Archive
Microsoft Reputation Services (MRS) Offline after December 31, 2015
 As I recently mentioned, Microsoft has discontinued and will be terminating their Microsoft Reputation Services (MRS) cloud URL categorization service on or shortly after December 31, 2015. Today, Microsoft released additional information vital to TMG administrators everywhere who are still relying on this service for URL filtering. Specifically, what happens with TMG once Microsoft officially turns off MRS and it is no longer available?
As I recently mentioned, Microsoft has discontinued and will be terminating their Microsoft Reputation Services (MRS) cloud URL categorization service on or shortly after December 31, 2015. Today, Microsoft released additional information vital to TMG administrators everywhere who are still relying on this service for URL filtering. Specifically, what happens with TMG once Microsoft officially turns off MRS and it is no longer available?
Bad things.
First, any firewall rules that rely on URL categorization to allow traffic will fail closed. That is, they will block all traffic. Second, any rules using URL categorization to deny traffic will fail open and allow that traffic instead. Finally, there is potential performance degradation that may occur with TMG after the service is disabled by Microsoft.
What to do?
First, update any TMG firewall rules that use URL Categories or URL Category Sets. You can replace them with Domain Name Sets or URL Sets, if desired. Next, disable the use of URL filtering in TMG by opening the TMG management console, right-clicking Web Access Policy and choosing Configure and then URL Filtering. Uncheck the box next to Enable URL Filtering and then click Ok.

Finally, consider a replacement solution for TMG’s URL filtering. There are a number of solutions available, both on-premises and cloud-based, that are capable replacements. The Zscaler solution is highly effective, and if you’re looking for a low-buck alternative, consider something like OpenDNS. There are many more, I’m sure.
Good luck!
Using PowerShell to Determine Forefront TMG Build Number
 Identifying the current build number of your Forefront TMG 2010 installation is critically important when making changes or updates to the system. It is generally recommended that all TMG firewalls be on the same release, so having this information is essential. Many TMG administrators use the TMG management console to gather this information, but I can tell you based on experience that this is not always the most accurate method to use.
Identifying the current build number of your Forefront TMG 2010 installation is critically important when making changes or updates to the system. It is generally recommended that all TMG firewalls be on the same release, so having this information is essential. Many TMG administrators use the TMG management console to gather this information, but I can tell you based on experience that this is not always the most accurate method to use.
I much prefer to gather this information programmatically at the command line. In the past I’ve written about using VBScript to do this, but it’s almost 2016 now and we really should be using PowerShell whenever possible. To that end, here are a few lines of PowerShell code you can use to accurately determine which version and build number your TMG firewall is currently running.
$FPC = New-Object -ComObject FPC.Root $Server = $FPC.GetContainingServer() $Server.ProductVersion

If you’ve done any work at all with VBScript and the TMG’s FPC COM object, you’ll no doubt be able to convert some of your existing scripts to PowerShell. Also, PowerShell, with its tab auto completion, is much more discoverable than using VBScript with COM, so I’m sure you’ll be able to do a lot more with TMG using PowerShell.
Enjoy!
Reminder: Microsoft Reputation Services (MRS) End of Support
 As a reminder to anyone out there still using the URL filtering feature of their Forefront TMG 2010 firewall, the Microsoft Reputation Services (MRS) service, which provides URL categorization for TMG, will no longer be supported after December 31, 2015. After this date, Microsoft will cease updating their URL categorization database. In addition, there are no guarantees from Microsoft that the service will be available in any form, so customers still using this service are strongly encouraged to look for alternative solutions.
As a reminder to anyone out there still using the URL filtering feature of their Forefront TMG 2010 firewall, the Microsoft Reputation Services (MRS) service, which provides URL categorization for TMG, will no longer be supported after December 31, 2015. After this date, Microsoft will cease updating their URL categorization database. In addition, there are no guarantees from Microsoft that the service will be available in any form, so customers still using this service are strongly encouraged to look for alternative solutions.
For many organizations, this means migrating to another platform entirely, which is not a bad idea considering that TMG is nearly six years old now. Alternatively, it is possible to replace TMG’s web filtering component. This can be done on premises by using integrations from various third-party vendors, or by using a cloud-based solution such as Zscaler.
Regardless which path you take, you have just over one month to identify and implement another URL filtering solution. Good luck!
ISAinfo Forefront TMG 2010 Configuration Reporting Utility
 With the demise of isatools.org a few years ago, many ISA Server and Forefront TMG 2010 administrators have reached out to me to ask where they can find the ISAinfo tool that was previously found on that site. If you’re not familiar with ISAinfo, it was a great utility used for viewing the ISA or TMG configuration by parsing the configuration export. This tool is tremendously useful for providing support, as it includes all of the information required to provide context for troubleshooting. In addition it is an excellent documentation tool.
With the demise of isatools.org a few years ago, many ISA Server and Forefront TMG 2010 administrators have reached out to me to ask where they can find the ISAinfo tool that was previously found on that site. If you’re not familiar with ISAinfo, it was a great utility used for viewing the ISA or TMG configuration by parsing the configuration export. This tool is tremendously useful for providing support, as it includes all of the information required to provide context for troubleshooting. In addition it is an excellent documentation tool.
So, if you’re looking for a reputable location from which to download this tool, look no further. I’ve placed the isainfo.zip file along with the checksums for file verification on my public OneDrive. Enjoy!
ISAinfo.zip – http://1drv.ms/1Q8GOaA
Checksums – http://1drv.ms/1Q8GWqq
Fastvue TMG Reporter 3.0 with Site Clean Now Available
 Just a few months ago I wrote about the beta release of Fastvue’s TMG Reporter v3.0, which includes some compelling new features that TMG firewall administrators are sure to love. Today I’m happy to announce that TMG Reporter 3.0 is now generally available. If you’re still using Forefront TMG 2010 in production, you’ll certainly want to check out the latest features TMG Reporter v3.0 has to offer. Site Clean is sure to impress! Head over to the Fastvue blog for more information.
Just a few months ago I wrote about the beta release of Fastvue’s TMG Reporter v3.0, which includes some compelling new features that TMG firewall administrators are sure to love. Today I’m happy to announce that TMG Reporter 3.0 is now generally available. If you’re still using Forefront TMG 2010 in production, you’ll certainly want to check out the latest features TMG Reporter v3.0 has to offer. Site Clean is sure to impress! Head over to the Fastvue blog for more information.
http://fastvue.co/tmgreporter/blog/fastvue-tmg-reporter-v3-0-out-now/
Fastvue TMG Reporter 3.0 Beta Now Available
 I’m a huge fan of the Fastvue TMG Reporter advanced reporting solution. If you’ve spent any time at all with the native Forefront TMG 2010 reporting tools, you know they are, as my British friends say, “rubbish”. While it is possible to configure Forefront TMG 2010 to log to an external SQL server and create your own reports, a better alternative is to use Fastvue TMG Reporter. They’ve already done all the hard work for you! Also, TMG Reporter from Fastvue works with TMG when configured to use an external SQL server, so you get the best of both worlds!
I’m a huge fan of the Fastvue TMG Reporter advanced reporting solution. If you’ve spent any time at all with the native Forefront TMG 2010 reporting tools, you know they are, as my British friends say, “rubbish”. While it is possible to configure Forefront TMG 2010 to log to an external SQL server and create your own reports, a better alternative is to use Fastvue TMG Reporter. They’ve already done all the hard work for you! Also, TMG Reporter from Fastvue works with TMG when configured to use an external SQL server, so you get the best of both worlds!
Recently the fine folks at Fastvue announced a sneak peak at their latest update to TMG Reporter in v3.0 Beta. This latest release includes a bunch of great new features, including the following:
- Site Clean – This provides a way to clean up a lot of noise from your activity reports by consolidating related requests (e.g. analytics and CDN requests).
- Private Report Sharing – Create a report for an individual or group and prevent them from accessing any other report data.
- AD Security Group Filtering – A must have for searching activity reports!
- Export to CSV for Reports and Report Tables – Great feature for detailed, granular data analysis offline.
- Filter by Firewall Server Name or IP Address – This is essential for enterprise customers managing multiple TMG firewalls across the organization.
The latest release also includes Gantt Bars for Activity Reports, changes to the Productivity Dashboard, inclusion of search terms in User Overview reports, an updated Alerts interface, and improved data visibility. In addition, v3.0 includes memory usage improvements and the usual bug fixes and miscellaneous minor improvements.
Be sure to download Fastvue TMG Report v3.0 Beta today!
Publish DirectAccess with Forefront TMG 2010
DirectAccess is a compelling remote access solution that provides seamless and transparent, always-on, bi-directional remote corporate network connectivity for managed Windows clients. In Windows Server 2008 R2 and Forefront Unified Access Gateway (UAG) 2010, the DirectAccess server had to be configured with two network adapters, with the external network interface configured with two consecutive public IPv4 addresses. Many security engineers were understandably concerned about exposing a domain-joined Windows server directly to the public Internet, which limited the adoption of the technology. Beginning with Windows Server 2012, DirectAccess is integrated in to the operating system and provides more flexible network configuration. DirectAccess can now be deployed behind an existing edge security solution performing NAT, and even supports single-NIC configuration.
The Forefront TMG 2010 firewall is an excellent choice to provide essential protection for the DirectAccess workload. When DirectAccess is deployed behind a NAT device, the only firewall port that needs to be opened is TCP port 443 (HTTPS).
When publishing DirectAccess with TMG, it is important to use a server publishing rule and not a web publishing rule. To publish DirectAccess, open the Forefront TMG 2010 management console, right-click Firewall Policy in the navigation tree, and then choose New Non-Web Server Publishing Rule.
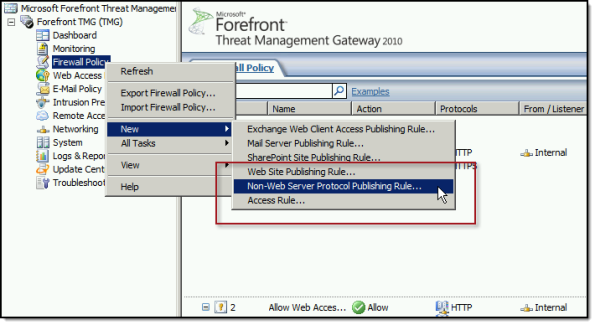
Provide a descriptive name for the rule, enter the IP address of the DirectAccess server, choose HTTPS Server for the protocol, and then select the network interface on which to listen for these requests.
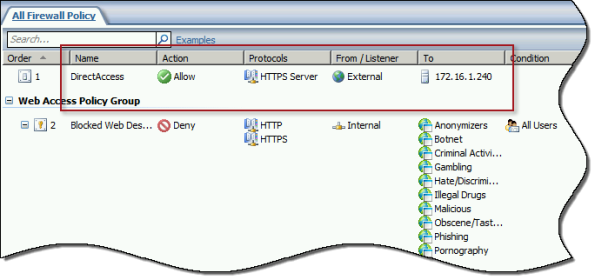
To ensure the proper operation of Receive Side Scaling (RSS) on the DirectAccess server, it is recommended that the server be configured to use TMG as its default gateway and to configure the publishing rule on TMG using the option Requests appear to come from the original client.
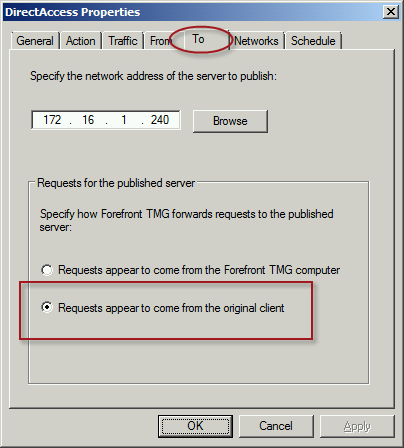
Also, TMG does not support load balancing for server publishing rules, so it is not possible to deliver traffic to multiple back end servers using TMG. For high availability and to provide for scalability, it is recommended to configure load balancing for DirectAccess using NLB or an external load balancer (recommended) and publish the virtual IP address (VIP) using the steps described above.
To learn more about DirectAccess, visit http://directaccess.richardhicks.com/
Forefront TMG 2010 SQL Services Fail to Start After Disabling SSL 3.0
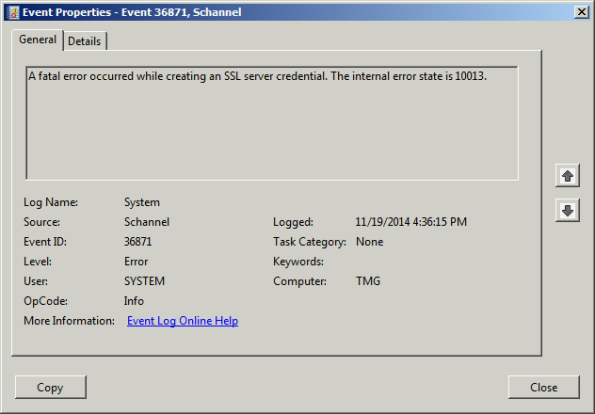
When performing POODLE attack mitigation on the Forefront TMG 2010 firewall by disabling SSL 3.0, you may encounter a scenario in which TMG’s SQL services fail to start after a reboot.

Looking through the Windows system event log you may see an error message logged by the Service Control Manager with event ID 36871 which states:
A fatal error occurred while creating an SSL server credential. The internal error state is 10013.
In addition you may also see an error message logged by the Service Control Manager with event ID 7024 which states:
The SQL Server (ISARS) service terminated with service-specific error %%-2146893007.

This can occur when SSL 3.0 is disabled at the same time that TLS 1.0 is also disabled. Even though TLS 1.1 and 1.2 might be enabled, TMG requires that TLS 1.0 specifically be enabled for SQL server services to function properly when SSL 3.0 is disabled.
To resolve this issue, enable TLS 1.0 Server in the registry by changing the value of Enabled to 1, as shown here. If these registry keys do not exist, create them.

Restart the server for the change to take effect.
Mitigating the POODLE SSL 3 Vulnerability on Forefront TMG 2010
Recently a new and very serious vulnerability in the SSL 3.0 protocol has been discovered that allows an attacker to recover sensitive information for an encrypted session. The Qualys SSL Labs server test has been updated to identify and warn about this issue.
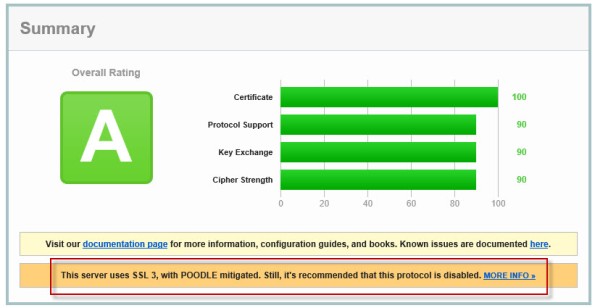
Figure 1 – Qualys SSL Labs Server Test Score for TMG Published Secure Web Site
On a Forefront TMG server with SSL hardening implemented as I’ve outlined here and here, the POODLE attack is mitigated, but it is still recommended that you disable SSL 3.0 altogether. SSL 3.0 is an old, outdated protocol that is no longer widely used, and disabling it should have minimal impact on clients connecting to secure web sites published by the Forefront TMG 2010 firewall.
To disable SSL 3.0 on the TMG firewall, open an elevated PowerShell window and execute the following commands:
New-Item -Path “HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server” -Force
New-ItemProperty -Path “HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server” -PropertyType dword -Value 0 -Name Enabled
Note: Use caution when copying/pasting the above commands as wrapping of the text has occurred.
A restart of the server is required for the change to take effect.
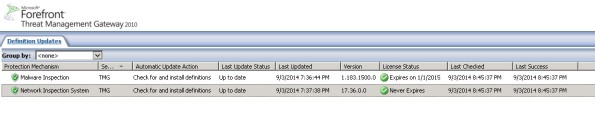
Forefront TMG 2010 Network Inspection System NIS Signature Updates
When Microsoft announced the formal end-of-life for Forefront TMG 2010, they laid out in clear detail the support boundaries for the product going forward. Microsoft stated specifically that they would continue mainstream support for TMG until April of 2015, and extended support would terminate in April 2020. However, the Web Protection Service (WPS) updates for the URL filtering database, antimalware signatures, and the Network Inspection System (NIS) would only continue until December 31, 2015.
Unfortunately, it appears that Microsoft has abandoned the updating for NIS signatures. You may have noticed that a fully updated Forefront TMG firewall with the latest signature updates shows that the last NIS signature was released for security bulletin MS12-050 on July 20, 2012!
I find it difficult to believe that there hasn’t been a single vulnerability discovered or hotfix released since July of 2012 that wouldn’t benefit from NIS protection, so I have to assume that Microsoft is no longer supporting NIS in spite of their pledge to provide support for WPS through the end of 2015. If you are relying on NIS for essential network protection, it’s time to consider deploying a dedicated IDS/IPS solution or another solution that provides this functionality.