Archive
Implementing DirectAccess with Windows Server 2016 Now Available
I am very excited to announce that my new DirectAccess book, “Implementing DirectAccess with Windows Server 2016“ from Apress media, is now shipping! The book is available on popular online sites like Amazon.com, Barnes & Noble, Springer.com, Apress.com, and others. The book is also available in electronic formats such as Amazon Kindle and Barnes & Noble Nook, as well as a variety of subscription formats including Safari, Books24x7, and SpringerLink.
This book contains detailed and prescriptive guidance for the planning, design, implementation, and support of a DirectAccess remote access solution on Windows Server 2016. It also includes valuable insight, tips, tricks, and best practice recommendations gained from my many years of deploying DirectAccess for some of the largest organizations in the world.
Current DirectAccess administrators will also find this book helpful, as the majority of content is still applicable to DirectAccess in Windows Server 2012 and Windows Server 2012 R2. In addition, the book also includes essential information on the design and deployment of highly available and geographically redundant DirectAccess deployments.
Troubleshooting DirectAccess can be a daunting task, so I’ve dedicated an entire chapter in the book to this topic. For those responsible for the maintenance and support of DirectAccess in their organization, this chapter alone will be worth the investment.
Be sure to order your copy today!
Hotfix Rollup 2 for Forefront UAG 2010 Service Pack 4 Now Available
Hotfix Rollup 2 for Microsoft Forefront UAG 2010 Service Pack 4 is now available for download. This hotfix rollup includes fixes for the following issues:
KB3066351 – Client HTTP connections to a UAG redirect trunk receives errors after you install hotfix rollup 1 for Forefront UAG 2010 SP4
KB3070067 – You may receive an HTTP 503 “Service is Unavailable” error when a connection to a UAG trunk fails in Forefront UAG 2010 SP4
KB3068283 – You may receive HTTP 503 errors on a server that is running Forefront UAG 2010 SP4
KB3068289 – Moving mailboxes as part of a hybrid Office 365 migration fails in Forefront UAG 2010 SP4
You can download Hotfix Rollup 2 for Forefront UAG 2010 SP4 here.
Publish DirectAccess with Forefront TMG 2010
DirectAccess is a compelling remote access solution that provides seamless and transparent, always-on, bi-directional remote corporate network connectivity for managed Windows clients. In Windows Server 2008 R2 and Forefront Unified Access Gateway (UAG) 2010, the DirectAccess server had to be configured with two network adapters, with the external network interface configured with two consecutive public IPv4 addresses. Many security engineers were understandably concerned about exposing a domain-joined Windows server directly to the public Internet, which limited the adoption of the technology. Beginning with Windows Server 2012, DirectAccess is integrated in to the operating system and provides more flexible network configuration. DirectAccess can now be deployed behind an existing edge security solution performing NAT, and even supports single-NIC configuration.
The Forefront TMG 2010 firewall is an excellent choice to provide essential protection for the DirectAccess workload. When DirectAccess is deployed behind a NAT device, the only firewall port that needs to be opened is TCP port 443 (HTTPS).
When publishing DirectAccess with TMG, it is important to use a server publishing rule and not a web publishing rule. To publish DirectAccess, open the Forefront TMG 2010 management console, right-click Firewall Policy in the navigation tree, and then choose New Non-Web Server Publishing Rule.
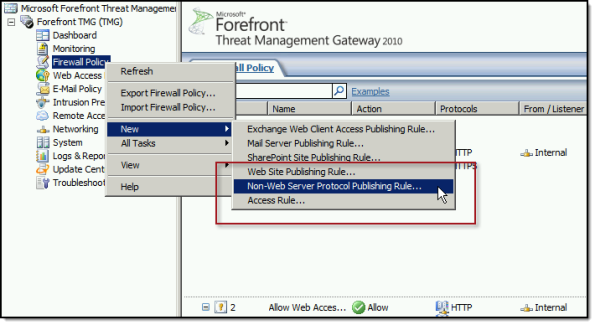
Provide a descriptive name for the rule, enter the IP address of the DirectAccess server, choose HTTPS Server for the protocol, and then select the network interface on which to listen for these requests.
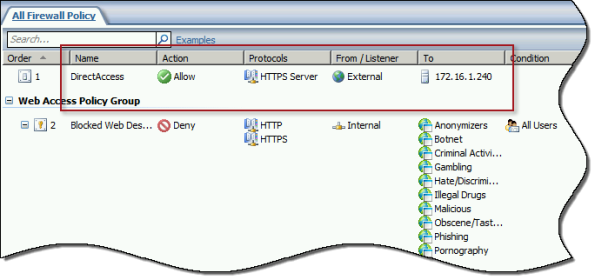
To ensure the proper operation of Receive Side Scaling (RSS) on the DirectAccess server, it is recommended that the server be configured to use TMG as its default gateway and to configure the publishing rule on TMG using the option Requests appear to come from the original client.
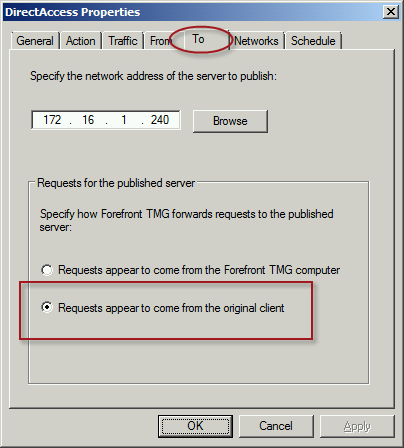
Also, TMG does not support load balancing for server publishing rules, so it is not possible to deliver traffic to multiple back end servers using TMG. For high availability and to provide for scalability, it is recommended to configure load balancing for DirectAccess using NLB or an external load balancer (recommended) and publish the virtual IP address (VIP) using the steps described above.
To learn more about DirectAccess, visit http://directaccess.richardhicks.com/
Recommended Forefront TMG 2010 SSL and TLS Configuration
Last year I wrote an article for ISAserver.org that provided detailed guidance for improving security for SSL and TLS protected web sites using Forefront TMG 2010. Many people have reached out to me recently to ask about enabling forward secrecy, which my original article did not include because, at the time, it was not recommended to enable it. However, as times have changed, it is now recommended to enable forward secrecy so I recently wrote a short post with guidance on how to do that. The post was written with a very narrow scope and addressed only the enabling of forward secrecy for TLS. Many of you have since asked for guidance on overall security best practices with regard to SSL and TLS along with adding support for forward secrecy. In addition to the configuration changes detailed in my original ISAserver.org article, I also recommend the following list of SSL and TLS cipher suites be explicitly enforced using the method outlined here.
TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256_P256 TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256_P384 TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256_P521 TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384_P384 TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384_P521 TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256_P256 TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA_P256 TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA_P256 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256_P256 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384_P256 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA_P256 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA_P256 TLS_DHE_DSS_WITH_AES_128_CBC_SHA256 TLS_DHE_DSS_WITH_AES_256_CBC_SHA256 TLS_DHE_DSS_WITH_AES_128_CBC_SHA TLS_DHE_DSS_WITH_AES_256_CBC_SHA TLS_RSA_WITH_AES_128_CBC_SHA256 TLS_RSA_WITH_AES_256_CBC_SHA256 TLS_RSA_WITH_AES_128_CBC_SHA TLS_RSA_WITH_AES_256_CBC_SHA
Using this configuration, the Forefront TMG 2010 firewall should receive an A rating from the SSL Labs test site (at the time of this writing).
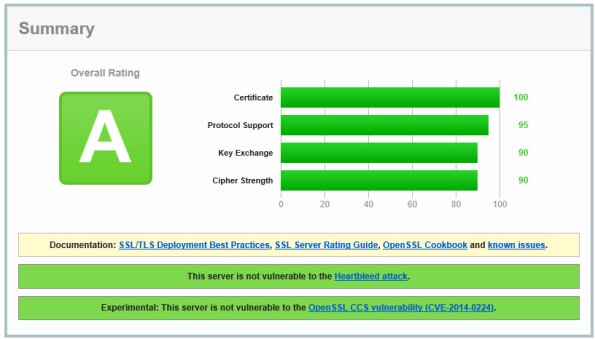
Enabling and supporting the above list of cipher suites will provide the best overall protection and performance for your SSL protected web sites. Note that the list above does not include support for SSL 3.0. If you need to support SSL 3.0 you should add the following cipher suites to the end of the list.
TLS_RSA_WITH_RC4_128_SHA TLS_RSA_WITH_RC4_128_MD5
Please note that this configuration may not work with older browsers on old, unsupported operating systems, for example Internet Explorer 6 on Windows XP. Before deploying this configuration in production I would encourage you to conduct some testing with your supported clients to ensure operability.
Enable TLS Forward Secrecy for Forefront TMG 2010 Published Web Sites
Last year I wrote an article for ISAserver.org that outlined in detail how to improve SSL and TLS security for web sites published using Forefront TMG 2010. In its default configuration, Windows Server 2008 R2 and Forefront TMG leave quite a bit to be desired in terms of SSL and TLS security. In the article I demonstrated how to dramatically improve the security posture of TMG when publishing web sites that use SSL and TLS. At the time I wrote the article it was not recommended to enable forward secrecy, so the changes I originally proposed resulted in an “A” score from the Qualys SSL Labs test site. However, times have changed since then, and with the recent revelations of wide spread government spying, it is now recommended to enable forward secrecy by default. Sites that don’t support forward secrecy will now receive a reduced grade.

To accomplish this on the Forefront TMG 2010 firewall, open the Local Group Policy Editor (gpedit.msc) and navigate to Computer Configuration, Administrative Templates, Network, SSL Configuration Settings. Double-click SSL Cipher Suite Order and choose Enabled. Copy the list of SSL cipher suites to a blank notepad document and then move all of the cipher suites that begin with TLS_ECDHE_RSA_WITH_AES_ to the front of the list. Use caution here because the list cannot have any extra commas, line breaks, or spaces at all. Paste the updated list back in to the SSL Cipher Suites box and click Ok.

The server will have to be restarted for the changes to take effect. Once complete, forward secrecy will now be used by modern browsers and you should once again receive an “A” grade from SSL Labs.

Forefront UAG 2010 End of Life Statement
Today, Microsoft announced the end of life for the Forefront UAG 2010 product. Microsoft will continue to provide mainstream support for UAG until April 14, 2015, and extended support until April 14, 2020. Existing customers with active Software Assurance on their existing UAG licenses as of December 1, 2013, may add new UAG server instances, users, and devices without having to purchase additional UAG licenses. In addition, existing customers who have purchased Forefront UAG server licenses will be given upgrade rights to Windows Server 2012 R2, which provides some of the remote access features found in Forefront UAG. For example, Windows Server 2012 R2 supports DirectAccess, client-based VPN, and reverse web proxy with new Web Application Proxy role.
With regard to license upgrade rights, users are entitled to a Windows Server 2012 R2 license for each Forefront UAG server license (or External Connector license) they currently own. Software Assurance for UAG can still be purchased until January 1, 2014. Forefront UAG 2010 will be removed from the pricelist on July 1, 2014. Forefront UAG 2010 will continue to be available from Microsoft OEM hardware partners like Celestix Networks for the foreseeable future, however.
Windows Azure Multifactor Authentication and Forefront TMG 2010
When Microsoft first announced Windows Azure Multi-Factor Authentication, a cloud-based strong authentication solution, my first thought was “I wonder if it works with Forefront TMG 2010?” Being cloud-based, my first thought was perhaps not. However, once I started digging in to it I quickly learned that it includes a software component that can be installed on-premises and will even integrate with on-premises security solutions via a number of interfaces, including RADIUS. Forefront TMG 2010 has supported RADIUS authentication for many years, so I put together a test lab and in no time at all I had Windows Azure multi-factor authentication working with Forefront TMG 2010 remote access VPN. Forefront TMG 2010 integrated with Windows Azure multi-factor authentication provides the highest level of protection for remote access users. Leveraging Windows Azure cloud-based strong authentication is extremely cost effective, with very low per user or per authentication costs and no on-premises hardware to purchase. The Windows Azure public cloud, which is ISO/IEC27001:2005 certified, provides the most secure and reliable strong authentication service available today. To learn how to configure Forefront TMG 2010 to work with Windows Azure multi-factor authentication, click here.
Publishing Exchange 2013 Outlook Web App with Forefront TMG 2010
Recently I wrote an article for ISAserver.org about publishing Exchange 2013 Outlook Web App (OWA) using Forefront TMG 2010. In spite of the fact that many organizations are migrating their e-mail services to the cloud, there are many organizations who cannot, for a variety of reasons, take advantage of cloud services for e-mail. This makes Exchange 2013 a compelling upgrade for many companies. Historically Forefront TMG 2010 and its predecessors were the go-to service for securing access to on-premises Exchange implementations. Forefront TMG 2010 supports OWA publishing with native publishing wizards, allowing you to select which version of Exchange you are publishing, with the added bonus of providing in-box forms-based authentication (FBA) templates that matched the look and feel of the Exchange version you were publishing. Since Forefront TMG 2010 has been deprecated, Microsoft has not updated Forefront TMG 2010 to include support for Exchange 2013 OWA. However, you can still publish Exchange 2013 OWA using Forefront TMG by following the instructions outlined in my ISAserver.org post. When using this method, the Exchange 2010 FBA templates are used. This makes the user experience somewhat disjointed, with the FBA pages not matching the new, updated look and feel of OWA 2013. To remedy this, I reached out to my good friend Scott Glew at Fastvue. Scott is a terrific web developer, as evidenced by the amazing UI included with the TMG Reporter solution. In short order, Scott whipped up some customized Forefront TMG 2010 FBA templates to match the look and feel of OWA 2013 and has made them available for free. Now if you’re publishing Exchange 2013 OWA using Forefront TMG 2010, you can download these custom templates and use them to provide a consistent experience for your Exchange OWA users. Enjoy!
Enable Hybrid Cloud with Forefront TMG 2010 and Windows Azure
Earlier this year I published an article on ISAserver.org on how to enable cross-premises network connectivity to Windows Azure using Forefront TMG 2010. When I wrote that piece, Windows Azure virtual networking was still in preview (beta). Since that time, Windows Azure virtual networking has been officially released, with some significant changes in features, functionality, and configuration steps. Many people noticed that their existing Forefront TMG 2010 to Windows Azure site-to-site VPN stopped working at this time and assumed that support for TMG had been dropped. Not so! Forefront TMG 2010 site-to-site VPN does work with Windows Azure virtual networks, and is indeed supported as it meets the minimum requirements for VPN devices connecting to Windows Azure virtual networks outlined here.
Configuring site-to-site VPN connectivity between the Forefront TMG 2010 firewall and Windows Azure virtual networks is not without a minor drawback, however. One of the new features of Windows Azure virtual networking is point-to-site VPN using SSTP. Unfortunately this feature requires that you configure dynamic routing on your Windows Azure virtual network, and dynamic routing makes use of IKEv2, which the Forefront TMG 2010 firewall does not support. So, if you want to enable cross-premises network connectivity to Windows Azure using Forefront TMG 2010, you will not be able to take advantage of this new point-to-site VPN connectivity option.
Important Note: Windows Azure virtual networking site-to-site VPN requires that your VPN endpoint have a public IPv4 address assigned to it’s external network interface. If your Forefront TMG 2010 firewall is located behind a border router or edge firewall performing NAT, site-to-site VPN connectivity with Windows Azure will not be possible.
To configure cross-premises network connectivity with Windows Azure, log in to the Windows Azure portal and select Networks in the navigation pane, then click on Create Virtual Network. Enter a Name for the virtual network, specify a Region, and provide an Affinity Group Name and select the appropriate Subscription.
Enter the names and IP addresses of any DNS servers to be used by machines in this virtual network and select the option to Configure site-to-site VPN. Do NOT select the option to Configure point-to-site VPN.
Provide a name for the site-to-site connection and enter the IP address assigned to the external network interface of the Forefront TMG firewall. In addition, specify the network address space in use on the private, on-premises side of the connection.
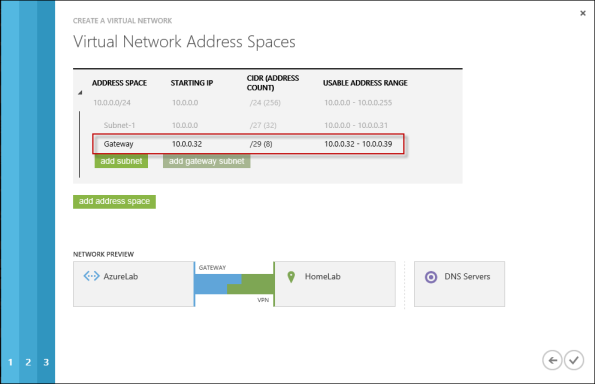
Define your virtual network subnet as required. Here I’ve chosen to use the 10.0.0.0/24 address space. Define any additional subnets as necessary and then click Add gateway subnet.
Click on the newly created virtual network and then click on Dashboard. Click Create Gateway and choose Static Routing.
Once the gateway has been created, make a note of the Gateway IP Address and then click Manage Key. Copy this key as it will be required when configuring the site-to-site VPN on the Forefront TMG 2010 firewall.
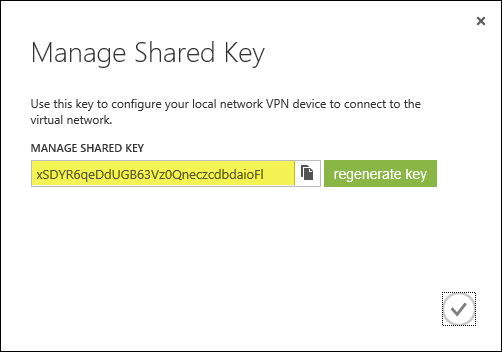
On the Forefront TMG 2010 firewall, open the management console and select Remote Access Policy (VPN). Click the Remote Sites tab in the center pane and then click Create VPN Site-to-Site Connection in the Tasks pane. When the Create Site-to-Site Connection Wizard begins, enter a name for the new site-to-site network.
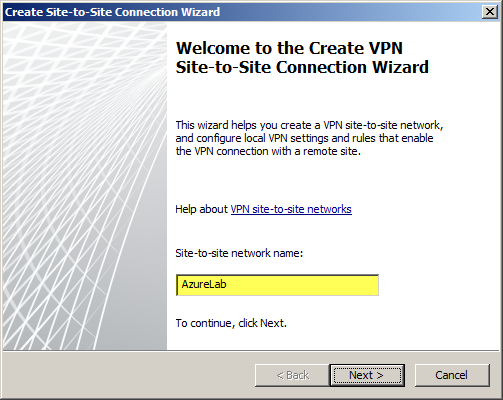
Select IP Security protocol (IPsec) tunnel mode.

Enter the IP address of the Windows Azure virtual network gateway and the local VPN gateway IP address, which is the IP address assigned to the external network interface of the Forefront TMG 2010 firewall.

Copy the pre-shared key from the Windows Azure virtual network gateway.
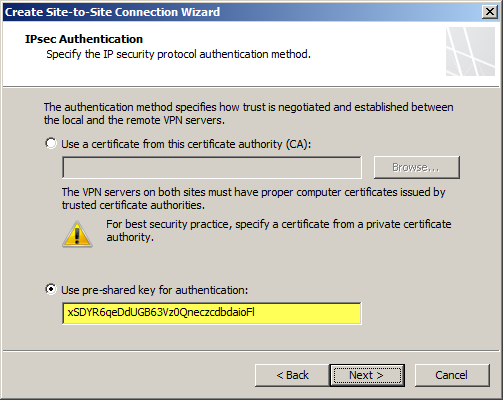
The IP address of the Windows Azure virtual network gateway will be automatically added to the network address list. Click Add Range and add the IP address range you defined earlier for the virtual network.
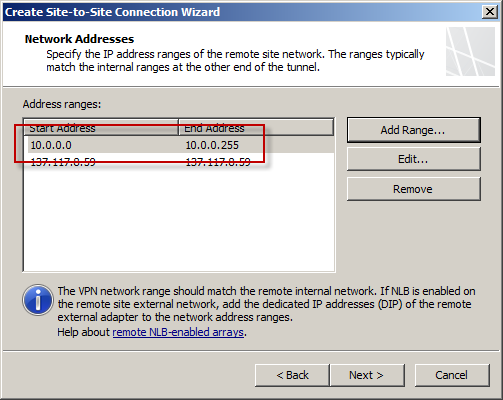
Select the option Create a network rule specifying a route relationship.

Any communication between the on-premises network and the Windows Azure virtual network must be allowed by firewall policy. You can create an access rule now, or create one later.
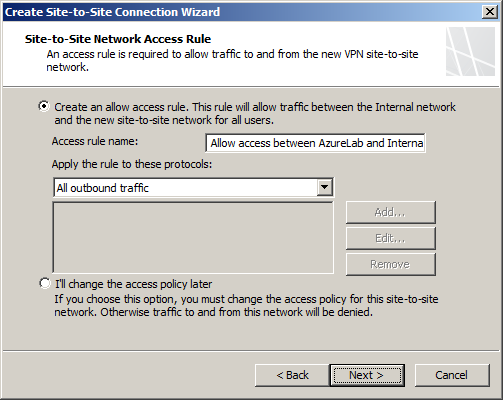
Review the configuration settings and click Finish.

Before applying the configuration, right-click the site-to-site connection and choose Properties, select the Connection tab, and then click IPsec Settings.
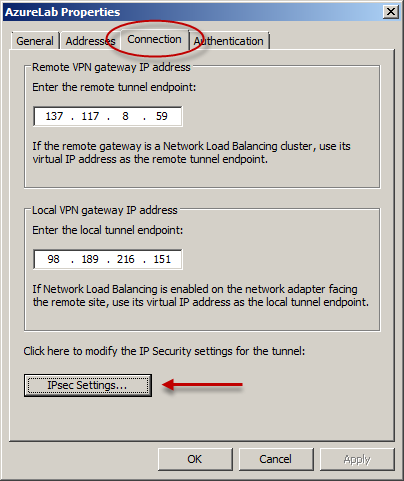
On the Phase I tab select SHA1 for the Integrity algorithm and leave the remaining settings at their defaults.

On the Phase II tab select SHA1 for the Integrity Algorithm. Select the option to Generate a new key every 102400000 Kbytes and clear the option to Use Perfect Forward Secrecy (PFS).
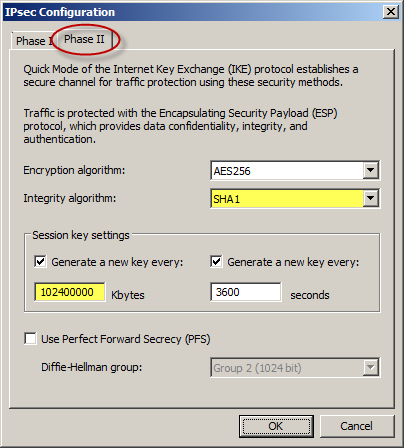
Once complete, apply the configuration. Finally, set the Maximum Transmission Unit (MTU) on the Forefront TMG 2010 firewall’s external interface to 1350 bytes by opening an elevated command prompt and issuing the following command:
netsh interface ipv4 set interface <interface_name_or_index> mtu=1350
For example:
netsh interface ipv4 set interface external mtu=1350
The Windows Azure management console should now indicate that you have successfully established a site-to-site VPN to the remote virtual network.
When you configure a new Windows Azure virtual machine, you can specify that the machine be placed in to your virtual network.
The new virtual machine should now be reachable from your on-premises network using the site-to-site VPN configured on the Forefront TMG 2010 firewall.
DirectAccess Session at Microsoft TechEd 2013
This month I had the honor and privilege to present a Windows Server 2012 DirectAccess session at Microsoft TechEd North America and Europe 2013. For those of you who attended in person, thank you very much! I certainly hope that you found the session informative and worthwhile. For those of you who were not able to attend in person, you can watch a recording of the session for free at Microsoft’s MSDN Channel 9 web site here. Enjoy!