Archive
Addressing Security Issues with PPTP VPN in Forefront TMG 2010
At the recent DEFCON hacking conference, security researchers demonstrated a method to crack the MS-CHAPv2 authentication protocol with a 100% success rate. MS-CHAPv2 is used as the default authentication method for remote access VPN in Forefront TMG 2010.
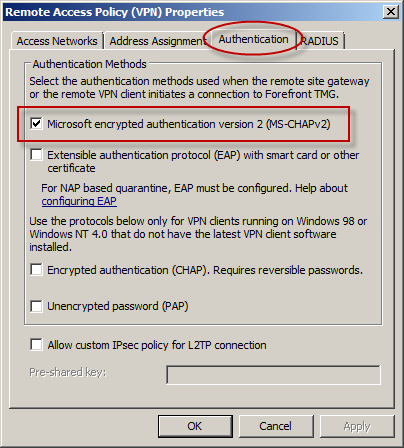
With the public availability of tools to automate the cracking process, PPTP communication using MS-CHAPv2 should be considered unencrypted. There are two options available to mitigate this concern: disable MS-CHAPv2 and enable EAP with PPTP, or disable PPTP and switch to a more secure remote access VPN protocol such as L2TP/IPsec or SSTP. Enabling EAP requires the use of smart cards or certificates for authentication which makes implementation more challenging. SSTP is an excellent option as it leverages SSL/TLS to protect the MS-CHAPv2 authentication process. However, SSTP is only supported on Windows Vista SP1 and later clients. L2TP/IPsec is another good choice, and although it does support certificates it can also be configured using a pre-shared key. If long, complex passwords are used and care is taken to ensure that the password is well protected, it can provide a secure remote access solution.
Forefront TMG 2010 Update Center Quick Tip
The Update Center in the Forefront TMG 2010 management console provides an instant view of the status of signature updates for the Malware Inspection and Network Inspection System (NIS) protection mechanisms. However, the column layout leaves out important information that can be essential when troubleshooting signature update issues. By default, the Last Checked and Last Success columns are hidden from view. To display these details, right-click anywhere in the column headings and then select Add/Remove Columns.
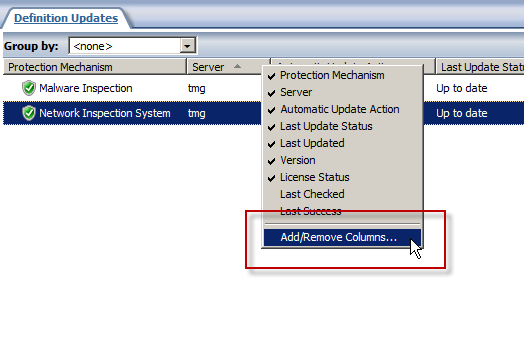
Next, select the Last Checked and Last Success columns and click Add.

Now you’ll see when the Forefront TMG 2010 firewall last checked for updates and when it was last successful.
Disable Logging on System Policy Rules in Forefront TMG 2010
I’ve written a number of articles on improving system performance and logging optimization over the years. As I’ve mentioned previously, this involves the security administrator reviewing each access rule and deciding if the traffic is interesting enough to require logging. If it is not, to improve performance and reduce log pollution it is advisable to disable logging for the access rule in question.

However, when attempting to make this change to a system policy rule you will encounter the following error:
The changes cannot be saved. Error: 0xc0040334 This property cannot be modified for the predefined item. The error occurred on object <policy rule name> of class ‘Policy Rule’ in the scope of array .

Unfortunately the system policy editor provides no facility to make this change in the GUI. To work around this limitation you can use COM to disable logging on system policy rules programmatically using the following script. In this example I’ve chosen to disable logging on the Allow intra-array communication system policy rule.
Option Explicit
Dim Root, Array, Rule
Set Root = CreateObject("FPC.Root")
Set Array = Root.GetContainingArray()
Set Rule = Array.SystemPolicy.PolicyRules.Item("Allow intra-array communication")
Rule.EnableLogging = False
Rule.Save
WScript.Echo “Done!”
Set Rule = Nothing
Set Array = Nothing
Set Root = Nothing
Note: To see this change reflected in the management console, hit F5 to refresh or close and reopen the console.
If you wish to disable logging for all system policy rules, alter the script to use a For Each Next construct as follows:
Set Rules = Array.SystemPolicy.PolicyRules For Each Rule in Rules Rule.EnableLogging = False Next
Forefront TMG 2010 Guest Blogging for Fastvue
Recently I was given the opportunity to write some guest blog posts about Forefront TMG 2010 for Fastvue. Fastvue develops TMG Reporter, an excellent real-time dashboard, alerting, and reporting tool that integrates with Forefront TMG 2010. Be sure to check out these new articles that have been posted:
Logging Improvements in Forefront TMG 2010
Enterprise Reporting Challenges with Forefront TMG 2010
Tips for Healthy Logging and Reporting in Forefront TMG 2010
Forefront TMG 2010 Enterprise Logging with Remote SQL Server
TMG Reporter is a significant upgrade from the native reporting tools included with Forefront TMG 2010. Download a free evaluation of their software today and give it a try. You won’t be disappointed!
Forefront TMG 2010 Account Lockout Feature for FBA
Consider a scenario in which you have published your Exchange 2010 Outlook Web App servers using Forefront TMG 2010 and are using Active Directory or LDAP authentication along with Forms-based Authentication (FBA). In an effort to gain access to the system, an attacker may perform a brute force password attack by either manual or programmatic means. The attacker will attempt to guess the password for a given user until they reach the configured account lockout threshold as defined in Active Directory. Once this happens, the attacker will have to wait for the password to unlock automatically or be unlocked by an administrator depending on your security policy. Effectively this results in a Denial of Service (DoS) because the legitimate user is unable to authenticate when this happens.
To address this concern, Forefront TMG SP2 includes a feature that allows administrators to enforce an account lockout policy on the Forefront TMG firewall itself. When configured with thresholds lower than those configured in Active Directory, this feature provides valuable protection from DoS that result from unsuccessful password guessing attempts. To enable this feature, install Forefront TMG 2010 SP2, and then follow these detailed instructions.
Controlling Access to File Shares with Forefront TMG 2010
Consider a scenario in which you have an IIS server located in a perimeter network protected by Forefront TMG 2010. The server is published to the Internet and is used to display product information for your company. Web content developers on your internal network need to have access to file shares on the IIS server to upload new web content. To facilitate this access you create an access rule to allow CIFS access to the IIS server. For security reasons you decide to restrict access to members of the Web Content Developers domain group. In addition, your workstations have the Forefront TMG Firewall Client installed. The access rule looks like this:
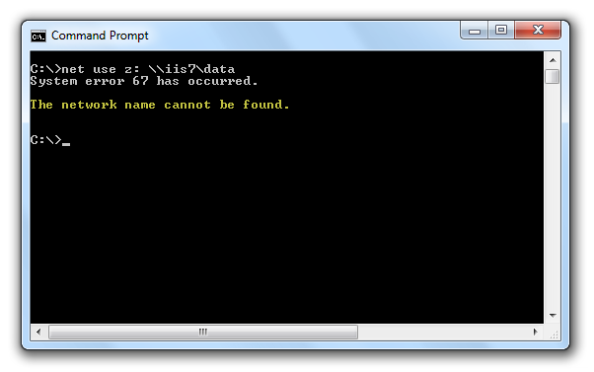
When users attempt to map a drive to the file share on the web server they receive the following error message:
System error 67 has occurred. The network name cannot be found.
In addition, the Forefront TMG 2010 firewall log indicates the following:
Denied Connection Log Type: Firewall Service Status: The action cannot be performed because the session is not authenticated.

At this point you might be puzzled because you have the Forefront TMG Firewall Client is installed on the workstation. TMG Firewall Client communication is always authenticated, so why does the firewall log indicate otherwise? The answer is simple. The Forefront TMG 2010 Firewall Client is a Layered Service Provider (LSP) that listens for Winsock calls made by the operating system and applications. Any Winsock calls made for resources on a remote network will be transparently delivered to the proxy server by the Firewall Client. However, CIFS communication does not use Winsock, so the TMG Firewall Client does not handle this traffic. As such, the network requests are delivered to the Forefront TMG firewall as SecureNAT requests. Since the rule in question requires authentication, and SecureNAT traffic cannot be authenticated, the firewall appropriately denies the traffic and the request fails.
You can resolve this issue by removing authentication on the access rule and controlling access on the file share itself. If you want to enforce user and group authentication at the firewall, consider using another protocol such as FTP.
For more information about the Forefront TMG 2010 Firewall Client and CIFS connections, please review Microsoft Knowledge Base article 913782.
IP Spoofing Alert from APIPA Address in Forefront TMG 2010
Security administrators may encounter the following IP spoofing alert on their Forefront TMG 2010 firewall:
Alert: IP Spoofing Description: Forefront TMG 2010 detected a possible spoof attack from the IP address 169.254.x.x. A spoof attack occurs when an IP address that is not reachable through the network adapter on which the packet was received. If logging for dropped packets is enabled, you can view the details of this attack in the firewall log in Forefront TMG 2010 log viewer. If the IP address belongs to a VPN client, this event may be ignored.

This alert occurs because the Forefront TMG 2010 firewall received a packet on its internal network interface from a client (server, workstation, or other host) that did not have a statically assigned IP address and was not able to obtain one from DHCP, so the client selected an IP address from the Automatic Private IP Address Assignment (APIPA) address range defined in RFC 3927.
You can safely ignore this alert, or you can resolve the issue by adding the APIPA reserved network 169.254.0.0/16 to the Internal network definition. This can be accomplished by opening the Forefront TMG 2010 management console and highlighting the Networking node in the navigation tree, then right-clicking the Internal network, selecting the Addresses tab, then clicking the Add Private button and choosing the address range 169.254.0.0 – 169.254.255.255.

Note: It is possible to resolve this issue by disabling alerts for IP spoofing attempts. However, this is considered bad security practice and is strongly discouraged.
You may recall from an earlier blog post I indicated that the best way to configure the Internal network definition in Forefront TMG 2010 is to choose the Add Adapter option. This still remains true. However, this is one of those rare cases in which you’ll want add an additional network address space to your Internal network definition to reduce the volume of IP spoofing alerts being raised by the Forefront TMG 2010 firewall.
The one side effect to implementing this change is that you will now receive a Configuration error alert informing you that your Internal network does not correlate with the network adapters that belong to it.
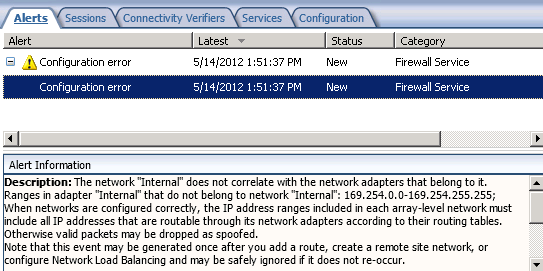
Essentially you have traded one annoying alert for another. However, the noise generated by IP spoofing alerts from clients with APIPA IP addresses might make this tradeoff worthwhile. In addition, it is much safer to disable the configuration error alert than it is the IP spoofing alert.
TechDays San Francisco 2012
TechDays San Francisco 2012, sponsored by the Pacific IT Professionals user group, is a two day IT professional conference being held on March 23 and 24, 2012. The event features a lineup of speakers that includes Chris Avis, CA Callahan, Jennelle Crothers, Jessica DeVita, Steve Evans, Jason C. Helmick, Chris Henley, Ed Horley, Darren Mar-Elia, Mark Minasi, Stephen Rose, Joey Snow, Doug Spindler, Mark Vinkour, Harold Wong, and Chris Zwergel. Sessions will cover topics such as Azure and cloud, Clustering, DNS/DHCP/IPAM, Exchange, Hyper-V, IIS, Lync, MDOP, networking and VPN, Powershell, SharePoint, System Center, VDI, Windows 8 Client and Server, and Windows Phone 7. I will be presenting sessions on Forefront Edge Security (Forefront TMG 2010 and UAG 2010) as well as DirectAccess. Visit the TechDaysSF web site for the full speaker lineup and session abstracts, then click here to register for the event. Hope to see you there!
WPAD Considerations for Kerberos Authentication with NLB VIP on Forefront TMG 2010
As I outlined in a recent article on ISAserver.org, Service Pack 2 (SP2) for Forefront TMG 2010 supports Kerberos authentication in load-balanced scenarios when web proxy clients are configured to use the virtual IP address (VIP) of the array. However, using Web Proxy Automatic Discovery (WPAD) with either DNS or DHCP poses a challenge for organizations that choose to take advantage of this new feature. When using WPAD, the web proxy client retrieves the automatic configuration script from the Forefront TMG firewall. The script provides the web proxy client with the IP addresses (or hostnames, if configured) of the individual array members. In this configuration, the web proxy client will send its request to one of the array members returned by function MakeProxies() and not to the VIP, as desired.
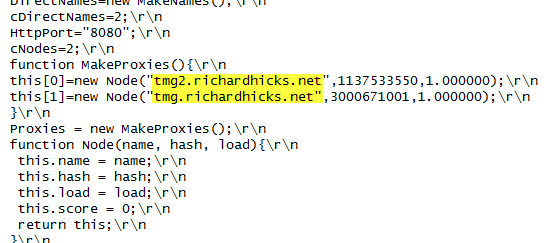
To work around this issue you can configure a separate web server to host the automatic configuration script. You can use any web server you wish, just make sure that it is highly available and don’t forget to configure the MIME type application/x-ns-proxy-autoconfig for the file extension you choose (typically .DAT or .PAC). Full details about how to do this can be found here. You can create your own Proxy Automatic Configuration (PAC) file from scratch, or you can simply retrieve the automatic configuration script from TMG, modify it to use the IP address (or preferably the hostname or FQDN) of the Forefront TMG array’s VIP, and place that on the web server for clients to retrieve. This means that the automatic configuration script will have to be updated manually, as required. This could be automated by writing a script that periodically retrieves the automatic configuration script from the Forefront TMG firewall, modifies it appropriately, and then saves it on the web server if you were really clever! Another alternative is to configure the Forefront TMG 2010 firewall to return a customized automatic configuration script. You can find details about this configuration here.
ESET Gateway Security Beta for Forefront TMG 2010
For security administrators looking to improve upon Forefront TMG 2010’s already strong advanced web protection features, leading anti-virus vendor ESET recently announced the beta availability of its Gateway Security for Forefront TMG 2010 software. ESET Gateway Security for Forefront TMG delivers advanced, gateway-integrated virus and malicious software scanning to provide comprehensive protection for web-based protocols like HTTP and FTP. ESET Gateway Security for Forefront TMG also supports SMTP, IMAP, and POP3 protocols to provide anti-malware and anti-spam capabilities for added protection. In addition, ESET Gateway Security for Forefront TMG 2010 includes host-based security for the TMG firewall’s underlying operating system, as well as automatic file exclusion configuration to ensure compatibility with Forefront TMG. ESET Gateway Security for Forefront TMG 2010 is fully compatible with existing ESET centralized management tools and supports Microsoft ISA Server 2006. Download the beta today!









