Archive
Forefront TMG 2010 Protocol Direction Explained
When reviewing the configuration of a pre-defined protocol or creating a custom protocol on the Forefront TMG 2010 firewall, many new (and sometimes even veteran) firewall administrators can be confused by the protocol direction. The correct configuration of the protocol direction is essential for proper firewall operation, but there are times when it can be somewhat unintuitive. In this post I’ll provide some clarification.
TCP
For TCP protocols the direction can be specified as either inbound or outbound.
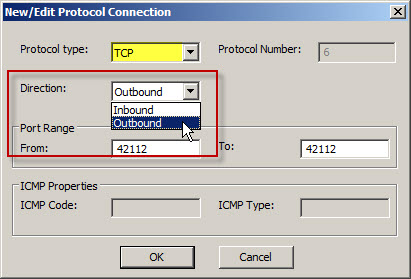
For access rules, protocol direction is configured as outbound. Traffic flows outbound from the source to the destination. This is true even when creating an access rule to allow traffic inbound to the Forefront TMG 2010 firewall itself. It sounds counterintuitive, but the TCP protocol direction for access rules allowing access to the Local Host network should still be outbound. Why? Again, because traffic flows outbound form the source to the destination, in this case the TMG firewall’s Local Host network. If, in this case, you were to configure the protocol direction as Inbound (intuitively, inbound to the TMG firewall) it will not work.
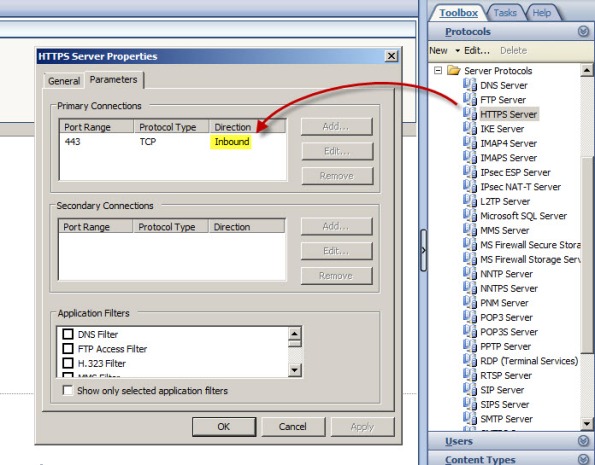
For publishing rules, protocol direction is configured as inbound. Traffic flows inbound from the source to the published service on the Forefront TMG 2010 firewall. Pre-defined server publishing protocols include the “server” suffix, as shown here:
UDP
For UDP protocols the direction can be specified as either Receive, Receive Send, Send, or Send Receive.
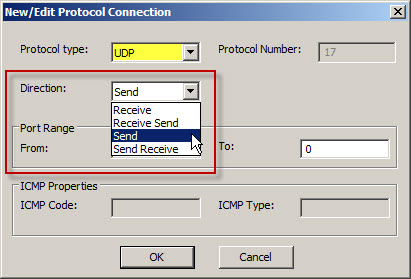
For access rules, protocol direction is configured as Send. Traffic is sent from the source to the destination. If a response is expected then the protocol direction is configured as Send Receive. This is required because UDP is connectionless and the return traffic would otherwise be denied by the TMG firewall.
For publishing rules, protocol direction is configured as Receive. Traffic is received by the TMG firewall from the source to the published service on the Forefront TMG 2010 firewall. If a response is expected then the protocol direction would be configured as Receive Send.
IP and ICMP
For IP and ICMP protocols the direction can be specified as either Send or Send Receive.

IP and ICMP protocol definitions are only supported for access rules, so protocol direction is configured as Send. As with UDP, IP and ICMP are connectionless and if a response is expected then the protocol direction is configured as Send Receive.
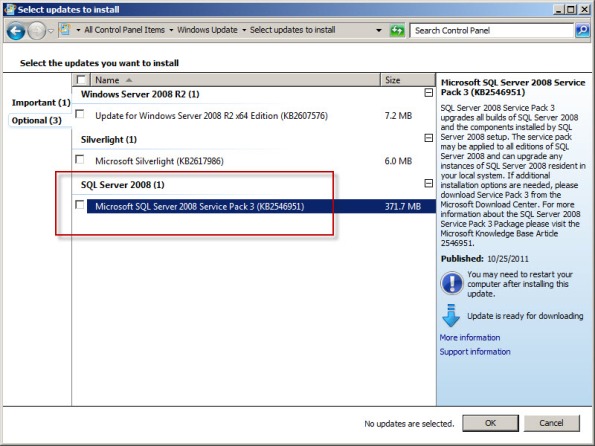
Updating SQL Server on Forefront TMG 2010
Keeping the base operating system of your Forefront TMG 2010 firewall up to date is vitally important to the overall security of your edge security solution. To manage system updates, many administrators will configure their Forefront TMG 2010 firewalls to use Windows Update or WSUS, or manage them using System Center Configuration Manager (SCCM) or another third-party systems management platform.
In my experience, SQL server running on the Forefront TMG 2010 firewall is often overlooked and commonly not updated. I believe this happens because updates for SQL server are classified as optional.
So, as a reminder, don’t overlook updates for SQL server on Forefront TMG 2010 firewalls or UAG 2010 servers! Using the Windows Update control panel application, select the option to install the latest service pack for Microsoft SQL Server 2008, which at the time of this writing is Service Pack 3. You can install the service pack directly if you choose; SQL Server 2008 Express SP3 can be downloaded here. After applying the latest service pack you can confirm that SQL has been updated by opening an elevated command prompt and entering the following commands:
osql -E -S .\msfw select @@version [press enter] go [press enter]
The output of the command should indicate that the installed SQL version is Microsoft SQL Server 2008 (SP3) – 10.0.5500.0 (X64).
Note: Applying service packs and updates to SQL is highly recommended to maintain the most secure Forefront TMG 2010 firewall possible. Upgrading the version of SQL installed on the TMG firewall is not supported and definitely not recommended, so don’t attempt to upgrade to SQL Server 2008 R2 Express.
Microsoft Security Bulletin MS11-083 and Forefront TMG 2010
Included in the November Microsoft security bulletin release was security update MS11-083 (KB2588516) that addresses a critical vulnerability in TCP/IP that could allow remote code execution. Forefront TMG 2010 firewalls are protected from this vulnerability, as the firewall engine’s kernel mode driver processes packets even before the operating system sees them. More information about how the Forefront TMG 2010 firewall engine and service work can be found here [this document is for ISA, but TMG is similar]. Although the underlying operating system’s TCP/IP networking stack is protected by the Forefront TMG firewall engine driver, TMG administrators are still strongly encouraged to install the MS11-083 update as soon as possible.