Archive
Southern California IT Professionals Association September Meeting
On Thursday, September 8 2011, I will be presenting an overview of Microsoft Forefront edge security solutions at the Southern California IT Professionals Association monthly meeting. During the session I’ll be providing an overview of Forefront Threat Management Gateway (TMG) 2010 and Unified Access Gateway (UAG) 2010, discussing common deployment scenarios, and highlighting the similarities and differences of the two solutions.
I will also be giving away copies of the Forefront Threat Management Gateway (TMG) 2010 Administrator’s Companion and the Forefront Unified Access Gateway (UAG) 2010 Administrator’s Handbook. The event begins at 6:30PM PDT and will be held at the CSU Fullerton campus in Irvine. For more information and to RSVP for the event, click here.
Hope to see you there!
HTTP to HTTPS Redirection Options in Forefront TMG and UAG
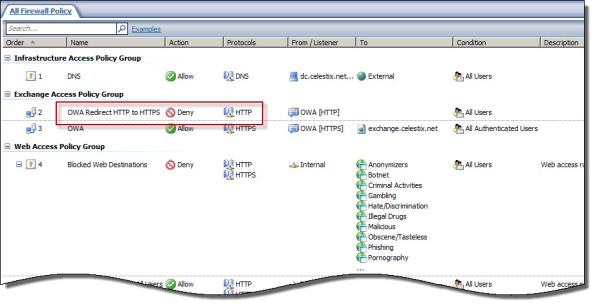
When publishing SSL-protected web sites such as Microsoft Outlook Web App with Forefront Threat Management Gateway (TMG) 2010 or Unified Access Gateway (UAG) 2010, it is often desirable to allow clients to enter the URL of the site without specifying the HTTPS protocol explicitly. For example, when publishing Outlook Web App (OWA) 2010 where the full URL is https://mail.celestix.net/owa/, for convenience an administrator might want to redirect non-secure requests for http://mail.celestix.net/owa/ to use the secure HTTPS protocol automatically. This can be done in a number of ways, depending on which Forefront solution is used for publishing.
Forefront TMG
With TMG, HTTPS redirection can be enabled by opening the properties of the web listener used in the publishing rule and selecting Enable HTTPS connections on port: and Redirect authenticated traffic from HTTP to HTTPS.
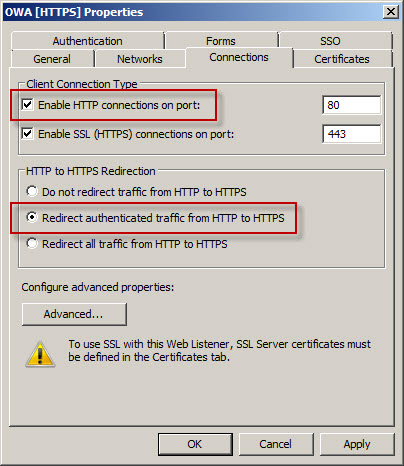
Now when users request the non-secure http://mail.celestix.net/owa/ they will automatically be redirected to the secure https://mail.celestix.net/owa/.
Even more convenient is to redirect requests for the base URL http://mail.celestix.net/ to the correct path https://mail.celestix.net/owa/. The easiest way to accomplish this is to create a new publishing rule that denies requests to http://mail.celestix.net/ and redirects them to https://mail.celestix.net/owa/. To enable this functionality, use the Web Site Publishing Wizard to create a publishing rule that denies access to http://mail.celesitx.net/ and redirects those requests to https://mail.celestix.net/owa/.

Be sure to place this rule before the publishing rule allowing access to the SSL-protected web site.
Now when users request the non-secure http://mail.celestix.net/ they will automatically be redirected to the secure https://mail.celestix.net/owa/.
Forefront UAG
Configuring Forefront UAG to redirect HTTP to HTTPS is even simpler. After you’ve created a trunk and published OWA, right-click HTTP Connections in the UAG management console navigation tree, select New Trunk, and then select the HTTP to HTTPS redirection option.

A Word about Network Interface Port Speed and Duplex Settings
When configuring network interface settings on a Forefront Threat Management Gateway (TMG) 2010 firewall, I strongly recommend that the port speed and duplex settings on all active network interfaces be manually configured. Although autonegotiation is typically enabled by default, and in most cases works without issue, I prefer to eliminate any possibility that a slower link speed or incorrect duplex setting is negotiated in error by configuring these settings explicitly.
Some believe you can configure one side of a link (either the host or the switch) manually and leave the other side set to autonegotiate. The theory is that the host set to autonegotiate will determine what settings the other side has configured and automatically choose those. This is not completely true and doesn’t work as expected. When one side of a link is set for autonegotiation and the other side is not (or doesn’t support it), a process called parallel detection takes place whereby the device that is configured to autonegotiate can determine the port speed of the other device, but it cannot determine the duplex settings and defaults to half duplex. Often this results in a duplex mismatch, which will cause extremely poor performance.
So, when configuring port speed and duplex settings, always remember that BOTH sides of the link should be configured identically. That is, if the switch is configured for 100Mbps/full duplex operation, the network interface on the TMG firewall should be configured the same. On some systems (mostly older ones), when attempting to change these settings, you might notice that there is no option to enable 1000Mbps (gigabit) at full duplex operation. The only available option is autonegotiate 1000Mbps.

Why is there no option to select 1000Mbps and full duplex? Because the designers of the 1000BASE-T specification (IEEE 802.3ab) made duplex autonegotiation mandatory when operating at 1000Mbps port speed over copper cabling. For this reason some network interface management software may limit your choices and not allow you to select this option. In my experience it appears that adherence to this mandate has been relaxed as most newer systems I have worked with now give you the option of configuring 1000Mbps and full duplex operation with copper cabling. If you have an older system and don’t have the option to specify 1000Mbps/full duplex on the network interface, I would recommend updating your network interface device drivers. If you still don’t have the option to specify 1000Mbps/full duplex you may need to replace the network interface card itself.
Mail and OCS Server Publishing using TMG on Forefront Unified Access Gateway (UAG) 2010
In a recent post I outlined some of the basic differences between Forefront Threat Management Gateway (TMG) 2010 and Unified Access Gateway (UAG) 2010. Although I indicated that UAG includes TMG under the covers, TMG is intended to provide protection for the UAG host only. It cannot be used to provide firewall, outbound proxy, or VPN services. There are specific instances when leveraging the underlying TMG services is allowed and supported. As the UAG Support Boundaries indicate, you can use TMG on UAG for Exchange mail server publishing (SMTP/SMPTS, POP3/POP3S, and IMAP/IMAPS) and Office Communications Server (OCS) SIP traffic publishing (Communicator Web Access (CWA) should be published using UAG). This means that if you are planning to publish Exchange and OCS, you can accomplish this using UAG alone. You are not required to deploy TMG or another firewall to provide secure access to mail server-to-server communication or OCS SIP traffic.
What are the Differences between TMG and UAG?
I am frequently asked “What are the differences between TMG and UAG?” and “Which one should I deploy?” In this post I will provide some background information that will hopefully answer those questions for you. This is not intended to be a comprehensive side-by-side feature comparison. It is only meant to provide a high-level overview of the basic differences between TMG and UAG.
Let’s begin by examining the features of each product:
- Microsoft Forefront Threat Management Gateway (TMG) 2010 is an integrated edge security gateway. It is a Common Criteria certified (EAL4+) enterprise-class application layer firewall that includes support for proxy services (forward and reverse proxy), content caching, and VPN (both remote access and site-to-site). It can be deployed in all of these roles, or any subset of them.
- Microsoft Forefront Unified Access Gateway (UAG) 2010 is a dedicated remote access gateway. It is Common Criteria certified (EAL2+) and provides browser-based remote access to published applications via an SSL VPN portal. It includes limited support for traditional client access VPN with Secure Socket Tunneling Protocol (SSTP) and Network Connector (a proprietary UAG component that provides network-level access). UAG can also serve as a DirectAccess gateway, a deployment scenario for which the UAG provides incredible value.
Fundamentally, TMG is a network-centric access control solution. With it you can provide fine-grained control over all types of communication going through the firewall, both web-based and non web-based protocols. TMG controls access inbound and outbound, and allows for the configuration of multiple perimeter (DMZ) networks.
By contrast, UAG is an application-centric remote access solution. It provides inbound access only; there are no outbound access capabilities provided by UAG. This is a common source of confusion, as UAG includes TMG under the hood. Many administrators mistakenly believe they can leverage the underlying TMG installation to provide forward proxy or VPN services. This is not supported. Other than mail server publishing, TMG may not be used for any other purpose. It is installed to provide protection for the UAG application only.
UAG takes one of the TMG deployment roles, the VPN/remote access role, and supercharges it. UAG includes advanced application publishing capabilities not provided by TMG, such as endpoint configuration and health detection, customizable data manipulation, session clean up, and more. For example, an administrator can allow full access to a published application to any system that has anti-virus software running and up-to-date, has the firewall enabled, and has the latest system updates applied. If the system does not meet these requirements, the administrator can determine if access should be granted with reduced privileges, or perhaps denied access altogether. An administrator might mask specific data sent to a user (such as credit card numbers, social security numbers, etc.) if the user is accessing the published web application from an untrusted device (non-managed workstation, kiosk, etc.). When the user closes their session, all temporarily downloaded files are removed from the workstation, ensuring that no sensitive data is left behind.
So when do you deploy TMG and when do you deploy UAG? If you want to control outbound web access (forward proxy or firewall), TMG is your only option. If you want to publish multiple applications with a single URL (an application portal), UAG is the answer. There are, however, areas where there is overlap between TMG and UAG capabilities. For example, let’s say you want to publish a single application such as Outlook Web App (OWA). Which solution do you choose? TMG can publish OWA quite capably, as can UAG. The answer depends on your specific requirements. If you need to restrict access to only those systems that meet your specific configuration requirements, publishing OWA with UAG is the solution. If you wish to grant access to OWA to anyone who authenticates successfully, then TMG will suffice.
Licensing often plays a role in determining which solution to deploy for remote access. UAG is licensed using Client Access Licenses, or CALs. Each user of the system is required to have a UAG CAL. The UAG CAL is included in the Microsoft Enterprise CAL (eCAL), so this may not be an issue for larger enterprises. TMG is licensed per processor. There are no CALs required for users of TMG (advanced web protection features do require the Web Protection Services Subscription license, however, which is licensed per user or per device annually). For more information, refer to the licensing FAQs for TMG and UAG.
In summary, TMG is a rock-solid firewall, proxy, content cache, and VPN access gateway that has basic support for application publishing. UAG is an advanced remote access gateway dedicated to application publishing, and is highly customizable and limited in functionality only by your programming skills, creativity, and imagination.
In a nutshell, think of TMG and UAG like this:
TMG – Keeps the bad guys out.
UAG – Lets the good guys in.
Upcoming Events
Over the next few months I’ll be traveling and speaking frequently, giving presentations at conferences, delivering training classes, speaking at seminars, and more. I’ve created an Events page here to keep everyone informed about where I am and what I’m doing. Chances are good that I’ll be in your part of the world sometime this year or next, so register for one of the events and introduce yourself!
Forefront Threat Management Gateway (TMG) and Windows Server 2008 Networking Scalability Features
Several years ago, Microsoft released the Scalable Networking Pack (SNP) for Windows Server 2003 SP1. The SNP included enhancements to the operating system’s networking stack to improve scalability and increase performance. Later the SNP features were included in Windows Server 2003 SP2. Veteran ISA firewall administrators will recall that the SNP adversely affected the operation of ISA, particularly when Network Load Balancing (NLB) was enabled. Since these features were enabled by default, disabling them after installing the SNP or Windows Server 2003 SP2 on an ISA firewall was a requirement. This was accomplished by modifying registry keys or installing a hotfix that disabled the SNP features.
Today, the networking stack in Windows Server 2008 and Windows Server 2008 R2 both include the capabilities originally introduced with the SNP. Instead of modifying registry keys to enable/disable those features as we did in Windows Server 2003, they are now managed using netsh.exe. To view these parameters, enter the following command:
netsh interface tcp show global
As you can see, SNP components such as receive-side scaling, chimney offload, and NetDMA are enabled by default. Thankfully TMG is now fully compatible with all of the scalable networking features. There is no need to disable them unless you have a specific requirement to do so.
Microsoft Forefront Unified Access Gateway (UAG) Administrator’s Handbook – Pre-Order Now!
Great news! The Microsoft Forefront Unified Access Gateway (UAG) 2010 Administrator’s Handbook is now available for pre-order. Authored by Erez (Ben) Ben-Ari and Ran Dolev from Microsoft, this book will be a valuable asset for all UAG administrators. Due out early next year, the book is available in traditional print form or electronic book (eBook). You can purchase one or both, but if you buy the eBook you will have immediate access to the first three chapters, and additional chapters as they become available.
Microsoft Operations Framework (MOF) Reliability Workbooks
The Microsoft Operations Framework (MOF) provides important guidance for IT professionals responsible for maintaining and operating various Microsoft technologies. The MOF Technology Library includes a series of workbooks that provide detailed knowledge, tasks, and schedules required to keep these technologies operating efficiently and without issue. There are workbooks available today for many Microsoft infrastructure and application services, including Active Directory, DNS, Exchange, SQL, IIS, and many more. Reliability workbooks for Forefront Unified Access Gateway (UAG) and DirectAccess were recently added to the library. The Network Load Balancing (NLB) workbook will also be helpful for many TMG and UAG administrators. If you are responsible for deploying or managing these technologies in your organization, these workbooks are sure to be beneficial.