PAL v2.3.3 Now with Forefront UAG 2010 Support
Recently the Performance Analysis of Logs (PAL) tool was updated and now includes a threshold file for Forefront UAG 2010. PAL is an essential utility that can make troubleshooting performance issues or capacity planning dramatically easier. I’ve written about using PAL on Forefront TMG 2010 in the past, and using PAL with Forefront UAG 2010 will be very similar. You can download the latest release of PAL at pal.codeplex.com.
Forefront TMG 2010 Replacement Options
Since Microsoft formally announced the end of life for the venerable Forefront TMG 2010 firewall, the most common question I hear is “What should I replace my Forefront TMG firewall with?” It’s an excellent question, and one that I can’t really answer for you definitively. Since Microsoft has elected to leave this space entirely, you’ll obviously be replacing it with a solution from another vendor. But which one? Well, the answer is “it depends”. There are many excellent firewalls, web proxies, and secure web gateways on the market today. So-called “Next Generation Firewalls” are gaining in popularity as well, and provide some interesting capabilities a security administrator can leverage to provide increased protection for their corporate networks. Which one to choose depends on many factors, and will vary greatly depending on your deployment scenario. My suggestion when evaluating potential replacements for your Forefront TMG 2010 firewall is to take a look at your current configuration, review your corporate security policy to determine network security requirements, then begin researching products that include the features you need. If you take a look at the latest Gartner Magic Quadrant for Secure Web Gateways or Next Generation Firewalls and choose a product in the leaders or challengers quadrants you will probably be satisfied. Regardless which solution you choose, demand a proof-of-concept or insist on an evaluation period with which you can return the product for a full refund if it doesn’t meet your needs or expectations. Be open-minded during the process, as you’re not likely to have the comfort level with the new solution as you do with your existing Forefront TMG 2010 firewall. If you are using your Forefront TMG 2010 firewall as a dedicated remote access solution, I would encourage you to look closely at Windows Server 2012 remote access VPN and especially DirectAccess.
Keep in mind that although Microsoft has announced the end of life for Forefront TMG 2010, it will still be supported for many years to come. You will have full feature functionality until the end of 2015, and the product will be supported in some fashion until early 2020 so there’s no need to rush. Perhaps the best replacement for Forefront TMG 2010 hasn’t even been created yet! If you have questions about Forefront TMG 2010 replacements, or you are in the process of evaluating another solution to replace your existing Forefront TMG firewall today, feel free to ask questions or share your experiences by commenting below. Thanks!
Forefront TMG 2010 Configuration Change Tracking Description Quick Tip
Configuration change tracking is an important tool that can be leveraged by Forefront TMG 2010 firewall administrators to audit changes made to the policy and configuration of TMG. This feature originally appeared with ISA 2006 SP1 and was optionally enabled by the administrator. Beginning with Forefront TMG 2010 this feature is now enabled by default. When applying changes made to TMG, the administrator is prompted to enter a description of the change which is included in the change tracking log.
![]()
If you check the box Do not show this prompt again you will, of course, not be prompted to enter descriptions for applied changes in the future. If you later decide you’d like to have this feature back, highlight the Troubleshooting node in the navigation tree and select the Change Tracking tab in the main window. In the Tasks pane click Configure Change Tracking and check the box next to Show prompt for a change description when applying configuration changes.
![]()
Windows 8 Modern UI Apps and Forefront TMG 2010
On a Windows 8 client deployed behind a Forefront TMG 2010 firewall, users may receive the following error when trying to open the Windows Store app.
You’re PC isn’t connected to the Internet. To use the Store, connect to the Internet and then try again.
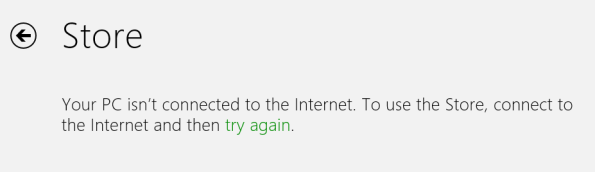
Other Windows 8 “modern UI” applications may experience similar behavior if they require access to resources on the public Internet. However, you are able to access the Internet using both the modern UI and desktop versions of Internet Explorer 10.
The problem occurs when the Forefront TMG 2010 firewall is configured to require authentication on rules controlling access to the Internet over HTTP and HTTPS, or if the option to require all users to authenticate is enabled on the web proxy listener (which isn’t a good idea!). Authenticated web proxy access requires that client be configured either as a web proxy client or as a firewall client. Internet Explorer can be configured as a web proxy client, typically using automatic configuration (WPAD) through DNS or DHCP, but Windows 8 modern UI applications do not inherit Internet Explorer proxy server settings. As such, they behave as SecureNAT clients which do not support authentication. To resolve this issue, run the following command from an elevated command prompt on the Windows 8 client.
netsh winhttp set proxy <tmg_hostname_or_IP_address>:<web_proxy_listener_port>
For example…
netsh winhttp set proxy tmg.richardhicks.net:8080
More information about configuring WINHTTP can be found here.
Another workaround is to install the Forefront TMG 2010 firewall client. This will ensure that all outbound communication through the Forefront TMG firewall is always authenticated.
Microsoft System Center 2012 Endpoint Protection Cookbook
Recently I had the opportunity to review the Microsoft System Center Endpoint Protection Cookbook from PACKT Publishing. The “cookbook” series from PACKT provide clear, concise instruction on how to accomplish various tasks with specific products. Written by Andrew Plue, a System Center veteran and consultant for Certified Security Solutions, this book provides a wealth of valuable information for engineers and administrators seeking to deploy System Center Endpoint Protection (SCEP) in their environments. The timing of this book review was perfect for me, as I was preparing to build out a product demonstration lab and wanted to leverage the endpoint protection components provided by System Center Configuration Manager 2012. Installing SCCM and SCEP is not exactly intuitive, but thankfully the book provided detailed, prescriptive guidance on how to implement, configure, and manage SCEP including a chapter dedicated to building out a SCEP lab environment. If you are considering a migration from Forefront Endpoint Protection (FEP) 2010 or a competing third-party solution, you’ll definitely want to add this reference to your library soon.
Microsoft Most Valuable Professional (MVP) 2012
Once again, I’m happy to announce that I have been awarded the Microsoft Most Valuable Professional (MVP) award for 2012! This is my fourth consecutive year receiving this distinction from Microsoft, and I’m proud to be included with so many great professionals in the program. See you at the MVP summit in February 2013!

Forefront TMG 2010 End of Life Statement
Note: This post updated on 4/22/2015 to reflect current information about the status of the Microsoft Reputation Service (MRS) after December 1, 2015.
Today, Microsoft announced the Forefront TMG 2010 product will be discontinued. Microsoft will continue to provide mainstream support for TMG until April 14, 2015, and extended support until April 14, 2020. The Forefront TMG 2010 Web Protection Services (WPS) will be discontinued on December 31, 2015. Beginning on January 1, 2016, Web Protection Service (URL filtering) will cease to function and the Microsoft Reputation Service (MRS) will be shutdown permanently. Virus and malicious software scanning and the Network Inspection System (NIS) will continue to operate but will no longer receive updates.
The end of life for Forefront TMG 2010 comes as part of sweeping changes made to the entire Forefront protection suite of products. In addition to ending development of Forefront TMG 2010, Microsoft also announced that Forefront Protection for Exchange (FPE), Forefront Protection for SharePoint (FPSP), Forefront Security for OCS (FSOCS), and Forefront Protection Server Management Console (FPSMC) are all being discontinued. Forefront Online Protection for Exchange (FOPE), which has been a part of Office 365, is being renamed Exchange Online Protection.
Looking ahead, Forefront Unified Access Gateway (UAG) 2010 and Forefront Identify Manager (FIM) 2010 R2 both have current roadmaps and will continue to be developed, although it is likely that they will not continue under the Forefront brand name.
Forefront TMG 2010 Protocols and Ports Reference
When deploying Forefront TMG 2010 as a forward or reverse proxy, many organizations will place their TMG firewalls in a perimeter or DMZ network to provide an additional layer of protection for their proxies. When deployed in this manner, configuring perimeter firewalls to allow proper communication to and from the Forefront TMG firewall can be challenging. Although the Service Overview and Network Port Requirements for Windows document on TechNet includes information about ISA server (which also applies to TMG) it includes all protocols and ports used by TMG in all deployment scenarios. This can be confusing when you simply want to allow TMG firewalls in a perimeter network to communicate with an Enterprise Management Server (EMS) on the internal network, or simply manage a TMG firewall in a perimeter network from a management workstation on the internal network. Opening all of the ports listed in the Microsoft KB article mentioned above would be unnecessary and would violate the principle of least privilege, which dictates that only the specific ports required for communication should be opened.
Note: This reference covers typical TMG configurations and may not include all protocols and ports required for every deployment scenario. For example, if you are using RADIUS or RSA for authentication, have configured connectivity verifiers or a remote SQL server, or have deployed Forefront TMG 2010 for Exchange integration, each of these configurations will require additional perimeter firewall access. Also, don’t forget that your perimeter firewalls will need to allow access to the protocols and ports required for the services you are accessing/publishing through Forefront TMG 2010.
For reference, here are the protocols and ports required for specific, common Forefront TMG 2010 deployment scenarios:
EMS to TMG
TCP 135, 10000-65535* – RPC
TCP 3847 – MS Firewall Control
TMG to EMS
TCP 445 – CIFS
UDP 445 – CIFS
TCP 2171 – MS Firewall Storage (domain-joined only)
TCP 2172 – MS Firewall Storage Secure (workgroup mode only)
TCP 3847 – MS Firewall Control
TMG to DCs
Domain joined…
TCP 88 – Kerberos
UDP 88 – Kerberos (send receive)
UDP 123 – NTP
TCP 135, 49152-65535* – RPC
TCP 389 – LDAP
UDP 389 – LDAP
TCP 445 – CIFS
UDP 445 – CIFS
TCP 3268 – LDAP Global Catalog
Non domain-joined…
TCP 389 – LDAP (required only for pre-authentication in reverse proxy scenarios)
TCP 636 – LDAPS (required only for pre-authentication in reverse proxy scenarios)
TMG to DNS
TCP 53 – DNS (send receive)
UDP 53 – DNS
Primary EMS to Replica EMS
TCP 135, 49152-65535* – RPC
TCP 2173 – MS Firewall Storage Replication
Replica EMS to Primary EMS
TCP 135, 49152-65535* – RPC
TCP 445 – CIFS
UDP 445 – CIFS
TCP 2171 – MS Firewall Storage – domain-joined only
TCP 2172 – MS Firewall Storage (Secure) – workgroup mode only
TCP 3847 – MS Firewall Control
Web Proxy Client to TMG
TCP 80 – HTTP (WPAD only)
TCP 8080 – HTTP Proxy
Firewall Client to TMG
TCP 80 – HTTP (WPAD only)
TCP 1745 – Firewall Client Control Channel
UDP 1745 – Firewall Client Control Channel
TCP 1024-65535 – All high ports**
UDP 1024-65535 – All high ports**
Management Workstation to TMG
TCP 135, 10000-65535* – RPC
TCP 2171 – MS Firewall Storage – Domain mode only
TCP 2172 – MS Firewall Storage (Secure) – Workgroup mode only
TCP 3847 – MS Firewall Control
*The default dynamic port range for Windows Server 2008 R2 is 49152-65535. When TMG is installed this setting is changed to 10000-65535. This does not apply to TMG EMS, however. RPC can be configured to use a smaller range of dynamic ports, if necessary. For more information, please see Microsoft KB 154956.
**The Forefront TMG 2010 Firewall Client is designed to operate without a firewall between itself and the TMG firewall. It is highly recommended that you avoid this design whenever possible. If this is unavoidable, all TCP and UDP high ports will have to be opened, as the TMG Firewall Client control channel utilizes random high ports and cannot be restricted as RPC can.
Addressing Security Issues with PPTP VPN in Forefront TMG 2010
At the recent DEFCON hacking conference, security researchers demonstrated a method to crack the MS-CHAPv2 authentication protocol with a 100% success rate. MS-CHAPv2 is used as the default authentication method for remote access VPN in Forefront TMG 2010.
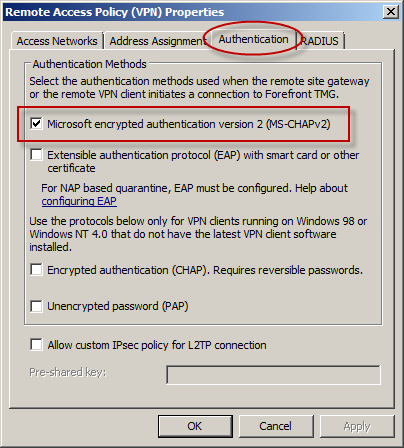
With the public availability of tools to automate the cracking process, PPTP communication using MS-CHAPv2 should be considered unencrypted. There are two options available to mitigate this concern: disable MS-CHAPv2 and enable EAP with PPTP, or disable PPTP and switch to a more secure remote access VPN protocol such as L2TP/IPsec or SSTP. Enabling EAP requires the use of smart cards or certificates for authentication which makes implementation more challenging. SSTP is an excellent option as it leverages SSL/TLS to protect the MS-CHAPv2 authentication process. However, SSTP is only supported on Windows Vista SP1 and later clients. L2TP/IPsec is another good choice, and although it does support certificates it can also be configured using a pre-shared key. If long, complex passwords are used and care is taken to ensure that the password is well protected, it can provide a secure remote access solution.






