Archive
IP Spoofing Alert from APIPA Address in Forefront TMG 2010
Security administrators may encounter the following IP spoofing alert on their Forefront TMG 2010 firewall:
Alert: IP Spoofing Description: Forefront TMG 2010 detected a possible spoof attack from the IP address 169.254.x.x. A spoof attack occurs when an IP address that is not reachable through the network adapter on which the packet was received. If logging for dropped packets is enabled, you can view the details of this attack in the firewall log in Forefront TMG 2010 log viewer. If the IP address belongs to a VPN client, this event may be ignored.

This alert occurs because the Forefront TMG 2010 firewall received a packet on its internal network interface from a client (server, workstation, or other host) that did not have a statically assigned IP address and was not able to obtain one from DHCP, so the client selected an IP address from the Automatic Private IP Address Assignment (APIPA) address range defined in RFC 3927.
You can safely ignore this alert, or you can resolve the issue by adding the APIPA reserved network 169.254.0.0/16 to the Internal network definition. This can be accomplished by opening the Forefront TMG 2010 management console and highlighting the Networking node in the navigation tree, then right-clicking the Internal network, selecting the Addresses tab, then clicking the Add Private button and choosing the address range 169.254.0.0 – 169.254.255.255.

Note: It is possible to resolve this issue by disabling alerts for IP spoofing attempts. However, this is considered bad security practice and is strongly discouraged.
You may recall from an earlier blog post I indicated that the best way to configure the Internal network definition in Forefront TMG 2010 is to choose the Add Adapter option. This still remains true. However, this is one of those rare cases in which you’ll want add an additional network address space to your Internal network definition to reduce the volume of IP spoofing alerts being raised by the Forefront TMG 2010 firewall.
The one side effect to implementing this change is that you will now receive a Configuration error alert informing you that your Internal network does not correlate with the network adapters that belong to it.
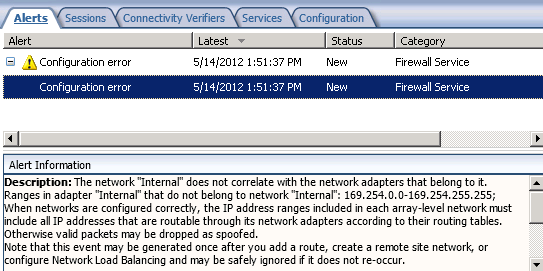
Essentially you have traded one annoying alert for another. However, the noise generated by IP spoofing alerts from clients with APIPA IP addresses might make this tradeoff worthwhile. In addition, it is much safer to disable the configuration error alert than it is the IP spoofing alert.




