraged to install the MS11-083 update as soon as possible.
Forefront TMG 2010 Firewall Client Hotfix Rollup – October 2011
A hotfix rollup for the Forefront TMG 2010 firewall client is now available that resolves several issues reported on client systems with the TMG firewall client installed. They are:
KB2620156 – An active FTP data channel cannot be established for an internal computer that is running the Forefront TMG 2010 firewall client.
KB2438187 – You cannot start a program that is installed many levels deep and that requires an Internet connection using the Forefront TMG 2010 firewall client.
KB2620191 – Security update 2520426 causes a regression on a computer that is running the Forefront TMG 2010 firewall client.
KB2620153 – A program experiences a 20-second delay when an established internal or external connection is closed when the Forefront TMG 2010 firewall client is installed.
The Forefront TMG 2010 firewall client hotfix rollup can be downloaded here. After applying this hotfix rollup, the new Forefront TMG 2010 firewall client build number will be 7.0.7734.186.

Vulnerability in the Forefront TMG 2010 Client Could Allow Remote Code Execution
It is extremely rare to see a security update for anything relating to the Forefront TMG firewall. However, the June 2011 security bulletin includes update MS11-040 that addresses a privately reported vulnerability in the Forefront TMG client that could allow remote code execution. This security update applies only to the Forefront TMG client, not the firewall itself. Also, it does not apply to previous versions of the ISA firewall client.
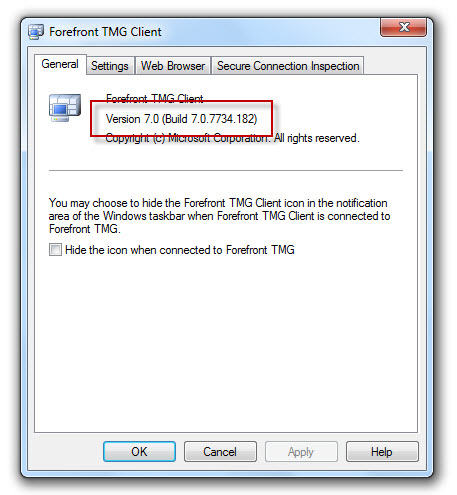
Before applying the MS11-040 update, the latest version of the Forefront TMG client was build 7.0.7734.100. After applying the MS11-040 update, the new build number will be 7.0.7734.182.
Security Update for Microsoft ISA Server 2006 (MS09-031)
Microsoft today announced the availability of a security update for Microsoft ISA Server 2006. This update addresses a vulnerability with RADIUS One Time Password (OTP). This update is rated important, and affects only ISA Server 2006 (and only in very specific scenarios). Previous versions of ISA are not affected, nor is Forefront Threat Management Gateway. For additional information, please read this post from the ISA product team.