Reviewing the Microsoft ISA Server 2006 System Policy
By default, the Microsoft ISA Server firewall is configured to deny all traffic that is not explicitly permitted by an access rule. This means that the firewall administrator will need to configure a number of access rules in order to facilitate domain and client communication, among other things.
Thankfully the ISA firewall includes a set of system policy access rules that simplify the configuration and operation of the firewall. The system policy contains a set of pre-configured access rules that allow ISA and the underlying operating system to communicate with things such as domain controllers, DNS servers, authentication servers, etc. The system policy rules are hidden from view by default. If you wish to see the system policy rules themselves, right-click on the ‘Firewall Policy’ node, highlight ‘View’, and then select ‘Show System Policy Rules’.
To edit the system policy rules, right-click on the ‘Firewall Policy’ node and choose ‘Edit System Policy…’.
If you have chosen to display the system policy rules you can double-click any rule or right-click a rule and choose ‘Edit System Policy’ to bring up the system policy editor as well.
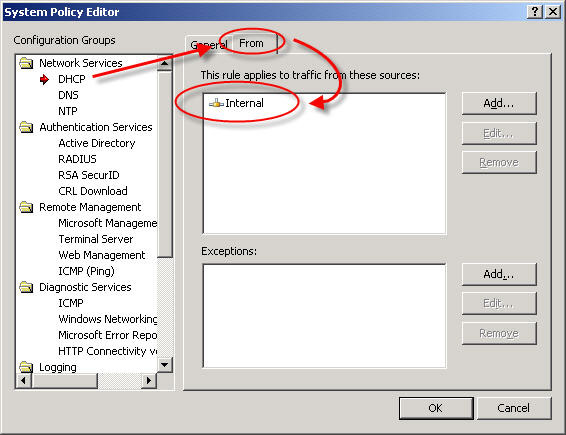
Although having pre-configured system policy rules is convenient, some of the rules are broad or may not be required in your environment. I would highly recommend that you review and edit the system policy prior to deploying a production Microsoft ISA firewall. For example, by default the system policy is configured to allow DHCP requests from the ISA firewall to the Internal network.
From a security perspective it would be best to specify which DHCP servers your ISA firewall can communicate with. Create new computer objects for each of your DHCP servers and specify them as the source for this rule instead of the entire Internal network. If none of your firewall’s network interfaces are configured to use DHCP you can safely disable this rule.
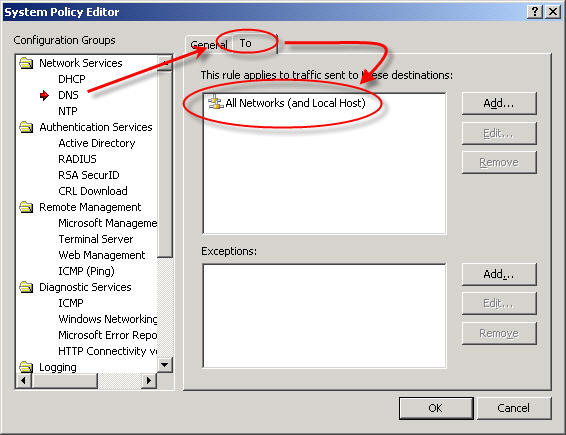
Another instance where the system policy can be tightened up is the DNS system policy rule. By default this rule allows the ISA firewall to communicate to DNS servers on all networks – and that includes the external network! (see Jason Jones’ blog post on proper ISA firewall network configuration)
This is an excellent opportunity to improve the security posture of your ISA firewall. I would recommend that you specify which DNS servers the ISA firewall can communicate with explicitly. Create new computer objects for each of your DNS servers and specify them as the destination for this rule, removing of course the ‘All Networks (and Local Host)’ network object.
One more example of broad system policy configuration is the SMTP system policy rule. By default this rule allows the ISA firewall to communicate to any SMTP server on the Internal network.
Again, your configuration will be much more secure if you specify which SMTP servers the ISA firewall can communicate with. If you are not using STMP notifications on the ISA firewall you can safely disable this rule.
These are only a few examples of areas where the system policy rule set can be tightened to improve security on the ISA firewall. Once you have completed your initial configuration, I would strongly encourage you to review and edit these policies. By disabling unnecessary rules and restricting the access on others you can enhance the already secure configuration of the ISA firewall.










Nice post Rich 😉
This approach should be part of any least privilege design/implementation and is actually quite easy to do.
Although Microsoft did a good job with system policy, it can never reflect the actual needs of the environment and therefore needs to be “tuned” as necessary by thinking about what the ISA deployment actually requires.
This approach is a standard part of our ISA builds and is also recommended in the ISA security guide IIRC. Personally, I try and disable as many policies as possible and then create specific computer sets for each rule to remove the default objects. Well worth spending 5 mins on any deployment if you ask me 😉
Cheers
JJ
Can you please give the link of the ISA Security Guide IIRC?
Thanks
http://technet.microsoft.com/en-us/library/bb794718.aspx
In System Policy Editor, what is Web Management section. How can I manage ISA Server by using Web applications?
Thanks
I believe this is a leftover from the old days when the operating system included a web-based management facility. There is no remote management utility for Microsoft ISA Server 2006, unless of course you have a Celestix MSA Series security appliance which does include a web-based management tool! If you are interested in seeing a demonstration, send me a note and I’ll provide you with a URL to our live online demonstration site.
Thanks for your reply.
When we look at the properties of this rule, in the Protocols tab, we can see the “ISA Server Web Management”. What this protocol? What do you mean about “old days when the operating system included a web-based management facility”?
Thanks a lot!
-Reza
This should provide some clarification – https://tmgblog.richardhicks.com/2009/07/14/microsoft-isa-server-2006-web-based-management-console/. Thanks!