Archive
Fastvue Enhanced Reporting for Forefront TMG 2010
Recently I had the pleasure of reviewing the Fastvue Dashboard product for Forefront TMG 2010 at ISAserver.org. Fastvue is a real-time dashboard that integrates with Forefront TMG to provide a nearly instantaneous view of traffic being controlled by your TMG firewall. Although the real-time dashboard is a nice feature, if you’ve spent any time at all with Forefront TMG 2010’s native reporting tools you know that TMG is severely lacking in this area. A major limitation of Forefront TMG 2010’s in-box reporting is that the reports are generated using summarized data. Data summarization occurs only once daily, so reports can be lacking essential information if you are looking for recent activity. In addition, the native reports are static and one-dimensional. If a report reveals something interesting that you want to know more about, creating and generating a new report is required.
Thankfully the good folks at Fastvue recognized these shortcomings and have addressed many of these issues with their latest release. Fastvue v2.0 now includes full historical reporting capabilities, with detailed company overview and user investigation reports that can be shared via e-mail. Reports can also be scheduled to run automatically. The reports are highly interactive, allowing the administrator to dynamically drill down to generate more granular reports in an instant.
The current version of Fastvue is priced at $395.00 per TMG firewall. The newest version will be priced at $795.00 per server. However, for a limited time, readers of my blog can purchase Fastvue v1.0 for the current price and receive a free upgrade to v2.0 when it is released. Click here to download a trial of the software and to take advantage of this offer!
WPAD Considerations for Kerberos Authentication with NLB VIP on Forefront TMG 2010
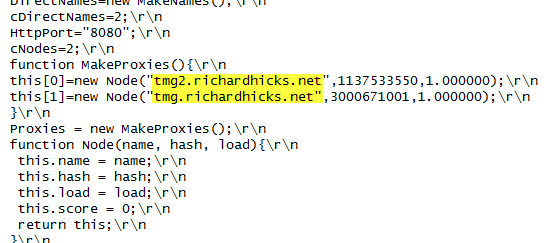
As I outlined in a recent article on ISAserver.org, Service Pack 2 (SP2) for Forefront TMG 2010 supports Kerberos authentication in load-balanced scenarios when web proxy clients are configured to use the virtual IP address (VIP) of the array. However, using Web Proxy Automatic Discovery (WPAD) with either DNS or DHCP poses a challenge for organizations that choose to take advantage of this new feature. When using WPAD, the web proxy client retrieves the automatic configuration script from the Forefront TMG firewall. The script provides the web proxy client with the IP addresses (or hostnames, if configured) of the individual array members. In this configuration, the web proxy client will send its request to one of the array members returned by function MakeProxies() and not to the VIP, as desired.
To work around this issue you can configure a separate web server to host the automatic configuration script. You can use any web server you wish, just make sure that it is highly available and don’t forget to configure the MIME type application/x-ns-proxy-autoconfig for the file extension you choose (typically .DAT or .PAC). Full details about how to do this can be found here. You can create your own Proxy Automatic Configuration (PAC) file from scratch, or you can simply retrieve the automatic configuration script from TMG, modify it to use the IP address (or preferably the hostname or FQDN) of the Forefront TMG array’s VIP, and place that on the web server for clients to retrieve. This means that the automatic configuration script will have to be updated manually, as required. This could be automated by writing a script that periodically retrieves the automatic configuration script from the Forefront TMG firewall, modifies it appropriately, and then saves it on the web server if you were really clever! Another alternative is to configure the Forefront TMG 2010 firewall to return a customized automatic configuration script. You can find details about this configuration here.
ESET Gateway Security Beta for Forefront TMG 2010
For security administrators looking to improve upon Forefront TMG 2010’s already strong advanced web protection features, leading anti-virus vendor ESET recently announced the beta availability of its Gateway Security for Forefront TMG 2010 software. ESET Gateway Security for Forefront TMG delivers advanced, gateway-integrated virus and malicious software scanning to provide comprehensive protection for web-based protocols like HTTP and FTP. ESET Gateway Security for Forefront TMG also supports SMTP, IMAP, and POP3 protocols to provide anti-malware and anti-spam capabilities for added protection. In addition, ESET Gateway Security for Forefront TMG 2010 includes host-based security for the TMG firewall’s underlying operating system, as well as automatic file exclusion configuration to ensure compatibility with Forefront TMG. ESET Gateway Security for Forefront TMG 2010 is fully compatible with existing ESET centralized management tools and supports Microsoft ISA Server 2006. Download the beta today!
Configuring SQL Memory Limits on Forefront TMG 2010
When Forefront TMG 2010 is installed, an instance of SQL Server 2008 Express is also installed to facilitate local firewall and web proxy logging. Some TMG administrators have reported that the SQL server process (sqlservr.exe) may consume an excessive amount of memory.
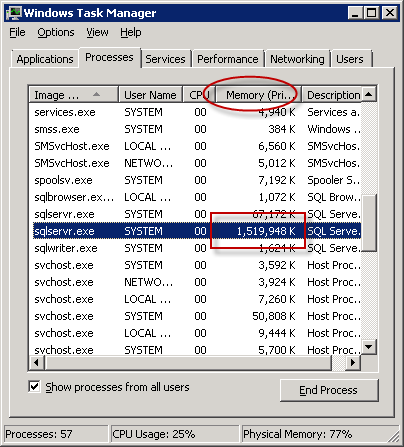
This occurs because SQL server performs its own internal memory management. By design it will consume large amounts of memory and hold it in reserve, which may appear to be a memory leak. However, if you observe the memory consumed by SQL server over an extended period of time, you will notice that it will periodically release memory as well.
In most cases, allowing SQL to handle the job of managing its memory without restriction poses no real problem. However, if your system is exhibiting signs of high memory pressure and you are confident that there are no other processes that are consuming excessive amounts of memory, you can configure SQL to limit the amount of memory that it will reserve. Before manually configuring SQL memory limits, review this blog post for a list of recommended settings.
Next, open an elevated command prompt and enter the following command:
osql –E –S .\msfw
After connecting to the SQL instance, enter the following commands:
USE master GO EXEC sp_configure 'show advanced options', 1 RECONFIGURE WITH OVERRIDE GO EXEC sp_configure 'max server memory (MB)', 1024 --configure 1GB limit, adjust as needed GO EXEC sp_configure 'show advanced options', 0 RECONFIGURE WITH OVERRIDE GO
This script assumes that you’ve chosen a 1GB (1024MB) memory limit. You can adjust the script above to reflect the values for your environment as required. Once complete, restart the SQL server service for the changes to take effect.
To view the currently configured memory limit, simply omit the numeric value after max server memory (MB), as shown here:
EXEC sp_configure 'max server memory (MB)'
To make things easier you can download these as script files and execute them using the following command:
osql –E –S .\msfw -i <path to script file>
You can find script files to show and set SQL memory limits here:
Hotfix Rollup 1 for Forefront TM 2010 SP2 Now Available
A hotfix rollup for Forefront TMG 2010 SP2 is now available. The hotfix rollup resolves several reported issues with TMG, including:
KB2654016 – A client may be unsuccessful in accessing a Java SSO application published to the web by Forefront TMG 2010
KB2653703 – “Error: Subreport could not be shown” error message in the User Activity or Site Activity report in Forefront TMG 2010
KB2654585 – UDP packets may become backlogged when you increase the “maximum concurrent UDP sessions per IP address” setting in Forefront TMG 2010
KB2624178 – Forefront TMG 2010 administrators may be unable to generate reports
KB2636183 – Both sides of a TCP connection are closed when the client or remote application half-closes the TCP connection in Forefront TMG 2010
KB2653669 – Summary information for the Top Overridden URLs table and for the Top Rule Override Users table display incorrect information in Forefront TMG 2010
KB2617060 – Forefront TMG 2010 enables L2TP site-to-site connections in RRAS
KB2655951 – Japanese characters in the subject line of an Alert email message are not readable in the Japanese version of Forefront TMG 2010
KB2654068 – “The Web Listener is not configured to use SSL” warning message may occur when you configure a Web Listener to use a valid SSL certificate in Forefront TMG 2010
KB2654193 – You receive a “Bad Request” error message when you try to access Outlook Web App published by Forefront TMG 2010
KB2654074 – String comparison may become case-sensitive when you published a website using Forefront TMG 2010
KB2658903 – Forefront TMG 2010 firewall service (wspsrv.exe) may crash frequently for a published website secured by SSL after you install Service Pack 2.
Hotfix rollup 1 for Forefront TMG 2010 SP2 can be downloaded here. After applying this update, the new Forefront TMG 2010 build number will be 7.0.9193.515.
TrainSignal Forefront TMG 2010 Training
Are you looking for Forefront TMG 2010 training? If so, take a look at TrainSignal’s Forefront TMG 2010 training package. This is a comprehensive video training course that includes 8 hours of video instruction over 21 modules. Scott Lowe does an excellent job of delivering the course, which is available online and on disc. I had the privilege of serving as the technical reviewer for this video training series, so I can assure you the material is exceptional.
If you are planning to deploy Forefront TMG 2010 in the future, or perhaps you are considering a migration from previous versions of ISA server to Forefront TMG 2010, the TrainSignal Forefront TMG 2010 video training series is an excellent investment. Check it out now!
Error 0xc0040431 When Creating a Forefront TMG 2010 Enterprise Array
When attempting to join a Forefront TMG 2010 enterprise edition firewall to an Enterprise Management Server (EMS) managed array, you may encounter one of the following error messages:
The operation failed. Error: 0xc0040431 Forefront TMG Services failed to start after array join or an array disjoin. Check alerts, fix the configuration, and attempt to restart the services.

The operation failed. Error: 0xc0040410 The file cannot be imported because the enterprise management mode is 2010SP1 in the exported file and 2008-only in the stored configuration.

You may also encounter one of the following error messages when attempting to create a standalone array with two or more Forefront TMG 2010 enterprise edition firewalls:
The operation failed. Error: 0x80004002 No such interface supported

The operation failed. Error: 0xc0040410 The file cannot be imported because the enterprise management mode is in the exported file and in the stored configuration.

Any of these errors can occur when you attempt to join a pre-SP2 Forefront TMG 2010 firewall to an EMS-managed array running Forefront TMG SP2, or when you attempt to create a standalone array with one node running Forefront TMG SP2 and another node running SP1.
To resolve this issue, make certain that Forefront TMG 2010 firewalls are all at the same service pack and update level before joining an EMS-managed array or creating a standalone array. For information about determining which version of ISA or TMG is installed, refer to one of the following blog posts:
https://tmgblog.richardhicks.com/2010/10/11/how-to-determine-tmg-version/
https://tmgblog.richardhicks.com/2010/12/03/more-about-determining-tmg-version-numbers/
For a documented reference of ISA and TMG build numbers, click here.
Forefront TMG 2010 Configuration Change Description Survey
When making changes to the Forefront TMG 2010 firewall, by default the administrator is prompted to enter a description of the configuration changes made before they are applied. For those TMG administrators that use this facility, what kind of information do you put in this change description box? A verbose explanation of changes made? Details about why the change was made? Your name, network ID, or initials? Is it helpful to provide reference to a help desk ticket or a change request?
Tell me how you use this feature and what kind of information you typically provide by commenting on this post. I’ll approve the most interesting and useful ones as they come in. Thanks in advance for participating!

Unable to Retrieve Data from Array Members after Enabling Kerberos Authentication with NLB on Forefront TMG 2010
Immediately after configuring Forefront TMG 2010 to support Kerberos authentication with NLB, you may encounter a scenario where the Forefront TMG management console fails to communicate with the members of the array and includes the following error message:
Unable to retrieve data from: <array_members>

In addition, an Event ID 4 from the Security-Kerberos source is recorded in the system event log:
The Kerberos client received a KRB_AP_ERR_MODIFIED error from the server tmgsvc2. The target name used was tmg3$@richardhicks.net. This indicates that the target server failed to decrypt the ticket provided by the client. This can occur when the target server principal name (SPN) is registered on an account other than the account the target service is using. Please ensure that the target SPN is registered on, and only registered on, the account used by the server. This error can also happen when the target service is using a different password for the target service account than what the Kerberos Key Distribution Center (KDC) has for the target service account. Please ensure that the service on the server and the KDC are both updated to use the current password. If the server name is not fully qualified, and the target domain (RICHARDHICKS.NET) is different from the client domain (RICHARDHICKS.NET), check if there are identically named server accounts in these two domains, or use the fully-qualified name to identify the server.
When making the changes to support Kerberos authentication in load balanced scenarios, the Forefront TMG firewall service is configured to run in the context of a domain user account. When the Forefront TMG management console was first opened, it authenticated to the array members using the Service Principal Name (SPN) registered to the machine (computer) account. As the changes are applied and the services are restarted, the array members are now running in the context of a domain user account. However, the management console continues to send a Kerberos ticket with the SPN registered to the machine account. The Forefront TMG firewall service running in the context of the domain user account cannot decrypt this Kerberos ticket and replies with a Kerberos error.

Resolution in this case is quite simple. Closing the Forefront TMG management console and opening it again will force the client to re-authenticate, this time using the correct SPN. The Kerberos event log errors are anomalous and can safely be ignored.










