Archive
Forefront TMG 2010 Protocols and Ports Reference
When deploying Forefront TMG 2010 as a forward or reverse proxy, many organizations will place their TMG firewalls in a perimeter or DMZ network to provide an additional layer of protection for their proxies. When deployed in this manner, configuring perimeter firewalls to allow proper communication to and from the Forefront TMG firewall can be challenging. Although the Service Overview and Network Port Requirements for Windows document on TechNet includes information about ISA server (which also applies to TMG) it includes all protocols and ports used by TMG in all deployment scenarios. This can be confusing when you simply want to allow TMG firewalls in a perimeter network to communicate with an Enterprise Management Server (EMS) on the internal network, or simply manage a TMG firewall in a perimeter network from a management workstation on the internal network. Opening all of the ports listed in the Microsoft KB article mentioned above would be unnecessary and would violate the principle of least privilege, which dictates that only the specific ports required for communication should be opened.
Note: This reference covers typical TMG configurations and may not include all protocols and ports required for every deployment scenario. For example, if you are using RADIUS or RSA for authentication, have configured connectivity verifiers or a remote SQL server, or have deployed Forefront TMG 2010 for Exchange integration, each of these configurations will require additional perimeter firewall access. Also, don’t forget that your perimeter firewalls will need to allow access to the protocols and ports required for the services you are accessing/publishing through Forefront TMG 2010.
For reference, here are the protocols and ports required for specific, common Forefront TMG 2010 deployment scenarios:
EMS to TMG
TCP 135, 10000-65535* – RPC
TCP 3847 – MS Firewall Control
TMG to EMS
TCP 445 – CIFS
UDP 445 – CIFS
TCP 2171 – MS Firewall Storage (domain-joined only)
TCP 2172 – MS Firewall Storage Secure (workgroup mode only)
TCP 3847 – MS Firewall Control
TMG to DCs
Domain joined…
TCP 88 – Kerberos
UDP 88 – Kerberos (send receive)
UDP 123 – NTP
TCP 135, 49152-65535* – RPC
TCP 389 – LDAP
UDP 389 – LDAP
TCP 445 – CIFS
UDP 445 – CIFS
TCP 3268 – LDAP Global Catalog
Non domain-joined…
TCP 389 – LDAP (required only for pre-authentication in reverse proxy scenarios)
TCP 636 – LDAPS (required only for pre-authentication in reverse proxy scenarios)
TMG to DNS
TCP 53 – DNS (send receive)
UDP 53 – DNS
Primary EMS to Replica EMS
TCP 135, 49152-65535* – RPC
TCP 2173 – MS Firewall Storage Replication
Replica EMS to Primary EMS
TCP 135, 49152-65535* – RPC
TCP 445 – CIFS
UDP 445 – CIFS
TCP 2171 – MS Firewall Storage – domain-joined only
TCP 2172 – MS Firewall Storage (Secure) – workgroup mode only
TCP 3847 – MS Firewall Control
Web Proxy Client to TMG
TCP 80 – HTTP (WPAD only)
TCP 8080 – HTTP Proxy
Firewall Client to TMG
TCP 80 – HTTP (WPAD only)
TCP 1745 – Firewall Client Control Channel
UDP 1745 – Firewall Client Control Channel
TCP 1024-65535 – All high ports**
UDP 1024-65535 – All high ports**
Management Workstation to TMG
TCP 135, 10000-65535* – RPC
TCP 2171 – MS Firewall Storage – Domain mode only
TCP 2172 – MS Firewall Storage (Secure) – Workgroup mode only
TCP 3847 – MS Firewall Control
*The default dynamic port range for Windows Server 2008 R2 is 49152-65535. When TMG is installed this setting is changed to 10000-65535. This does not apply to TMG EMS, however. RPC can be configured to use a smaller range of dynamic ports, if necessary. For more information, please see Microsoft KB 154956.
**The Forefront TMG 2010 Firewall Client is designed to operate without a firewall between itself and the TMG firewall. It is highly recommended that you avoid this design whenever possible. If this is unavoidable, all TCP and UDP high ports will have to be opened, as the TMG Firewall Client control channel utilizes random high ports and cannot be restricted as RPC can.
Controlling Access to File Shares with Forefront TMG 2010
Consider a scenario in which you have an IIS server located in a perimeter network protected by Forefront TMG 2010. The server is published to the Internet and is used to display product information for your company. Web content developers on your internal network need to have access to file shares on the IIS server to upload new web content. To facilitate this access you create an access rule to allow CIFS access to the IIS server. For security reasons you decide to restrict access to members of the Web Content Developers domain group. In addition, your workstations have the Forefront TMG Firewall Client installed. The access rule looks like this:
When users attempt to map a drive to the file share on the web server they receive the following error message:
System error 67 has occurred. The network name cannot be found.
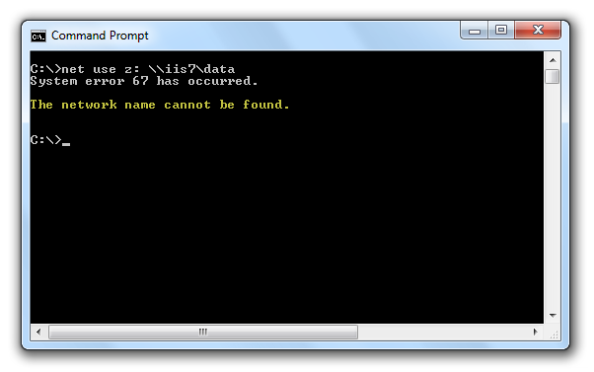
In addition, the Forefront TMG 2010 firewall log indicates the following:
Denied Connection Log Type: Firewall Service Status: The action cannot be performed because the session is not authenticated.

At this point you might be puzzled because you have the Forefront TMG Firewall Client is installed on the workstation. TMG Firewall Client communication is always authenticated, so why does the firewall log indicate otherwise? The answer is simple. The Forefront TMG 2010 Firewall Client is a Layered Service Provider (LSP) that listens for Winsock calls made by the operating system and applications. Any Winsock calls made for resources on a remote network will be transparently delivered to the proxy server by the Firewall Client. However, CIFS communication does not use Winsock, so the TMG Firewall Client does not handle this traffic. As such, the network requests are delivered to the Forefront TMG firewall as SecureNAT requests. Since the rule in question requires authentication, and SecureNAT traffic cannot be authenticated, the firewall appropriately denies the traffic and the request fails.
You can resolve this issue by removing authentication on the access rule and controlling access on the file share itself. If you want to enforce user and group authentication at the firewall, consider using another protocol such as FTP.
For more information about the Forefront TMG 2010 Firewall Client and CIFS connections, please review Microsoft Knowledge Base article 913782.
Fastvue Enhanced Reporting for Forefront TMG 2010
Recently I had the pleasure of reviewing the Fastvue Dashboard product for Forefront TMG 2010 at ISAserver.org. Fastvue is a real-time dashboard that integrates with Forefront TMG to provide a nearly instantaneous view of traffic being controlled by your TMG firewall. Although the real-time dashboard is a nice feature, if you’ve spent any time at all with Forefront TMG 2010’s native reporting tools you know that TMG is severely lacking in this area. A major limitation of Forefront TMG 2010’s in-box reporting is that the reports are generated using summarized data. Data summarization occurs only once daily, so reports can be lacking essential information if you are looking for recent activity. In addition, the native reports are static and one-dimensional. If a report reveals something interesting that you want to know more about, creating and generating a new report is required.
Thankfully the good folks at Fastvue recognized these shortcomings and have addressed many of these issues with their latest release. Fastvue v2.0 now includes full historical reporting capabilities, with detailed company overview and user investigation reports that can be shared via e-mail. Reports can also be scheduled to run automatically. The reports are highly interactive, allowing the administrator to dynamically drill down to generate more granular reports in an instant.
The current version of Fastvue is priced at $395.00 per TMG firewall. The newest version will be priced at $795.00 per server. However, for a limited time, readers of my blog can purchase Fastvue v1.0 for the current price and receive a free upgrade to v2.0 when it is released. Click here to download a trial of the software and to take advantage of this offer!
WPAD Considerations for Kerberos Authentication with NLB VIP on Forefront TMG 2010
As I outlined in a recent article on ISAserver.org, Service Pack 2 (SP2) for Forefront TMG 2010 supports Kerberos authentication in load-balanced scenarios when web proxy clients are configured to use the virtual IP address (VIP) of the array. However, using Web Proxy Automatic Discovery (WPAD) with either DNS or DHCP poses a challenge for organizations that choose to take advantage of this new feature. When using WPAD, the web proxy client retrieves the automatic configuration script from the Forefront TMG firewall. The script provides the web proxy client with the IP addresses (or hostnames, if configured) of the individual array members. In this configuration, the web proxy client will send its request to one of the array members returned by function MakeProxies() and not to the VIP, as desired.
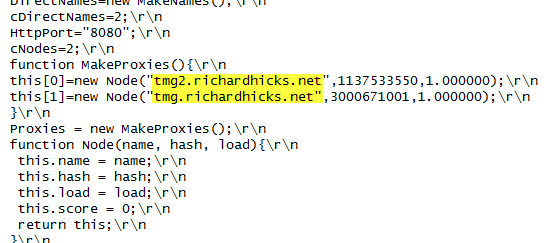
To work around this issue you can configure a separate web server to host the automatic configuration script. You can use any web server you wish, just make sure that it is highly available and don’t forget to configure the MIME type application/x-ns-proxy-autoconfig for the file extension you choose (typically .DAT or .PAC). Full details about how to do this can be found here. You can create your own Proxy Automatic Configuration (PAC) file from scratch, or you can simply retrieve the automatic configuration script from TMG, modify it to use the IP address (or preferably the hostname or FQDN) of the Forefront TMG array’s VIP, and place that on the web server for clients to retrieve. This means that the automatic configuration script will have to be updated manually, as required. This could be automated by writing a script that periodically retrieves the automatic configuration script from the Forefront TMG firewall, modifies it appropriately, and then saves it on the web server if you were really clever! Another alternative is to configure the Forefront TMG 2010 firewall to return a customized automatic configuration script. You can find details about this configuration here.
Error 0xc0040431 When Creating a Forefront TMG 2010 Enterprise Array
When attempting to join a Forefront TMG 2010 enterprise edition firewall to an Enterprise Management Server (EMS) managed array, you may encounter one of the following error messages:
The operation failed. Error: 0xc0040431 Forefront TMG Services failed to start after array join or an array disjoin. Check alerts, fix the configuration, and attempt to restart the services.

The operation failed. Error: 0xc0040410 The file cannot be imported because the enterprise management mode is 2010SP1 in the exported file and 2008-only in the stored configuration.

You may also encounter one of the following error messages when attempting to create a standalone array with two or more Forefront TMG 2010 enterprise edition firewalls:
The operation failed. Error: 0x80004002 No such interface supported

The operation failed. Error: 0xc0040410 The file cannot be imported because the enterprise management mode is in the exported file and in the stored configuration.

Any of these errors can occur when you attempt to join a pre-SP2 Forefront TMG 2010 firewall to an EMS-managed array running Forefront TMG SP2, or when you attempt to create a standalone array with one node running Forefront TMG SP2 and another node running SP1.
To resolve this issue, make certain that Forefront TMG 2010 firewalls are all at the same service pack and update level before joining an EMS-managed array or creating a standalone array. For information about determining which version of ISA or TMG is installed, refer to one of the following blog posts:
https://tmgblog.richardhicks.com/2010/10/11/how-to-determine-tmg-version/
https://tmgblog.richardhicks.com/2010/12/03/more-about-determining-tmg-version-numbers/
For a documented reference of ISA and TMG build numbers, click here.
Forefront TMG 2010 Configuration Change Description Survey
When making changes to the Forefront TMG 2010 firewall, by default the administrator is prompted to enter a description of the configuration changes made before they are applied. For those TMG administrators that use this facility, what kind of information do you put in this change description box? A verbose explanation of changes made? Details about why the change was made? Your name, network ID, or initials? Is it helpful to provide reference to a help desk ticket or a change request?
Tell me how you use this feature and what kind of information you typically provide by commenting on this post. I’ll approve the most interesting and useful ones as they come in. Thanks in advance for participating!

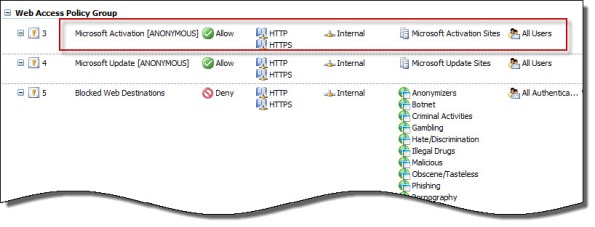
Error 0x8004FE2F Activating Windows on Forefront TMG 2010 Protected Network
When attempting to activate Windows Server 2008R2 you may receive one of the following error messages:
A problem occurred when Windows tried to activate. Error Code 0x8004FE2F

Or…
A problem occurred when Windows tried to activate. Error Code 0xC004FC03

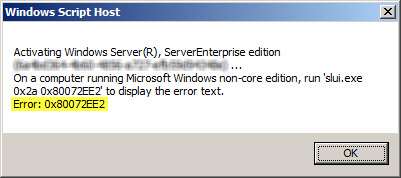
If you attempt to activate Windows from the command line using slmgr.vbs -ato you may also encounter one of the following error messages:
Activating Window Server(R), ServerEnterprise edition {GUID}...
On a computer running Microsoft Windows non-core edition, run 'slui.exe
0x2a 0x8004FE2F' to display the error text.
Error: 0x8004FE2F

Or…
Activating Window Server(R), ServerEnterprise edition {GUID}...
On a computer running Microsoft Windows non-core edition, run 'slui.exe
0x2a 0x80072EE2' to display the error text.
Error: 0x80072EE2
The problem may occur for systems that are located on a network that is protected by a Forefront TMG 2010 firewall, and the access rule that allows the traffic requires authentication. The Windows activation process relies on WinHTTP and by default, WinHTTP communication is sent as SecureNAT client traffic. SecureNAT clients unfortunately cannot be authenticated, so the request fails.
There are two ways resolve this issue. The first is to configure WinHTTP on the Windows system you are trying to activate to use a proxy serverexplicitly. Open an elevated command prompt and enter the following command:
netsh winhttp set proxy <name or IP address of proxy server>:<port>
For example:
netsh winhttp set proxy tmg.richardhicks.net:8080
Instead of making this change to each system you want to activate, an alternative is to create an anonymous access rule on the Forefront TMG 2010 firewall that allows HTTP and HTTPS traffic to those destinations required to activate Windows. Using the Forefront TMG 2010 management console, create an access rule that allows HTTP and HTTPS from the Internal network to a Domain Name Set that contains the following destinations for all users:
activation.sls.microsoft.com.nsatc.net go.microsoft.com *.sls.microsoft.com
Make sure this rule is placed before any other rules for HTTP or HTTPS that require authentication.
Once configured, activating Windows should work without issue.