Archive
Controlling Access to File Shares with Forefront TMG 2010
Consider a scenario in which you have an IIS server located in a perimeter network protected by Forefront TMG 2010. The server is published to the Internet and is used to display product information for your company. Web content developers on your internal network need to have access to file shares on the IIS server to upload new web content. To facilitate this access you create an access rule to allow CIFS access to the IIS server. For security reasons you decide to restrict access to members of the Web Content Developers domain group. In addition, your workstations have the Forefront TMG Firewall Client installed. The access rule looks like this:
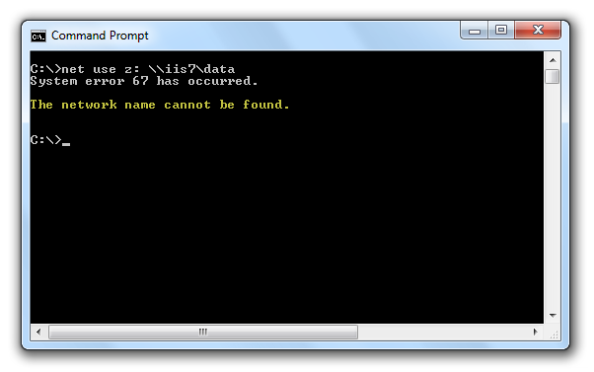
When users attempt to map a drive to the file share on the web server they receive the following error message:
System error 67 has occurred. The network name cannot be found.
In addition, the Forefront TMG 2010 firewall log indicates the following:
Denied Connection Log Type: Firewall Service Status: The action cannot be performed because the session is not authenticated.

At this point you might be puzzled because you have the Forefront TMG Firewall Client is installed on the workstation. TMG Firewall Client communication is always authenticated, so why does the firewall log indicate otherwise? The answer is simple. The Forefront TMG 2010 Firewall Client is a Layered Service Provider (LSP) that listens for Winsock calls made by the operating system and applications. Any Winsock calls made for resources on a remote network will be transparently delivered to the proxy server by the Firewall Client. However, CIFS communication does not use Winsock, so the TMG Firewall Client does not handle this traffic. As such, the network requests are delivered to the Forefront TMG firewall as SecureNAT requests. Since the rule in question requires authentication, and SecureNAT traffic cannot be authenticated, the firewall appropriately denies the traffic and the request fails.
You can resolve this issue by removing authentication on the access rule and controlling access on the file share itself. If you want to enforce user and group authentication at the firewall, consider using another protocol such as FTP.
For more information about the Forefront TMG 2010 Firewall Client and CIFS connections, please review Microsoft Knowledge Base article 913782.
New DirectAccess Blog
For anyone interested in news and information about Microsoft DirectAccess, I have started another blog at directaccess.richardhicks.com. With this blog I’ll be writing about DirectAccess in Windows Server 2008 R2, Forefront Unified Access Gateway (UAG) 2010 DirectAccess, and DirectAccess in Windows Server 2012. In addition, I’ll be touching on topics related to VPN and remote access in general, IPv6, and core networking. DirectAccess is the way of the future for managed client remote access, so I would encourage you to follow my blog and stay up to date with this wonderful technology. Of course I’ll still continue to write about edge security and Forefront TMG 2010 here, don’t worry!
IP Spoofing Alert from APIPA Address in Forefront TMG 2010
Security administrators may encounter the following IP spoofing alert on their Forefront TMG 2010 firewall:
Alert: IP Spoofing Description: Forefront TMG 2010 detected a possible spoof attack from the IP address 169.254.x.x. A spoof attack occurs when an IP address that is not reachable through the network adapter on which the packet was received. If logging for dropped packets is enabled, you can view the details of this attack in the firewall log in Forefront TMG 2010 log viewer. If the IP address belongs to a VPN client, this event may be ignored.

This alert occurs because the Forefront TMG 2010 firewall received a packet on its internal network interface from a client (server, workstation, or other host) that did not have a statically assigned IP address and was not able to obtain one from DHCP, so the client selected an IP address from the Automatic Private IP Address Assignment (APIPA) address range defined in RFC 3927.
You can safely ignore this alert, or you can resolve the issue by adding the APIPA reserved network 169.254.0.0/16 to the Internal network definition. This can be accomplished by opening the Forefront TMG 2010 management console and highlighting the Networking node in the navigation tree, then right-clicking the Internal network, selecting the Addresses tab, then clicking the Add Private button and choosing the address range 169.254.0.0 – 169.254.255.255.

Note: It is possible to resolve this issue by disabling alerts for IP spoofing attempts. However, this is considered bad security practice and is strongly discouraged.
You may recall from an earlier blog post I indicated that the best way to configure the Internal network definition in Forefront TMG 2010 is to choose the Add Adapter option. This still remains true. However, this is one of those rare cases in which you’ll want add an additional network address space to your Internal network definition to reduce the volume of IP spoofing alerts being raised by the Forefront TMG 2010 firewall.
The one side effect to implementing this change is that you will now receive a Configuration error alert informing you that your Internal network does not correlate with the network adapters that belong to it.
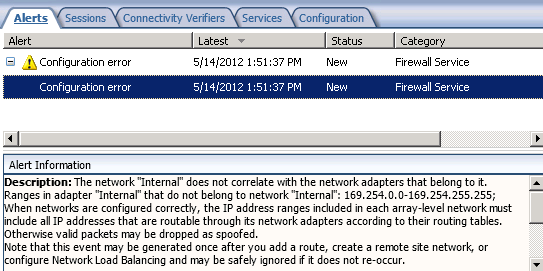
Essentially you have traded one annoying alert for another. However, the noise generated by IP spoofing alerts from clients with APIPA IP addresses might make this tradeoff worthwhile. In addition, it is much safer to disable the configuration error alert than it is the IP spoofing alert.
Hotfix Rollup 2 for Forefront TMG 2010 SP2 Now Available
The latest hotfix rollup for Forefront TMG 2010 SP2 is now available. This update includes fixes for the following issues:
KB2701952 – “Access is denied” status error when you use a delegated user account to try to monitor services in Forefront TMG 2010.
KB2700248 – A server that is running Forefront TMG 2010 may randomly stop processing incoming traffic.
KB2700806 – Connectivity verifier that uses the “HTTP request” connection method may not detect when a web server comes back online in Forefront TMG 2010.
KB2705787 – The Firewall service may intermittently crash when it processes client web proxy requests in a Forefront TMG 2010 environment.
KB2701943 – Error message when you try to join a Forefront 2010 server to an array: “The Operation Failed. Error code – 0x80070002 – the system cannot find the file specified”.
KB2705829 – The Firewall service may stop responding to all traffic on a server that is running Forefront TMG 2010.
KB2694478 – Dynamic Caching may incorrectly delete recently cached objects from a caching server that is running Forefront TMG 2010 or ISA Server 2006.
You can download hotfix rollup 2 for Forefront TMG 2010 SP2 here. After applying this update, the new Forefront TMG 2010 build number will be 7.0.9193.540.





