Archive
Forefront TMG 2010 Protocols and Ports Reference
When deploying Forefront TMG 2010 as a forward or reverse proxy, many organizations will place their TMG firewalls in a perimeter or DMZ network to provide an additional layer of protection for their proxies. When deployed in this manner, configuring perimeter firewalls to allow proper communication to and from the Forefront TMG firewall can be challenging. Although the Service Overview and Network Port Requirements for Windows document on TechNet includes information about ISA server (which also applies to TMG) it includes all protocols and ports used by TMG in all deployment scenarios. This can be confusing when you simply want to allow TMG firewalls in a perimeter network to communicate with an Enterprise Management Server (EMS) on the internal network, or simply manage a TMG firewall in a perimeter network from a management workstation on the internal network. Opening all of the ports listed in the Microsoft KB article mentioned above would be unnecessary and would violate the principle of least privilege, which dictates that only the specific ports required for communication should be opened.
Note: This reference covers typical TMG configurations and may not include all protocols and ports required for every deployment scenario. For example, if you are using RADIUS or RSA for authentication, have configured connectivity verifiers or a remote SQL server, or have deployed Forefront TMG 2010 for Exchange integration, each of these configurations will require additional perimeter firewall access. Also, don’t forget that your perimeter firewalls will need to allow access to the protocols and ports required for the services you are accessing/publishing through Forefront TMG 2010.
For reference, here are the protocols and ports required for specific, common Forefront TMG 2010 deployment scenarios:
EMS to TMG
TCP 135, 10000-65535* – RPC
TCP 3847 – MS Firewall Control
TMG to EMS
TCP 445 – CIFS
UDP 445 – CIFS
TCP 2171 – MS Firewall Storage (domain-joined only)
TCP 2172 – MS Firewall Storage Secure (workgroup mode only)
TCP 3847 – MS Firewall Control
TMG to DCs
Domain joined…
TCP 88 – Kerberos
UDP 88 – Kerberos (send receive)
UDP 123 – NTP
TCP 135, 49152-65535* – RPC
TCP 389 – LDAP
UDP 389 – LDAP
TCP 445 – CIFS
UDP 445 – CIFS
TCP 3268 – LDAP Global Catalog
Non domain-joined…
TCP 389 – LDAP (required only for pre-authentication in reverse proxy scenarios)
TCP 636 – LDAPS (required only for pre-authentication in reverse proxy scenarios)
TMG to DNS
TCP 53 – DNS (send receive)
UDP 53 – DNS
Primary EMS to Replica EMS
TCP 135, 49152-65535* – RPC
TCP 2173 – MS Firewall Storage Replication
Replica EMS to Primary EMS
TCP 135, 49152-65535* – RPC
TCP 445 – CIFS
UDP 445 – CIFS
TCP 2171 – MS Firewall Storage – domain-joined only
TCP 2172 – MS Firewall Storage (Secure) – workgroup mode only
TCP 3847 – MS Firewall Control
Web Proxy Client to TMG
TCP 80 – HTTP (WPAD only)
TCP 8080 – HTTP Proxy
Firewall Client to TMG
TCP 80 – HTTP (WPAD only)
TCP 1745 – Firewall Client Control Channel
UDP 1745 – Firewall Client Control Channel
TCP 1024-65535 – All high ports**
UDP 1024-65535 – All high ports**
Management Workstation to TMG
TCP 135, 10000-65535* – RPC
TCP 2171 – MS Firewall Storage – Domain mode only
TCP 2172 – MS Firewall Storage (Secure) – Workgroup mode only
TCP 3847 – MS Firewall Control
*The default dynamic port range for Windows Server 2008 R2 is 49152-65535. When TMG is installed this setting is changed to 10000-65535. This does not apply to TMG EMS, however. RPC can be configured to use a smaller range of dynamic ports, if necessary. For more information, please see Microsoft KB 154956.
**The Forefront TMG 2010 Firewall Client is designed to operate without a firewall between itself and the TMG firewall. It is highly recommended that you avoid this design whenever possible. If this is unavoidable, all TCP and UDP high ports will have to be opened, as the TMG Firewall Client control channel utilizes random high ports and cannot be restricted as RPC can.
Addressing Security Issues with PPTP VPN in Forefront TMG 2010
At the recent DEFCON hacking conference, security researchers demonstrated a method to crack the MS-CHAPv2 authentication protocol with a 100% success rate. MS-CHAPv2 is used as the default authentication method for remote access VPN in Forefront TMG 2010.
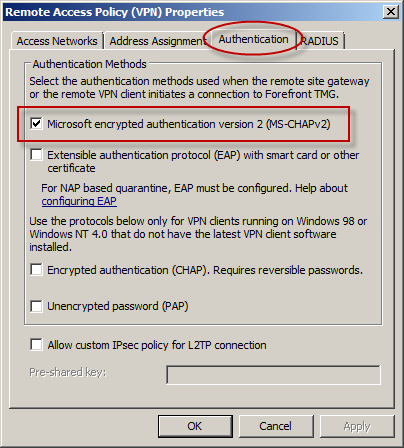
With the public availability of tools to automate the cracking process, PPTP communication using MS-CHAPv2 should be considered unencrypted. There are two options available to mitigate this concern: disable MS-CHAPv2 and enable EAP with PPTP, or disable PPTP and switch to a more secure remote access VPN protocol such as L2TP/IPsec or SSTP. Enabling EAP requires the use of smart cards or certificates for authentication which makes implementation more challenging. SSTP is an excellent option as it leverages SSL/TLS to protect the MS-CHAPv2 authentication process. However, SSTP is only supported on Windows Vista SP1 and later clients. L2TP/IPsec is another good choice, and although it does support certificates it can also be configured using a pre-shared key. If long, complex passwords are used and care is taken to ensure that the password is well protected, it can provide a secure remote access solution.
July 2012 Twitter Outage and Forefront TMG URL Filtering
Earlier today Twitter suffered a serious outage. To further complicate matters, it appears that Microsoft Reputation Services (MRS) is now categorizing twitter.com as a phishing site.


I’m not certain what the reason for this categorization is for, but based on past experience it may have to do with Twitter services running on a shared hosting provider that previously included services that were identified as phishing related. To resolve this issue, open the Forefront TMG management console, highlight the Web Access Policy node in the navigation tree, then click Configure URL Category Overrides in the Tasks pane and move the URL pattern *.twitter.com/ to the Online Communities category.

Forefront TMG 2010 Update Center Quick Tip
The Update Center in the Forefront TMG 2010 management console provides an instant view of the status of signature updates for the Malware Inspection and Network Inspection System (NIS) protection mechanisms. However, the column layout leaves out important information that can be essential when troubleshooting signature update issues. By default, the Last Checked and Last Success columns are hidden from view. To display these details, right-click anywhere in the column headings and then select Add/Remove Columns.
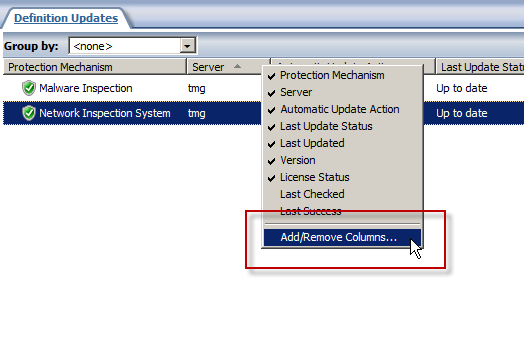
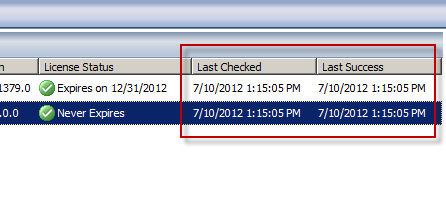
Next, select the Last Checked and Last Success columns and click Add.

Now you’ll see when the Forefront TMG 2010 firewall last checked for updates and when it was last successful.
Disable Logging on System Policy Rules in Forefront TMG 2010
I’ve written a number of articles on improving system performance and logging optimization over the years. As I’ve mentioned previously, this involves the security administrator reviewing each access rule and deciding if the traffic is interesting enough to require logging. If it is not, to improve performance and reduce log pollution it is advisable to disable logging for the access rule in question.

However, when attempting to make this change to a system policy rule you will encounter the following error:
The changes cannot be saved. Error: 0xc0040334 This property cannot be modified for the predefined item. The error occurred on object <policy rule name> of class ‘Policy Rule’ in the scope of array .

Unfortunately the system policy editor provides no facility to make this change in the GUI. To work around this limitation you can use COM to disable logging on system policy rules programmatically using the following script. In this example I’ve chosen to disable logging on the Allow intra-array communication system policy rule.
Option Explicit
Dim Root, Array, Rule
Set Root = CreateObject("FPC.Root")
Set Array = Root.GetContainingArray()
Set Rule = Array.SystemPolicy.PolicyRules.Item("Allow intra-array communication")
Rule.EnableLogging = False
Rule.Save
WScript.Echo “Done!”
Set Rule = Nothing
Set Array = Nothing
Set Root = Nothing
Note: To see this change reflected in the management console, hit F5 to refresh or close and reopen the console.
If you wish to disable logging for all system policy rules, alter the script to use a For Each Next construct as follows:
Set Rules = Array.SystemPolicy.PolicyRules For Each Rule in Rules Rule.EnableLogging = False Next
Forefront TMG and UAG 2010 Presentation at TechEd North America 2012
For those of you who were not able to attend Microsoft TechEd North America 2012 this year, the session I presented entitled “Demystifying Microsoft Forefront Edge Security Solutions: TMG and UAG” is now available online. Enjoy!
Forefront TMG 2010 Guest Blogging for Fastvue
Recently I was given the opportunity to write some guest blog posts about Forefront TMG 2010 for Fastvue. Fastvue develops TMG Reporter, an excellent real-time dashboard, alerting, and reporting tool that integrates with Forefront TMG 2010. Be sure to check out these new articles that have been posted:
Logging Improvements in Forefront TMG 2010
Enterprise Reporting Challenges with Forefront TMG 2010
Tips for Healthy Logging and Reporting in Forefront TMG 2010
Forefront TMG 2010 Enterprise Logging with Remote SQL Server
TMG Reporter is a significant upgrade from the native reporting tools included with Forefront TMG 2010. Download a free evaluation of their software today and give it a try. You won’t be disappointed!
Forefront TMG 2010 Account Lockout Feature for FBA
Consider a scenario in which you have published your Exchange 2010 Outlook Web App servers using Forefront TMG 2010 and are using Active Directory or LDAP authentication along with Forms-based Authentication (FBA). In an effort to gain access to the system, an attacker may perform a brute force password attack by either manual or programmatic means. The attacker will attempt to guess the password for a given user until they reach the configured account lockout threshold as defined in Active Directory. Once this happens, the attacker will have to wait for the password to unlock automatically or be unlocked by an administrator depending on your security policy. Effectively this results in a Denial of Service (DoS) because the legitimate user is unable to authenticate when this happens.
To address this concern, Forefront TMG SP2 includes a feature that allows administrators to enforce an account lockout policy on the Forefront TMG firewall itself. When configured with thresholds lower than those configured in Active Directory, this feature provides valuable protection from DoS that result from unsuccessful password guessing attempts. To enable this feature, install Forefront TMG 2010 SP2, and then follow these detailed instructions.
Controlling Access to File Shares with Forefront TMG 2010
Consider a scenario in which you have an IIS server located in a perimeter network protected by Forefront TMG 2010. The server is published to the Internet and is used to display product information for your company. Web content developers on your internal network need to have access to file shares on the IIS server to upload new web content. To facilitate this access you create an access rule to allow CIFS access to the IIS server. For security reasons you decide to restrict access to members of the Web Content Developers domain group. In addition, your workstations have the Forefront TMG Firewall Client installed. The access rule looks like this:
When users attempt to map a drive to the file share on the web server they receive the following error message:
System error 67 has occurred. The network name cannot be found.
In addition, the Forefront TMG 2010 firewall log indicates the following:
Denied Connection Log Type: Firewall Service Status: The action cannot be performed because the session is not authenticated.

At this point you might be puzzled because you have the Forefront TMG Firewall Client is installed on the workstation. TMG Firewall Client communication is always authenticated, so why does the firewall log indicate otherwise? The answer is simple. The Forefront TMG 2010 Firewall Client is a Layered Service Provider (LSP) that listens for Winsock calls made by the operating system and applications. Any Winsock calls made for resources on a remote network will be transparently delivered to the proxy server by the Firewall Client. However, CIFS communication does not use Winsock, so the TMG Firewall Client does not handle this traffic. As such, the network requests are delivered to the Forefront TMG firewall as SecureNAT requests. Since the rule in question requires authentication, and SecureNAT traffic cannot be authenticated, the firewall appropriately denies the traffic and the request fails.
You can resolve this issue by removing authentication on the access rule and controlling access on the file share itself. If you want to enforce user and group authentication at the firewall, consider using another protocol such as FTP.
For more information about the Forefront TMG 2010 Firewall Client and CIFS connections, please review Microsoft Knowledge Base article 913782.








