Archive
Extending the Life of Forefront TMG 2010 with Zscaler Cloud Based Security
Forefront TMG End of Life
With the end of life announcement for Microsoft Forefront TMG 2010, one of the most common questions I am asked is “What should I replace my Forefront TMG firewall with?” Many are surprised when I reply “Why do you want to replace it?” Simply because Forefront TMG will not be developed in the future does not mean there’s an immediate need to replace it. Considering the fact that Forefront TMG mainstream support extends until April 2015, and extended support lasts until April 2020, often the decision to replace TMG is nothing more than a knee-jerk reaction to marketing pressure by vendors of competing solutions.
Do You Need to Replace Forefront TMG 2010 Now?
If you have deployed Forefront TMG 2010 as a firewall, basic forward or reverse web proxy, or remote access or site-to-site VPN, there is no need to replace Forefront TMG 2010 right now. All of the features used in these deployment scenarios will continue to function in to perpetuity. You have until April 2020 to find a replacement for Forefront TMG, which should give you plenty of time to consider alternative solutions. However, if you have deployed Forefront TMG as a secure web gateway, the situation is a little different. Although support for the product extends until April 2020, the Web Protection Service (WPS) subscription will only function until the end of 2015. This means that URL filtering reputation database updates, antimalware signatures, and Network Inspection System (NIS) signatures will no longer be updated past this time. Not to worry, there are some excellent cloud-based security solutions that can be integrated with Forefront TMG 2010 to effectively extend the life of TMG for the foreseeable future.
Extending the Life of Forefront TMG 2010 with Zscaler
Recently I had the opportunity to evaluate the Zscaler Cloud-based security solution. Zscaler provides security-as-a-service and integrates seamlessly with Forefront TMG to provide essential web security protection with URL filtering, dynamic web content control, virus and malicious software scanning, HTTPS inspection capabilities, and more. The Zscaler security solution provides significantly more protection than the native Forefront TMG technologies offer. There are also tremendous economies of scale to be gained by using this cloud-based security solution, as Zscaler has more than 4000 enterprise customers in 180 countries, servicing more than 10 million users globally. The threat intelligence gained from having such a broad view of Internet activity worldwide enables Zscaler to quickly identify emerging threats on a global basis and extend protection to all of its customers quickly and effectively.
Zscaler Integration with Forefront TMG 2010
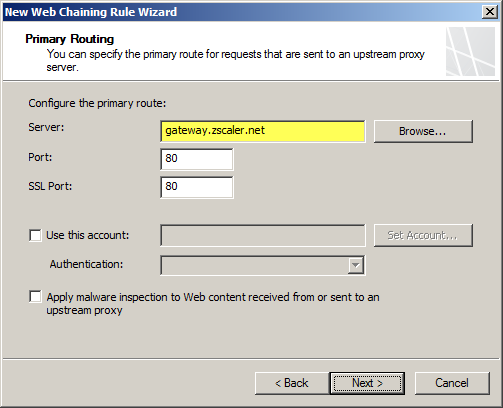
Integrating an on-premises Forefront TMG firewall with the Zscaler cloud is accomplished without having to install a plug-in on the TMG firewall. On-premises web traffic is delivered to the Zscaler cloud service by Forefront TMG through the use of web proxy chaining rules. After you’ve signed up for the service, simply configure a web proxy chaining rule to forward web proxy requests from Forefront TMG to the Zscaler cloud proxy gateways.

Zscaler Protection for Mobile Users
The Zscaler solution has some additional advantages over Forefront TMG’s native web protection mechanisms. With a cloud-based solution, Zscaler’s protection can also be extended transparently to mobile users, keeping them safe regardless of where they are. Zscaler has more than 100 datacenters worldwide, ensuring quick response times and low latency wherever the mobile user happens to be. Integrating individual clients can be done using proxy PAC files to route traffic to Zscaler’s datacenters. Additionally there is an option to install an agent on the client to forward traffic, which has the benefit of preventing the end user from disabling proxy settings to bypass content filtering restrictions.
Forefront TMG 2010 and Zscaler – Better Together
You may be asking yourself “Why not just use Zscaler exclusively? Why do I need TMG at all?” Valid question! Integrating Zscaler with Forefront TMG provides the best of both worlds in terms of security and performance. With Forefront TMG 2010 on premises, you have a Common Criteria-certified enterprise-class firewall to provide the highest level of security for your network. You can leverage strong user and group-based authentication, and you gain the added benefit of local caching for web content. In addition, you can make use of Forefront TMG 2010’s other features like multi-networking to create perimeter or DMZ networks for isolating public-facing services, reverse proxy for on-premises web-based and non-web based applications and services, remote access VPN for managed and non-managed mobile users, and site-to-site VPN to connect remote offices, business partners, or cloud service providers.
Forefront TMG End of Sale? Not Quite!
Although Microsoft is committed to supporting Forefront TMG 2010 for many years to come, they are no longer selling Forefront TMG 2010 licenses or the Web Protection Service (WPS) subscription licenses. If you’ve already deployed Forefront TMG 2010, or have already purchased Forefront TMG processor licenses and the WPS subscription, you have nothing to worry about. If you’re looking to deploy Forefront TMG 2010 today, you can’t purchase licenses for the software from Microsoft. However, you can still obtain Forefront TMG 2010 through a Microsoft OEM partner like Celestix Networks. (Full disclosure: Celestix Networks is my current employer.)
Keep Calm and Carry On
In my estimation, you can safely deploy or keep Forefront TMG 2010 in your environment and still gain a healthy return on your investment for many years to come. If you’re using Forefront TMG for publishing services such as Outlook Web App (OWA) or SharePoint, or you’re leveraging client-based remote access or site-to-site VPN, you have nothing to worry about. If you’re using Forefront TMG as a secure web gateway, you can enhance and extend the solution by using Zscaler’s cloud-based security solution for less than you would have paid for the Microsoft WPS subscription. No need to go out and replace your Forefront TMG 2010 solution for quite a few more years! If you are considering a new deployment, you can still purchase Forefront TMG 2010 from Microsoft OEM partners like Iron Networks. So Keep Calm and Deploy Forefront TMG 2010 today!

Citrix NetScaler Forefront TMG 2010 Replacement White Paper
With the formal end of life announcement for Forefront TMG 2010 last year, many firewall and secure web gateway vendors have been touting themselves as replacements for TMG. The folks at Citrix recently made available a white paper [PDF] making their case as a comprehensive replacement for Forefront TMG. While I don’t have any personal experience with the NetScaler solution, it does appear to have many of the features that TMG administrators have come to rely upon, such as URL filtering, virus and malicious software inspection, SSL termination (HTTPS inspection), content caching, low-level intrusion detection and prevention, and VPN capabilities. In addition, the NetScaler supports flexible network placement with edge, back firewall, and unihomed (single-legged or one-arm) deployment options. The solution is available in both hardware appliance form factor and virtual appliance.
Citrix makes an attempt to position their solution as the ideal and comprehensive replacement for Forefront TMG, and while it does have many features that TMG provides there is one glaring omission – an alternative to the Forefront TMG Firewall Client. ISA and TMG administrators have long used the Firewall Client to provide seamless and transparent proxy services for Winsock applications. The firewall client enables fully authenticated proxy support for non-web based protocols, and it appears that the NetScaler does not include such capabilities.
As with most white papers comparing solutions like this, it is helpful to understand they are essentially marketing material designed to downplay the features of the competing solution while often embellishing their own features. There are also some inaccuracies with regard to Forefront TMG capabilities, which is also not uncommon in documents such as these. For example, the document states that Forefront TMG 2010 failover requires three nodes, which is incorrect. You can easily create a standalone array using Forefront TMG 2010 Enterprise Edition using two nodes.
Overall the Citrix NetScaler looks like a pretty good solution. If you are in the market today for an alternative to Forefront TMG 2010 (…and should you be? That’s a topic for a future post, so stay tuned!) then download their white paper and take a closer look.
Configuring Forefront TMG 2010 HTTPS Inspection Inclusion List
When HTTPS inspection is configured and enabled on a Forefront TMG 2010 firewall, the administrator has the option to define web sites to exclude from HTTPS inspection. This may be required for a variety of reasons. For example, an administrator may need to exclude certain destinations to address privacy concerns, or perhaps HTTPS inspection breaks an application that uses SSL to tunnel non-HTTP protocols. All HTTPS web sites are inspected except for those sites defined as Destination Exceptions.

Beginning with Service Pack 2 (SP2) for Forefront TMG 2010, administrators can now define an explicit inclusion list for HTTPS inspection. Sites included on this list will be subject to HTTPS inspection, while all other destinations will be excluded. To define an HTTPS inspection inclusion list, create a Domain Name Set and populate it with those destinations for which you explicitly want to enforce HTTPS inspection.
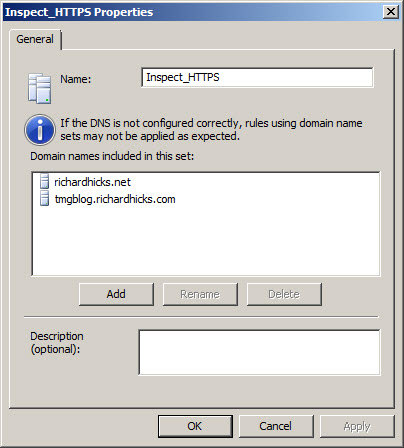
After saving and applying the configuration, copy this VBScript file to the TMG firewall, then open an elevated command prompt and type the following command:
cscript.exe ConfigureHTTPSiInclusionList.vbs <DomainNameSetName>
Substitute <DomainNameSetName> in the command above with the name of the Domain Name Set created earlier. Once configured, the Destination Exceptions tab of the HTTPS Outbound Inspection properties will be greyed out, and only those sites included in the Domain Name Set defined as the HTTPS inspection inclusion list will be subject to HTTPS inspection. All other destinations will be excluded. You can still define Source Exceptions as needed, however.

Only one Domain Name Set can be specified as the HTTPS inspection inclusion list. Running the command without parameters removes any configured inclusion list and returns HTTPS inspection back to its original state.
For more information regarding HTTPS inspection inclusion lists, refer to KB2619986.




