Archive
Hotfix Rollup 1 for Forefront TM 2010 SP2 Now Available
A hotfix rollup for Forefront TMG 2010 SP2 is now available. The hotfix rollup resolves several reported issues with TMG, including:
KB2654016 – A client may be unsuccessful in accessing a Java SSO application published to the web by Forefront TMG 2010
KB2653703 – “Error: Subreport could not be shown” error message in the User Activity or Site Activity report in Forefront TMG 2010
KB2654585 – UDP packets may become backlogged when you increase the “maximum concurrent UDP sessions per IP address” setting in Forefront TMG 2010
KB2624178 – Forefront TMG 2010 administrators may be unable to generate reports
KB2636183 – Both sides of a TCP connection are closed when the client or remote application half-closes the TCP connection in Forefront TMG 2010
KB2653669 – Summary information for the Top Overridden URLs table and for the Top Rule Override Users table display incorrect information in Forefront TMG 2010
KB2617060 – Forefront TMG 2010 enables L2TP site-to-site connections in RRAS
KB2655951 – Japanese characters in the subject line of an Alert email message are not readable in the Japanese version of Forefront TMG 2010
KB2654068 – “The Web Listener is not configured to use SSL” warning message may occur when you configure a Web Listener to use a valid SSL certificate in Forefront TMG 2010
KB2654193 – You receive a “Bad Request” error message when you try to access Outlook Web App published by Forefront TMG 2010
KB2654074 – String comparison may become case-sensitive when you published a website using Forefront TMG 2010
KB2658903 – Forefront TMG 2010 firewall service (wspsrv.exe) may crash frequently for a published website secured by SSL after you install Service Pack 2.
Hotfix rollup 1 for Forefront TMG 2010 SP2 can be downloaded here. After applying this update, the new Forefront TMG 2010 build number will be 7.0.9193.515.
Unable to Retrieve Data from Array Members after Enabling Kerberos Authentication with NLB on Forefront TMG 2010
Immediately after configuring Forefront TMG 2010 to support Kerberos authentication with NLB, you may encounter a scenario where the Forefront TMG management console fails to communicate with the members of the array and includes the following error message:
Unable to retrieve data from: <array_members>

In addition, an Event ID 4 from the Security-Kerberos source is recorded in the system event log:
The Kerberos client received a KRB_AP_ERR_MODIFIED error from the server tmgsvc2. The target name used was tmg3$@richardhicks.net. This indicates that the target server failed to decrypt the ticket provided by the client. This can occur when the target server principal name (SPN) is registered on an account other than the account the target service is using. Please ensure that the target SPN is registered on, and only registered on, the account used by the server. This error can also happen when the target service is using a different password for the target service account than what the Kerberos Key Distribution Center (KDC) has for the target service account. Please ensure that the service on the server and the KDC are both updated to use the current password. If the server name is not fully qualified, and the target domain (RICHARDHICKS.NET) is different from the client domain (RICHARDHICKS.NET), check if there are identically named server accounts in these two domains, or use the fully-qualified name to identify the server.
When making the changes to support Kerberos authentication in load balanced scenarios, the Forefront TMG firewall service is configured to run in the context of a domain user account. When the Forefront TMG management console was first opened, it authenticated to the array members using the Service Principal Name (SPN) registered to the machine (computer) account. As the changes are applied and the services are restarted, the array members are now running in the context of a domain user account. However, the management console continues to send a Kerberos ticket with the SPN registered to the machine account. The Forefront TMG firewall service running in the context of the domain user account cannot decrypt this Kerberos ticket and replies with a Kerberos error.

Resolution in this case is quite simple. Closing the Forefront TMG management console and opening it again will force the client to re-authenticate, this time using the correct SPN. The Kerberos event log errors are anomalous and can safely be ignored.
Error 0x8004FE2F Activating Windows on Forefront TMG 2010 Protected Network
When attempting to activate Windows Server 2008R2 you may receive one of the following error messages:
A problem occurred when Windows tried to activate. Error Code 0x8004FE2F

Or…
A problem occurred when Windows tried to activate. Error Code 0xC004FC03

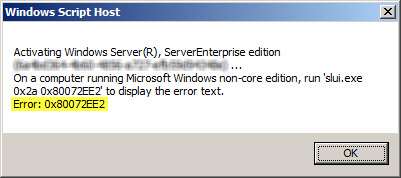
If you attempt to activate Windows from the command line using slmgr.vbs -ato you may also encounter one of the following error messages:
Activating Window Server(R), ServerEnterprise edition {GUID}...
On a computer running Microsoft Windows non-core edition, run 'slui.exe
0x2a 0x8004FE2F' to display the error text.
Error: 0x8004FE2F

Or…
Activating Window Server(R), ServerEnterprise edition {GUID}...
On a computer running Microsoft Windows non-core edition, run 'slui.exe
0x2a 0x80072EE2' to display the error text.
Error: 0x80072EE2
The problem may occur for systems that are located on a network that is protected by a Forefront TMG 2010 firewall, and the access rule that allows the traffic requires authentication. The Windows activation process relies on WinHTTP and by default, WinHTTP communication is sent as SecureNAT client traffic. SecureNAT clients unfortunately cannot be authenticated, so the request fails.
There are two ways resolve this issue. The first is to configure WinHTTP on the Windows system you are trying to activate to use a proxy serverexplicitly. Open an elevated command prompt and enter the following command:
netsh winhttp set proxy <name or IP address of proxy server>:<port>
For example:
netsh winhttp set proxy tmg.richardhicks.net:8080
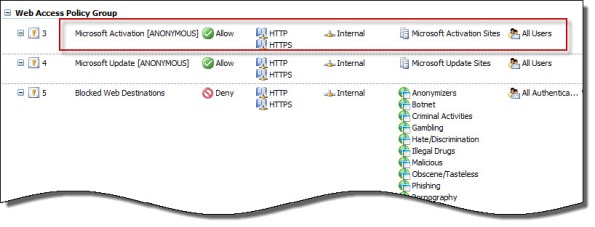
Instead of making this change to each system you want to activate, an alternative is to create an anonymous access rule on the Forefront TMG 2010 firewall that allows HTTP and HTTPS traffic to those destinations required to activate Windows. Using the Forefront TMG 2010 management console, create an access rule that allows HTTP and HTTPS from the Internal network to a Domain Name Set that contains the following destinations for all users:
activation.sls.microsoft.com.nsatc.net go.microsoft.com *.sls.microsoft.com
Make sure this rule is placed before any other rules for HTTP or HTTPS that require authentication.
Once configured, activating Windows should work without issue.