Websense Integration Support for Forefront Threat Management Gateway (TMG) 2010
Updated July 11, 2011: Since this post was originally published, Websense now supports full integration with Forefront TMG 2010 with Websense Web Security/Web Filter v7.6.
There seems to be a fair amount of confusion regarding Websense integration support for Microsoft Forefront Threat Management Gateway (TMG) 2010. As you are most likely aware, TMG is 64-bit only and is supported only on Windows Server 2008 64-bit and Windows Server 2008 R2 64-bit. You cannot install TMG on any 32-bit operating system. By contrast, Websense Web Security and Web Filter today (July, 2010) are 32-bit only and are not supported on any 64-bit operating system. These architectural differences clearly limit the integration capabilities for Websense and TMG.
Recently Websense announced the availability of Websense Web Filter and Web Security v7.5, which now includes limited support for integration with TMG. In this release, no Websense components (with the exception of the filtering plug-in) can be installed on the TMG firewall system. In order to support Websense integration with TMG, you must have a separate system or systems on which to install the Websense policy, filtering, user identification, and logging/reporting components. For typical enterprise deployments this won’t be an issue, but this is disappointing news for many small to mid-sized customers who don’t need or want the extra overhead of multiple systems to provide URL filtering services. Another serious limitation is that Websense Web Filter and Web Security v7.5 are currently not supported on Windows Server 2008 R2, at all. If you have installed TMG on Windows Server 2008 R2, you are out of luck.
Thankfully, TMG includes native URL filtering capabilities that, when combined with other TMG advanced protection technologies such as integrated virus and malware scanning, HTTPS inspection, and the vulnerability-based intrusion detection and prevention system, provide a consolidated and comprehensive secure web gateway solution that ultimately affords more overall protection compared to URL filtering solutions alone. TMG includes a 120-day evaluation of these advanced web protection technologies (beginning at the time of product installation, not the activation of the URL filtering feature itself!) so there’s no obligation to try it out. Take it for a test drive…I think you’ll be impressed! It performs well, scales very effectively, and is much easier to manage than many third-party integrations.
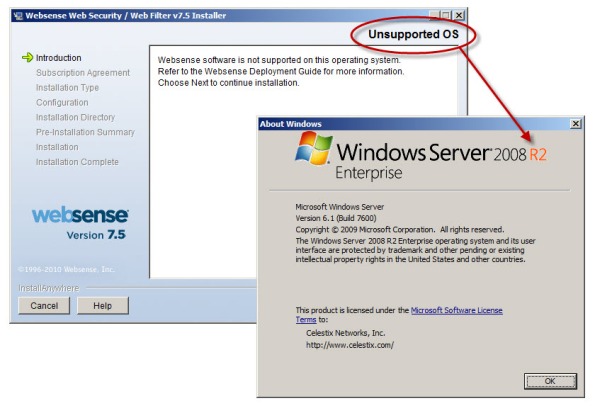





Didn’t know about it not supporting Windows 2008 R2. As much as I hate Websense they do a lot of things right when it comes to the actually filtering of web sites.
I was ready to ditch Websense and go to TMG (its a way way cheaper solution in comparison to Websense). One problem though HTTPS Inspection is required to block HTTPS websites. Let me explain. If I want to take advantage of URL filtering in TGM in terms of blocking HTTPS sites HTTPS Inspection must be on. The problem is that Firefox does not inherit the Windows CA root for our enterprise. So deploying this is an IE only thing.
On the other hand I can block any HTTPS in Websense as long as it falls into a blocked category.
I really wished TGM would do this.
Hi Richard,
Thanks for the information. I couldn’t resist adding a shameless plug here for WebSpy Vantage as it is a great alternative reporting solution that runs fine on Server 2008 R2. Here’s an article explaining how to set it up:
http://www.webspy.com/vendors/microsoft-ftmg/howto.aspx
Also checkout my video that outlines the major advantages of using WebSpy Vantage with TMG here:
http://www.webspy.com.au/blogs/index.php/8-reasons-not-to-use-microsoft-forefront-tmgs-reporting/
Thanks again. Your blog is a great source of information for ISA & TMG. Keep up the good work!
Cheers!
Scott.
TMG most certainly can block HTTPS sites without enabling HTTPS inspection enabled. What you don’t see is the TMG block page when the site is blocked, but the same is true for Websense or any other third-party URL filtering solution. You also get more accurate enforcement of URL filtering policies with HTTPS inspection enabled because TMG has access to the full URL.